Navigating the Path to CyberPeace: Insights and Strategies
Featured Blogs

Executive Summary:
A video showing a peacock allegedly trapped in ice has been going viral on social media. In the clip, the peacock appears to be frozen in a snow-covered area. Moments later, a man is seen approaching with a hammer and breaking the ice to rescue the bird. Social media users are sharing the video as a real-life incident, praising the peacock’s resilience and describing the scene as inspiring. However, CyberPeace research found the viral claim to be misleading. Our research revealed that the video was created using Artificial Intelligence (AI) and is being falsely circulated as a real incident.
Claim:
Facebook user ‘Ras Bihari Pathak’ shared the viral video on January 25, 2026, with the caption: “This peacock is not standing on ice, but on courage. It reminds us that no matter how harsh the circumstances are, hope always returns in colours.” The archived version of the post can be accessed here.

Fact Check:
To verify the claim, we first conducted a keyword search on Google to check whether any such real incident involving a peacock trapped in ice had been reported. However, no credible or verified media reports were found. Next, we closely examined the viral video. Upon observation, the peacock’s movements and reactions appeared unnatural and artificial. The motion lacked realistic physical behaviour, raising suspicion that the video might have been digitally generated. To confirm this, we analysed the clip using the AI video detection tool Hive Moderation, which indicated a 99 per cent or higher likelihood that the video was AI-generated.
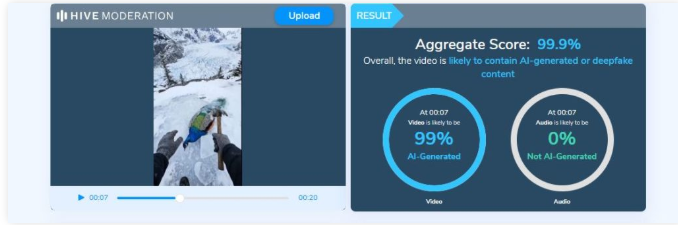
Conclusion:
CyberPeace research confirms that the viral video showing a peacock allegedly trapped in ice is not real. The clip has been created using Artificial Intelligence and is being shared on social media with a false and misleading claim.

Executive Summary
A video featuring Uttar Pradesh Chief Minister Yogi Adityanath is being widely shared on social media. In the video, Adityanath can be heard saying, “Let me become the Prime Minister, and Pakistan-occupied Kashmir will also become a part of India.” The video also carries an on-screen text that reads “Next PM 2029.” By sharing this clip, social media users are claiming that Yogi Adityanath is set to become India’s Prime Minister in 2029.
However, CyberPeace research found the viral claim to be misleading. Our research revealed that the video circulating online has been edited and is being shared out of context. The original video dates back to May 2024. In the original footage, Yogi Adityanath is not speaking about himself. Instead, he is referring to Prime Minister Narendra Modi.
In the original statement, Adityanath says:
“Let Modi ji become Prime Minister for the third time, and within the next six months, Pakistan-occupied Kashmir will also become a part of India.”
It is evident that the video has been trimmed and misleading text has been added to falsely portray the statement as a declaration about Yogi Adityanath becoming Prime Minister in 2029.
Claim
A YouTube user shared the viral video on January 29, 2026, claiming that Yogi Adityanath said, “Let me become Prime Minister, and Pakistan-occupied Kashmir will be part of India.” The video carries the caption “Next PM 2029,” suggesting that Adityanath is set to become the Prime Minister in 2029.
Link to the post n archive

Fact Check:
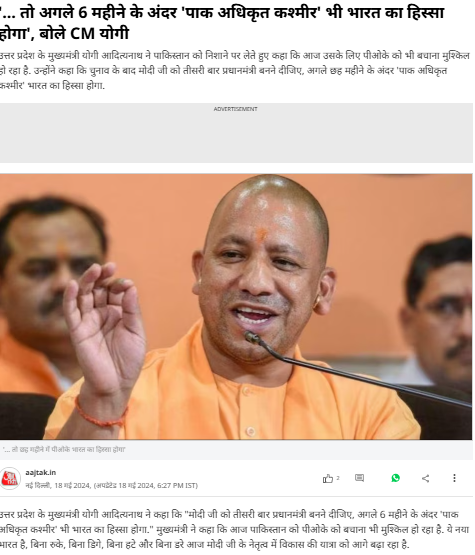
To verify the viral claim, we first conducted a keyword search on Google. During this process, we found a report published by Aaj Tak on May 18, 2024. According to the report, Yogi Adityanath stated that if Narendra Modi becomes Prime Minister for the third time, Pakistan-occupied Kashmir would become part of India within six months.
Report link:
Next, we extracted keyframes from the viral video and ran them through Google Lens. This led us to the official YouTube channel of Yogi Adityanath, where the same video was uploaded on May 18, 2024.
Original video link:
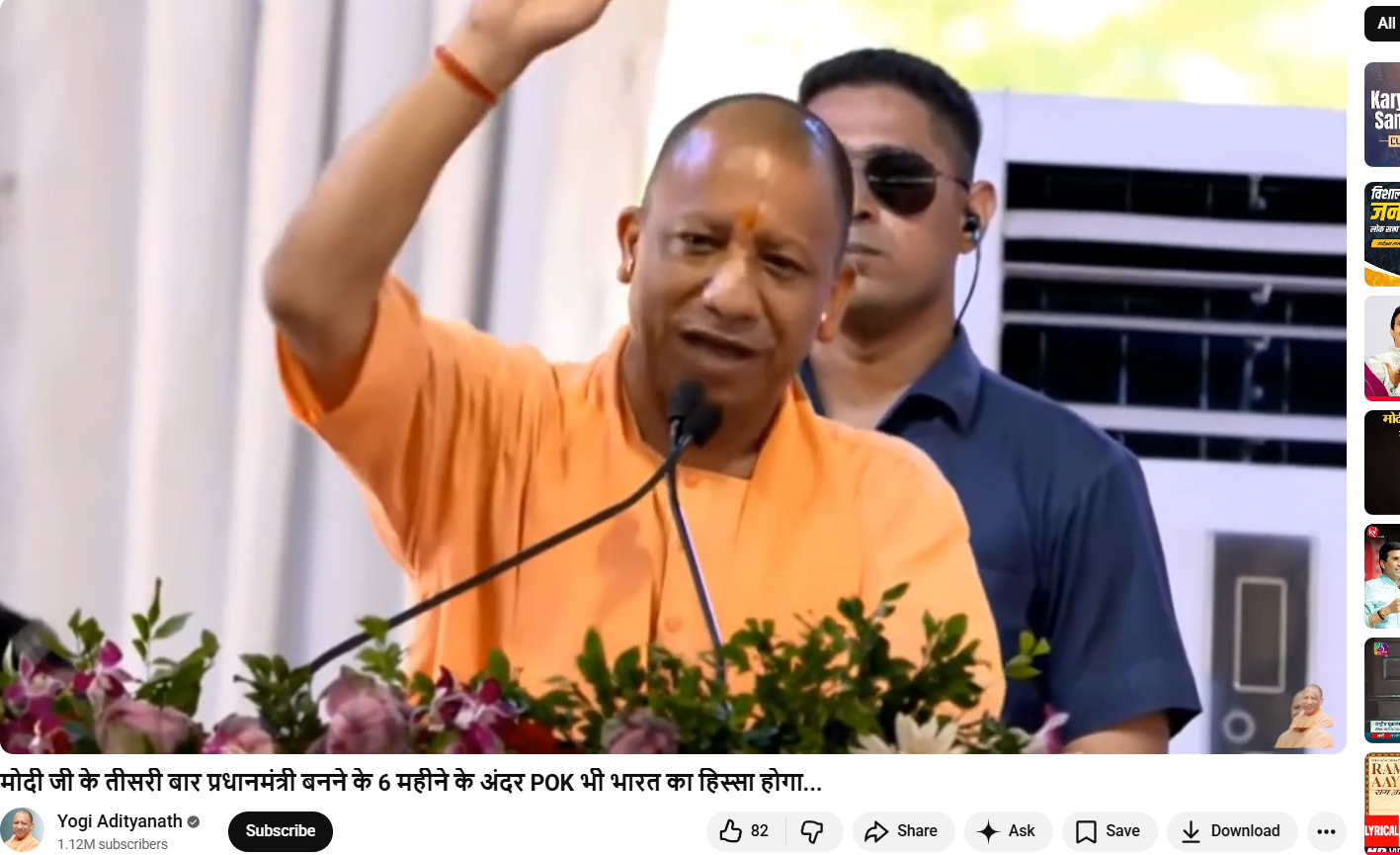
In the original video, Yogi Adityanath clearly makes the statement in reference to Prime Minister Narendra Modi, not himself.Finally, we compared the viral clip with the original footage. The visuals in both videos are identical; however, the viral version has been edited and overlaid with misleading text to change the meaning of the statement.
Conclusion
Our research confirms that the viral video is edited and misleading. The original video is from May 2024, in which Yogi Adityanath was speaking about Prime Minister Narendra Modi, not about himself becoming Prime Minister in 2029. The video has been falsely altered and shared with a deceptive claim on social media.

Executive Summary:
A video showing a peacock allegedly trapped in ice has been going viral on social media. In the clip, the peacock appears to be frozen in a snow-covered area. Moments later, a man is seen approaching with a hammer and breaking the ice to rescue the bird. Social media users are sharing the video as a real-life incident, praising the peacock’s resilience and describing the scene as inspiring. However, CyberPeace research found the viral claim to be misleading. Our research revealed that the video was created using Artificial Intelligence (AI) and is being falsely circulated as a real incident.
Claim:
Facebook user ‘Ras Bihari Pathak’ shared the viral video on January 25, 2026, with the caption: “This peacock is not standing on ice, but on courage. It reminds us that no matter how harsh the circumstances are, hope always returns in colours.” The archived version of the post can be accessed here.

Fact Check:
To verify the claim, we first conducted a keyword search on Google to check whether any such real incident involving a peacock trapped in ice had been reported. However, no credible or verified media reports were found. Next, we closely examined the viral video. Upon observation, the peacock’s movements and reactions appeared unnatural and artificial. The motion lacked realistic physical behaviour, raising suspicion that the video might have been digitally generated. To confirm this, we analysed the clip using the AI video detection tool Hive Moderation, which indicated a 99 per cent or higher likelihood that the video was AI-generated.

Conclusion:
CyberPeace research confirms that the viral video showing a peacock allegedly trapped in ice is not real. The clip has been created using Artificial Intelligence and is being shared on social media with a false and misleading claim.

Executive Summary
A video featuring Uttar Pradesh Chief Minister Yogi Adityanath is being widely shared on social media. In the video, Adityanath can be heard saying, “Let me become the Prime Minister, and Pakistan-occupied Kashmir will also become a part of India.” The video also carries an on-screen text that reads “Next PM 2029.” By sharing this clip, social media users are claiming that Yogi Adityanath is set to become India’s Prime Minister in 2029.
However, CyberPeace research found the viral claim to be misleading. Our research revealed that the video circulating online has been edited and is being shared out of context. The original video dates back to May 2024. In the original footage, Yogi Adityanath is not speaking about himself. Instead, he is referring to Prime Minister Narendra Modi.
In the original statement, Adityanath says:
“Let Modi ji become Prime Minister for the third time, and within the next six months, Pakistan-occupied Kashmir will also become a part of India.”
It is evident that the video has been trimmed and misleading text has been added to falsely portray the statement as a declaration about Yogi Adityanath becoming Prime Minister in 2029.
Claim
A YouTube user shared the viral video on January 29, 2026, claiming that Yogi Adityanath said, “Let me become Prime Minister, and Pakistan-occupied Kashmir will be part of India.” The video carries the caption “Next PM 2029,” suggesting that Adityanath is set to become the Prime Minister in 2029.
Link to the post n archive

Fact Check:
To verify the viral claim, we first conducted a keyword search on Google. During this process, we found a report published by Aaj Tak on May 18, 2024. According to the report, Yogi Adityanath stated that if Narendra Modi becomes Prime Minister for the third time, Pakistan-occupied Kashmir would become part of India within six months.
Report link:

Next, we extracted keyframes from the viral video and ran them through Google Lens. This led us to the official YouTube channel of Yogi Adityanath, where the same video was uploaded on May 18, 2024.
Original video link:

In the original video, Yogi Adityanath clearly makes the statement in reference to Prime Minister Narendra Modi, not himself.Finally, we compared the viral clip with the original footage. The visuals in both videos are identical; however, the viral version has been edited and overlaid with misleading text to change the meaning of the statement.
Conclusion
Our research confirms that the viral video is edited and misleading. The original video is from May 2024, in which Yogi Adityanath was speaking about Prime Minister Narendra Modi, not about himself becoming Prime Minister in 2029. The video has been falsely altered and shared with a deceptive claim on social media.

Executive Summary
As India concluded its 77th Republic Day celebrations on January 26, 2026, with grandeur and patriotic enthusiasm along the iconic Kartavya Path, a video began circulating on social media claiming to show Indian security personnel failing to perform motorcycle stunts during the ceremonial parade. The short clip allegedly depicts soldiers attempting high-risk, synchronised motorcycle manoeuvres, only to lose balance and fall off their bikes. The visuals were widely shared online with mocking captions, suggesting incompetence during a nationally televised event. However, an research by the CyberPeace found that the video is not authentic and was digitally generated using artificial intelligence.
Claim
A Pakistan-based X user, Sadaf Baloch (@sadafzbaloch), shared the video on January 27, claiming it showed Indian security personnel failing to execute motorcycle stunts during the Republic Day parade held on January 26, 2026. While sharing the clip, the user wrote:“Every time the Indian Army tries a tactical stunt, it looks less like combat training and more like a low-budget circus trailer filmed in one take.”The post was widely circulated with similar narratives questioning the professionalism of Indian forces.
Here is the link and archive link to the post, along with a screenshot.

To verify the authenticity of the viral video, the Desk conducted a detailed frame-by-frame analysis. During the examination, a watermark linked to ‘Sora’—an AI text-to-video generation model was detected at the 00:05 timestamp. The presence of this watermark strongly indicated that the video was artificially generated and not recorded during a real-world event.

Fact Check:
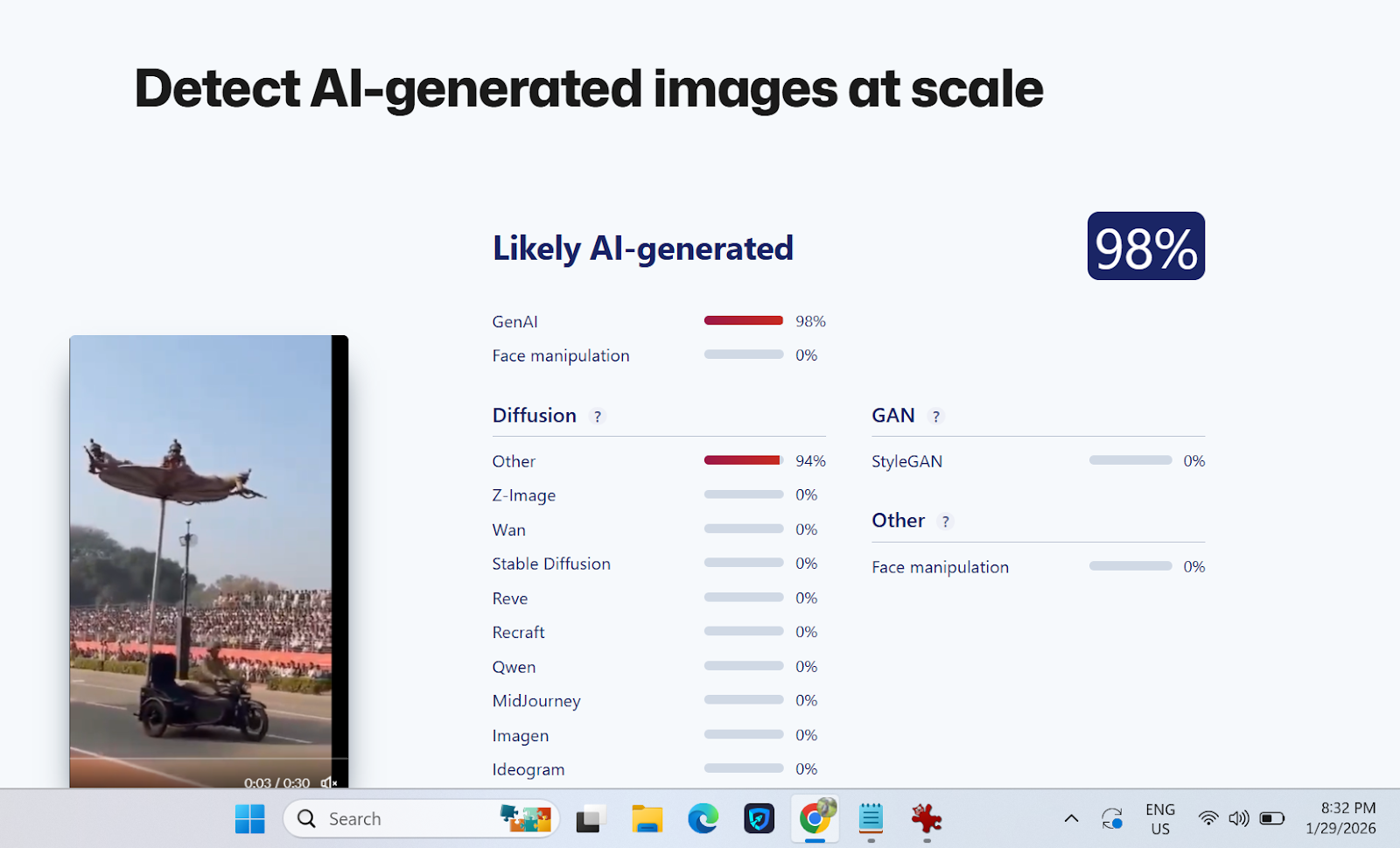
Further visual scrutiny revealed several inconsistencies commonly associated with AI-generated content. The background appeared unnatural and lacked realistic depth, while the movements and reactions of the security personnel looked mechanically exaggerated and inconsistent with real physics. Facial expressions and body motions during the alleged falls also appeared unrealistic. To strengthen the verification, the Desk analysed the clip using Sightengine, an AI-detection tool. The results showed a 98 per cent probability that the video contained AI-generated or deepfake elements.
Below is a screenshot of the result.
As part of the research , the Desk also conducted a customised keyword search and reviewed official coverage of the Republic Day parade. A full-length video broadcast by DD News on its official YouTube channel was examined. The footage showed joint CRPF and SSB motorcycle teams performing traditional daredevil stunts without any mishap. No incident resembling the viral claim was found in the official broadcast or in any credible media reports.
Here is the video link and a screenshot.
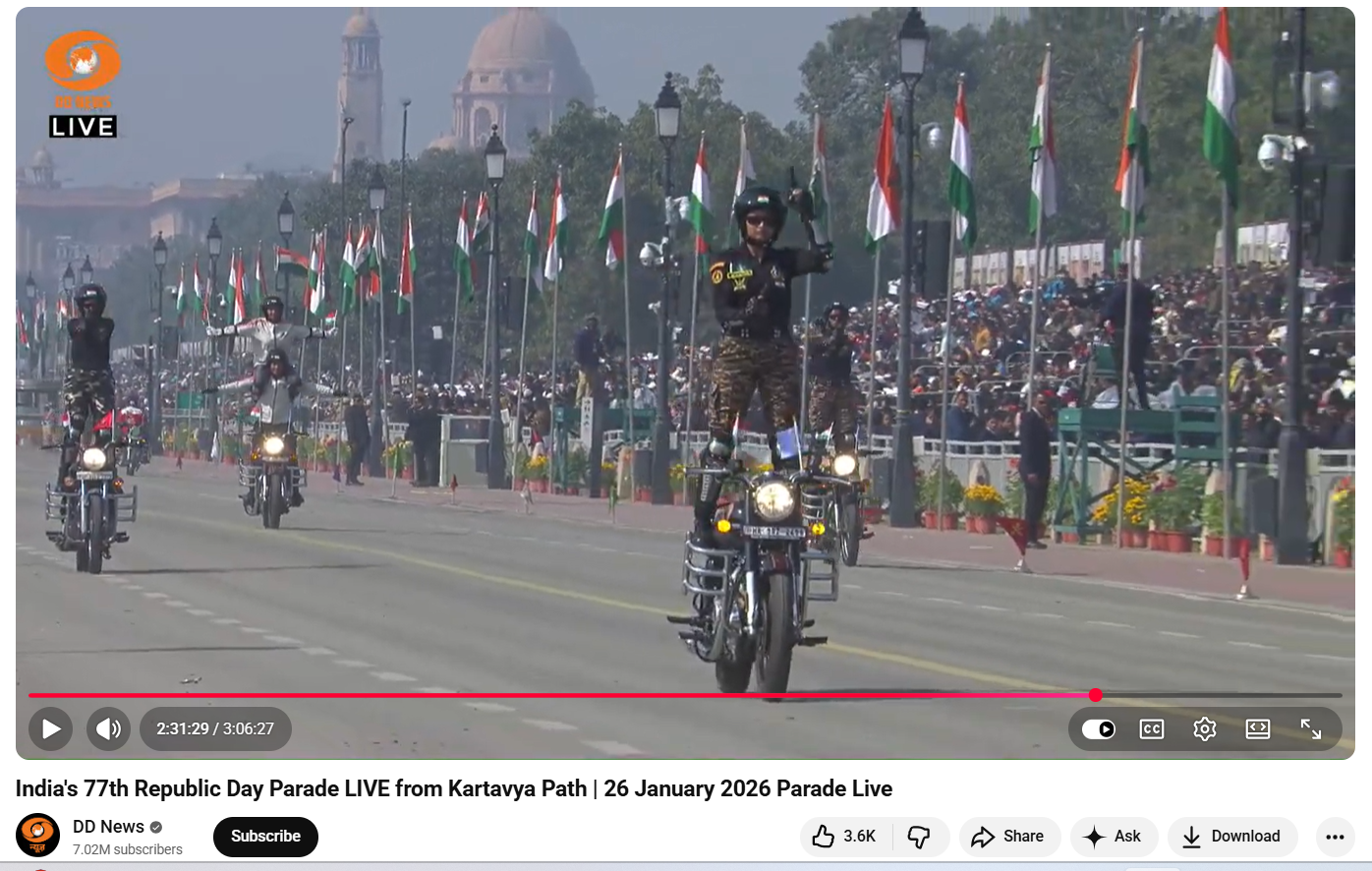
Conclusion
The CyberPeace research confirms that the viral video purportedly showing Indian security personnel failing to perform motorcycle stunts during the 77th Republic Day parade is AI-generated. The clip has been falsely circulated online as genuine content with the intent to mislead viewers and spread misinformation.

Executive Summary:
A video claiming to show the plane crash that allegedly killed Maharashtra Deputy Chief Minister Ajit Pawar has been widely circulated on social media. The circulation began soon after reports emerged of a tragic aircraft accident in Baramati, Maharashtra, on January 28, 2026, in which Ajit Pawar and five others were reported to have died. The viral video shows a plane crashing to the ground moments after take-off. Social media users have claimed that the footage captures the exact incident in which Ajit Pawar was on board. However, an research by the CyberPeacehas found that this claim is false.
Claim:
An Instagram user shared the video on January 28, 2026, claiming that it showed the plane crash in Maharashtra in which Deputy Chief Minister Ajit Pawar and others allegedly lost their lives. The caption accompanying the video read:“This morning, Deputy CM Ajit Pawar and six others tragically died in a plane crash in Maharashtra.”
Links to the post and its archived version are provided below.
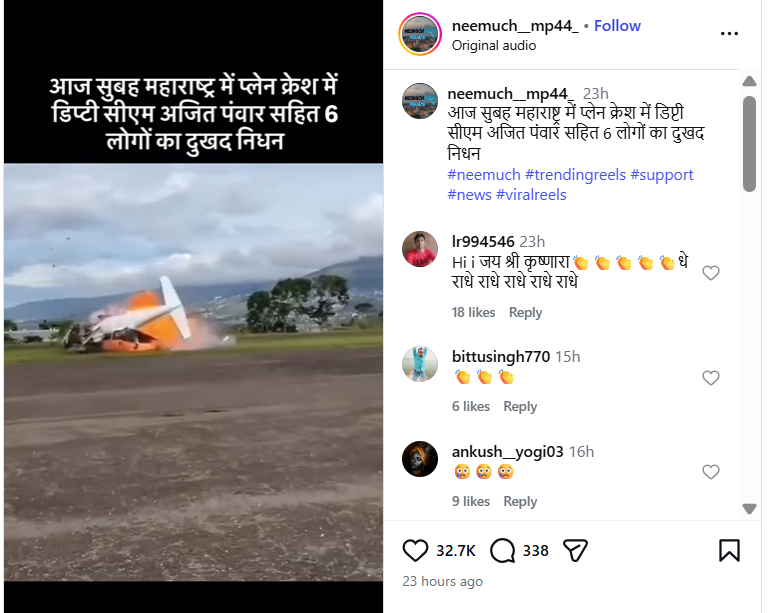
Fact Check:
To verify the authenticity of the viral video, the CyberPeaceconducted a reverse image search of its keyframes. During this process, the same visuals were found in a video report uploaded on News9 Live’s official YouTube channel on October 23, 2025.
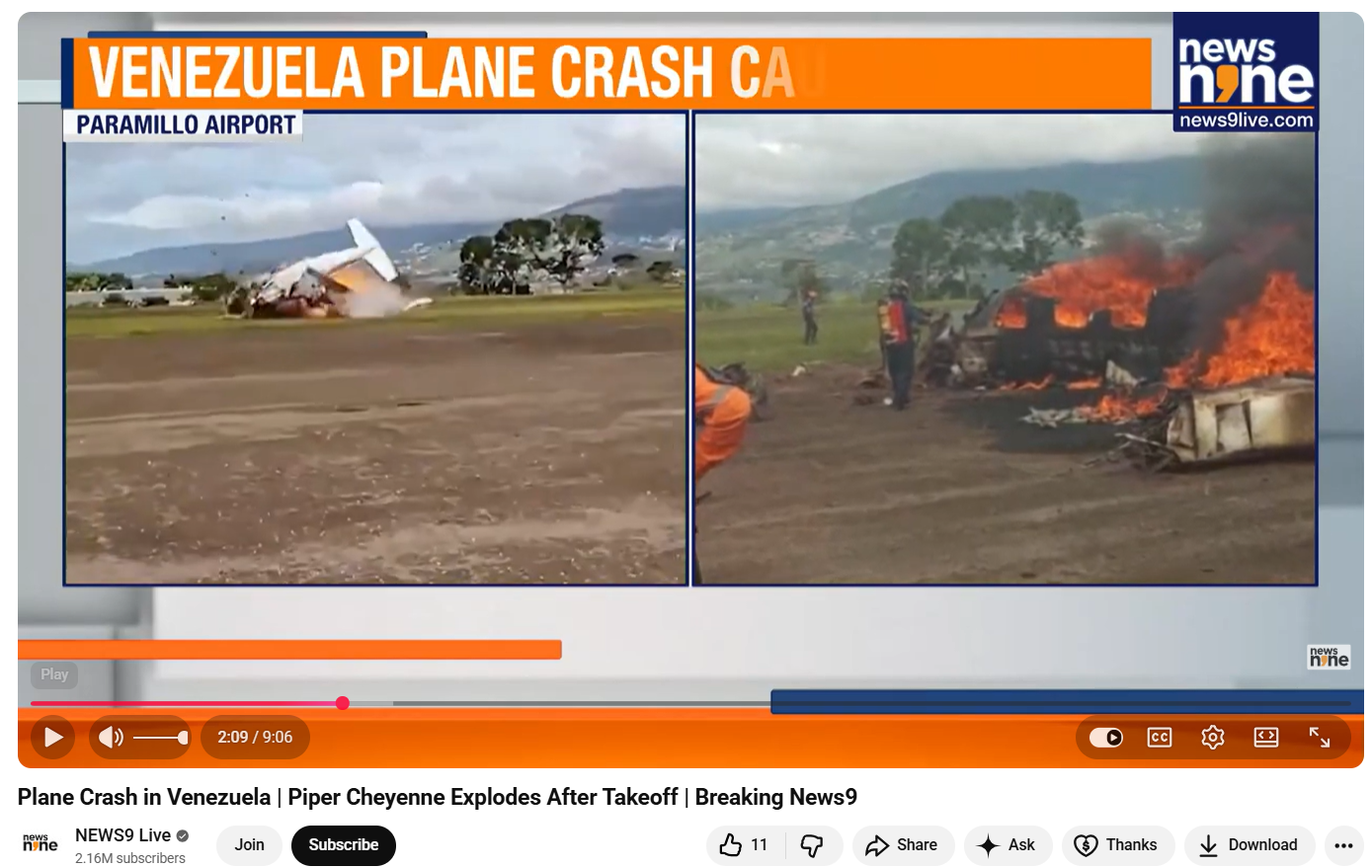
According to the report, the footage shows a plane crash in Venezuela, not India. The incident occurred shortly after a Piper Cheyenne aircraft took off from Paramillo Airport in Táchira, Venezuela. The aircraft crashed within seconds of take-off, killing both occupants on board. The deceased were identified as pilot José Bortone and co-pilot Juan Maldonado. Further confirmation came from a report published on October 22, 2025, by Latin American news outlet El Tiempo. The Spanish-language report also featured the same video visuals and stated that a small aircraft lost control and crashed on the runway at Paramillo Airport in Venezuela, resulting in the deaths of the pilot and co-pilot.
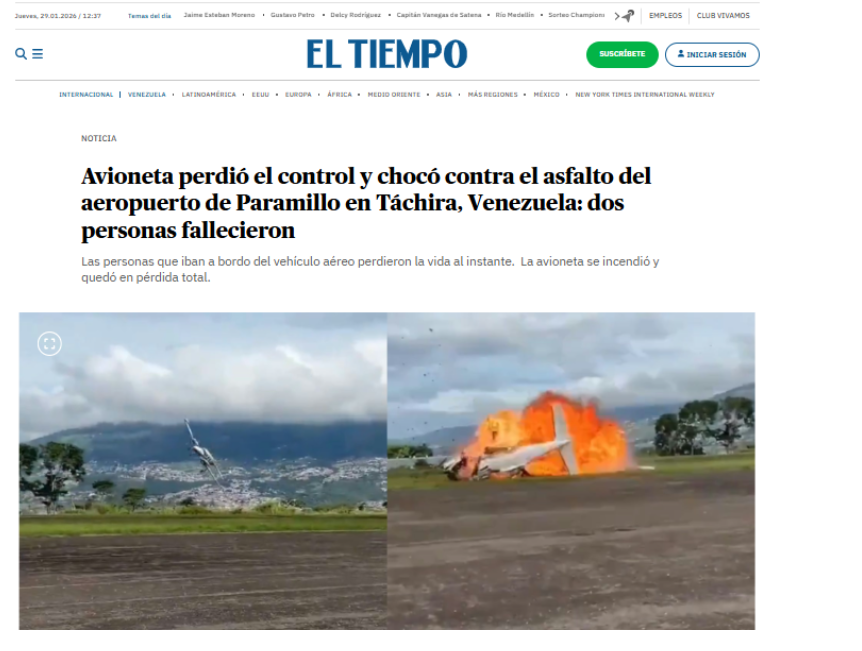
Conclusion
The CyberPeace’s research clearly establishes that the viral video being shared as footage of Ajit Pawar’s alleged plane crash in Baramati is misleading. The video actually shows a plane crash that occurred in Venezuela in October 2025 and has been falsely linked to a tragic claim in India.

Executive Summary
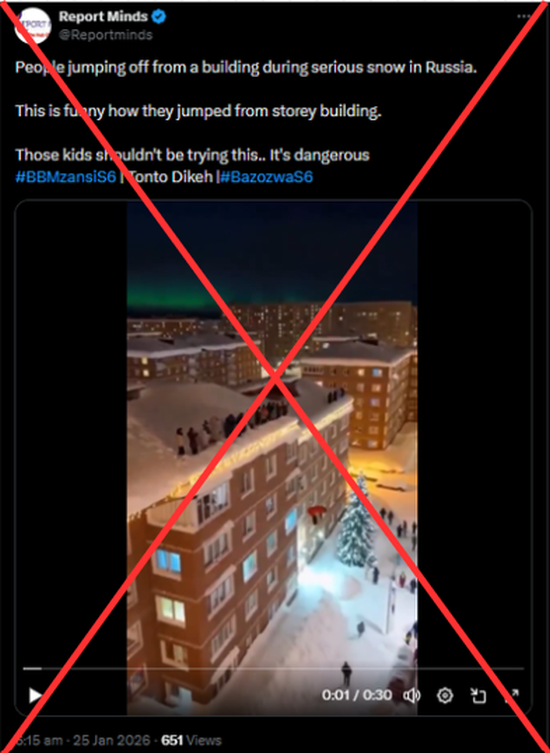
A dramatic video showing several people jumping from the upper floors of a building into what appears to be thick snow has been circulating on social media, with users claiming that it captures a real incident in Russia during heavy snowfall. In the footage, individuals can be seen leaping one after another from a multi-storey structure onto a snow-covered surface below, eliciting reactions ranging from amusement to concern. The claim accompanying the video suggests that it depicts a reckless real-life episode in a snow-hit region of Russia.
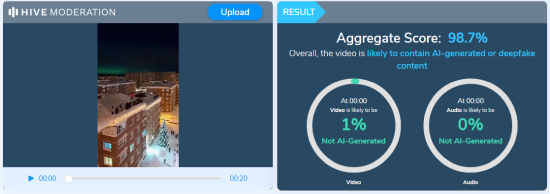
A thorough analysis by CyberPeace confirmed that the video is not a real-world recording but an AI-generated creation. The footage exhibits multiple signs of synthetic media, including unnatural human movements, inconsistent physics, blurred or distorted edges, and a glossy, computer-rendered appearance. In some frames, a partial watermark from an AI video generation tool is visible. Further verification using the Hive Moderation AI-detection platform indicated that 98.7% of the video is AI-generated, confirming that the clip is entirely digitally created and does not depict any actual incident in Russia.
Claim:
The video was shared on social media by an X (formerly Twitter) user ‘Report Minds’ on January 25, claiming it showed a real-life event in Russia. The post caption read: "People jumping off from a building during serious snow in Russia. This is funny, how they jumped from a storey building. Those kids shouldn't be trying this. It's dangerous." Here is the link to the post, and below is a screenshot.
Fact Check:
The Desk used the InVid tool to extract keyframes from the viral video and conducted a reverse image search, which revealed multiple instances of the same video shared by other users with similar claims. Upon close visual examination, several anomalies were observed, including unnatural human movements, blurred and distorted sections, a glossy, digitally-rendered appearance, and a partially concealed logo of the AI video generation tool ‘Sora AI’ visible in certain frames. Screenshots highlighting these inconsistencies were captured during the research .
- https://x.com/DailyLoud/status/2015107152772297086?s=20
- https://x.com/75secondes/status/2015134928745164848?s=20


The video was analyzed on Hive Moderation, an AI-detection platform, which confirmed that 98.7% of the content is AI-generated.
The viral video showing people jumping off a building into snow, claimed to depict a real incident in Russia, is entirely AI-generated. Social media users who shared it presented the digitally created footage as if it were real, making the claim false and misleading.

Executive Summary
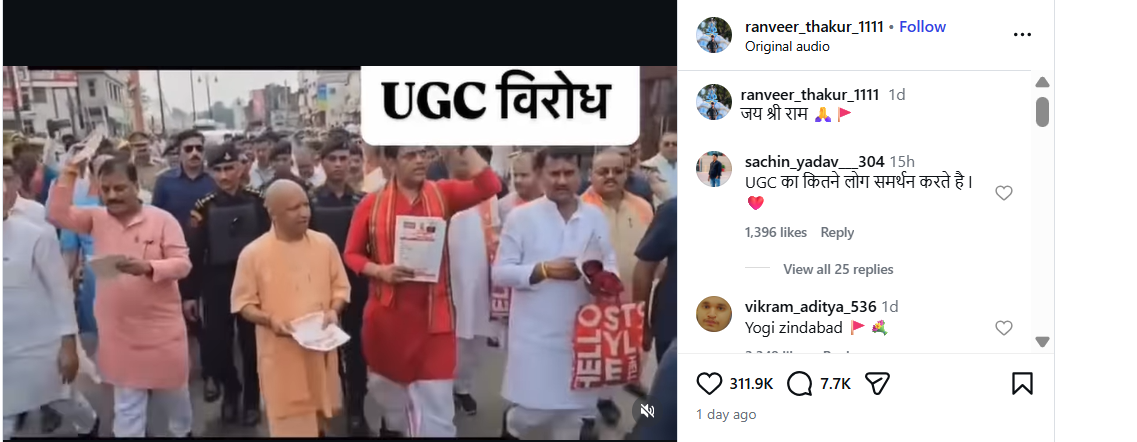
A video circulating on social media shows Uttar Pradesh Chief Minister Yogi Adityanath and Gorakhpur MP Ravi Kishan walking with a group of people. Users are claiming that the two leaders were participating in a protest against the University Grants Commission (UGC). Research by CyberPeace has found the viral claim to be misleading. Our research revealed that the video is from September 2025 and is being shared out of context with recent events. The video was recorded when Chief Minister Yogi Adityanath undertook a foot march in Gorakhpur on a Monday. Ravi Kishan, MP from Gorakhpur, was also present. During the march, the Chief Minister visited local markets, malls, and shops, interacting with traders and gathering information on the implementation of GST rate cuts.
Claim Details:
On Instagram, a user shared the viral video on 27 January 2026. The video shows the Chief Minister and the MP walking with a group of people. The text “UGC protest” appears on the video, suggesting that it is connected to a protest against the University Grants Commission.
Fact Check:
To verify the claim, we searched Google using relevant keywords, but found no credible media reports confirming it.Next, we extracted key frames from the video and searched them using Google Lens. The video was traced to NBT Uttar Pradesh’s X (formerly Twitter) account, posted on 22 September 2025.
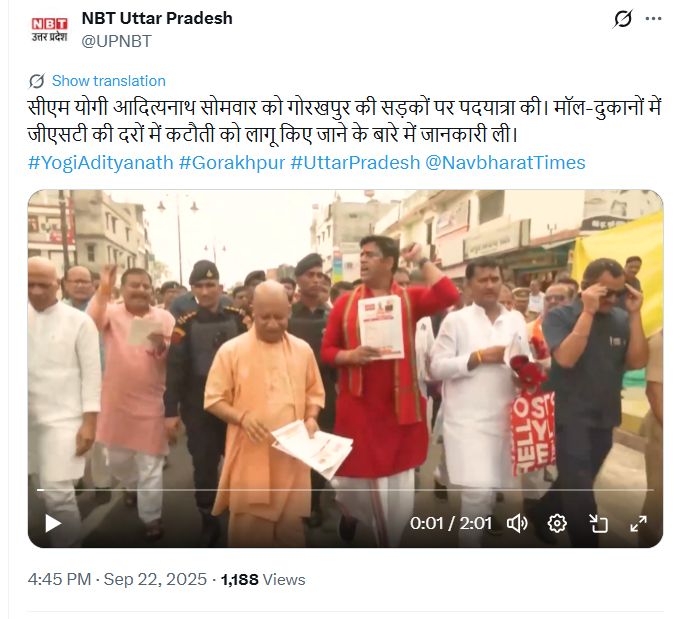
According to NBT Uttar Pradesh, CM Yogi Adityanath undertook a foot march in Gorakhpur, visiting malls and shops to interact with traders and check the implementation of GST rate cuts.
Conclusion:
The viral video is not related to any recent UGC guidelines. It dates back to September 2025, showing CM Yogi Adityanath and MP Ravi Kishan on a foot march in Gorakhpur, interacting with traders about GST rate cuts.The claim that the video depicts a protest against the University Grants Commission is therefore false and misleading.

Executive Summary
A video circulating on social media allegedly shows Uttar Pradesh Chief Minister Yogi Adityanath criticizing Bollywood actor Shah Rukh Khan and asking people not to watch his films. Users sharing the clip claim that these statements are recent. CyberPeace’s research has found the claim to be misleading. research revealed that the video is from 2015, long before Yogi Adityanath became the Chief Minister of Uttar Pradesh. At that time, he was serving as a Member of Parliament from Gorakhpur.
Claim
On January 13, 2026, a Facebook user shared the video with the caption: "A clear message from the Hon’ble Chief Minister of Uttar Pradesh, Param Pujya Mahant Yogi Adityanath, urging people not to watch Shah Rukh Khan’s movie. Share this message widely, send it to all groups you are part of, and inform the youth in your family."
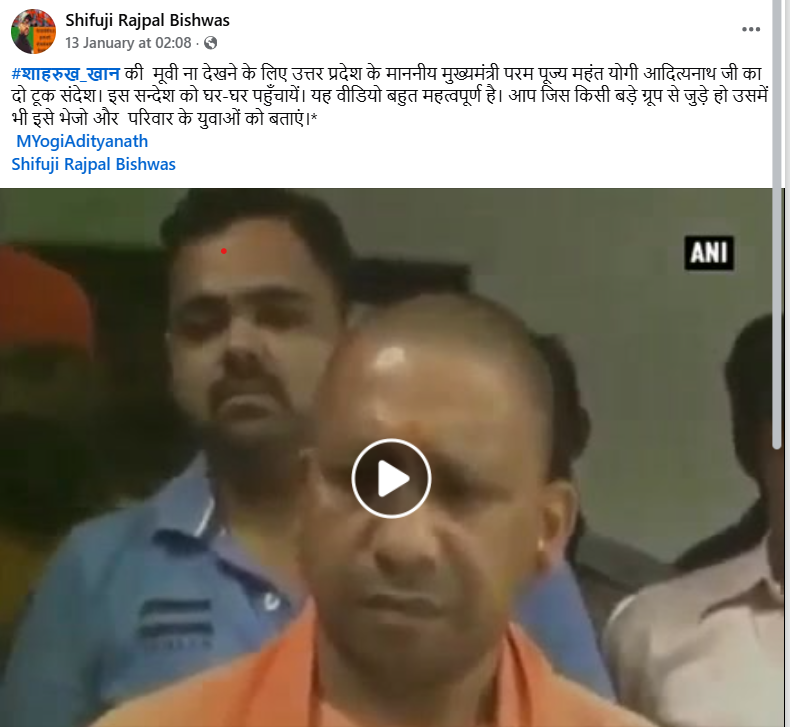
Fact Check:
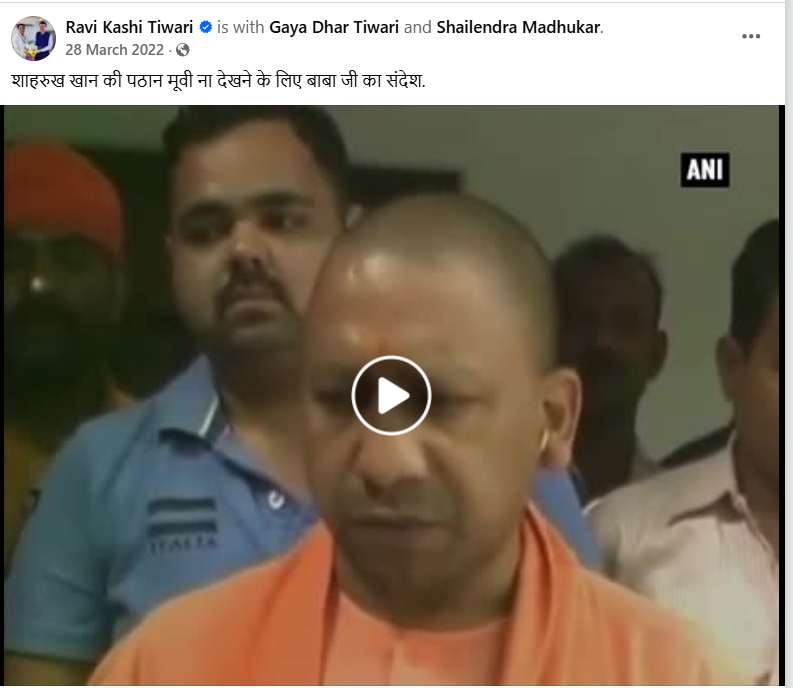
To verify the claim, keyframes from the viral video were extracted and reverse-searched using Google Lens. The same video was found in a Facebook post dated March 28, 2022, where it was shared with the caption: "Baba Ji’s message to not watch Shah Rukh Khan’s ‘Pathaan’ movie."
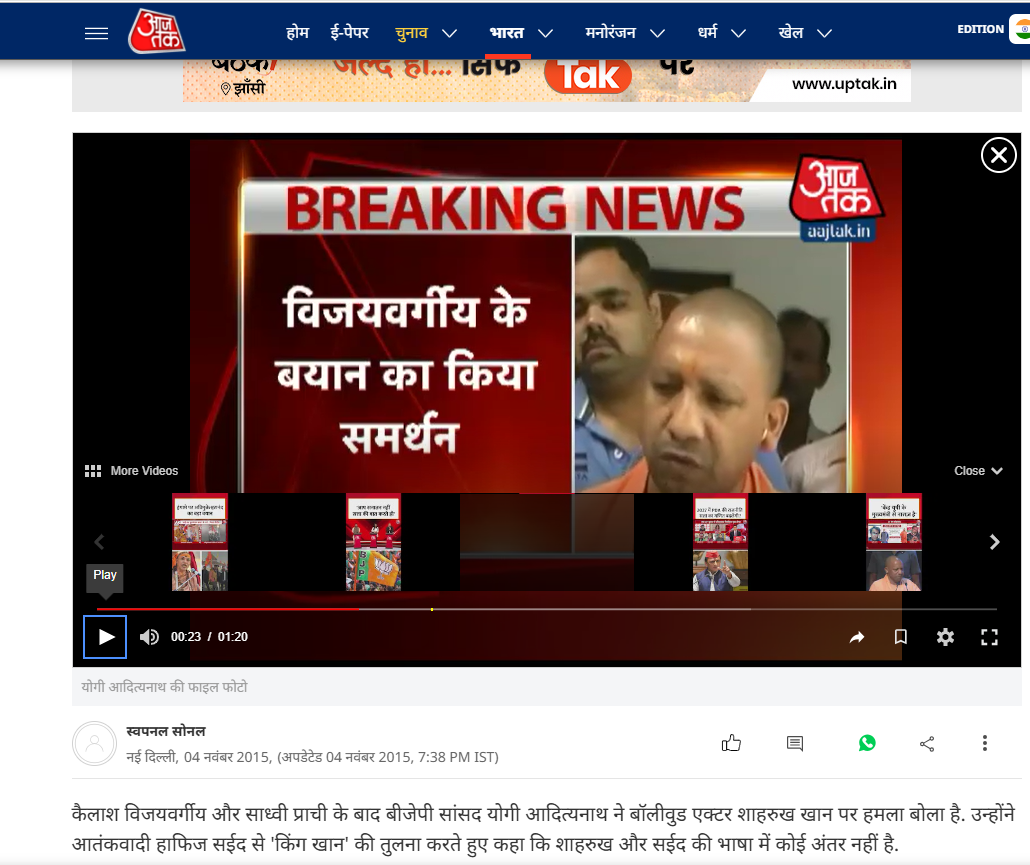
Further research traced the video to Aaj Tak’s website, which reported on November 4, 2015, that then-BJP MP Yogi Adityanath criticized Shah Rukh Khan, comparing his language to that of terrorist Hafiz Saeed, stating that there was no difference in their statements.
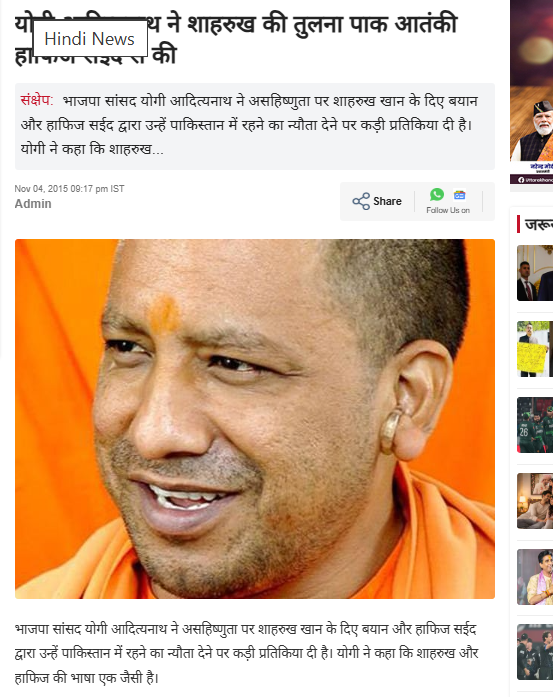
A Live Hindustan report from the same date confirmed that Yogi Adityanath had strongly reacted to Shah Rukh Khan’s comments on rising intolerance in India and Hafiz Saeed’s invitation for him to stay in Pakistan. The reports make it clear that Yogi Adityanath criticized Shah Rukh Khan in 2015 by highlighting the similarity between his statements and those of Hafiz Saeed. At the same time, Shah Rukh Khan had highlighted growing intolerance in the country, citing incidents where filmmakers, scientists, and authors were returning awards, describing it as a sign of “deep intolerance” in India.
Conclusion:
Our research found that the statement attributed to Chief Minister Yogi Adityanath circulating on social media is not recent. The video dates back to 2015, a time when Yogi Adityanath was not yet the Chief Minister of Uttar Pradesh.

Executive Summary
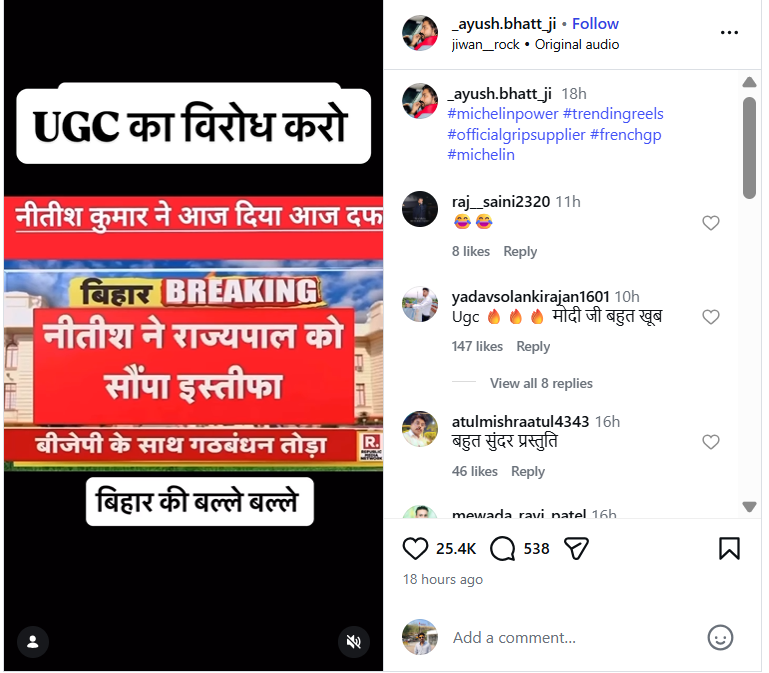
A news video is being widely circulated on social media with the claim that Bihar Chief Minister Nitish Kumar has resigned from his post in protest against the ongoing UGC-related controversy. Several users are sharing the clip while alleging that Kumar stepped down after opposing the issue. However, CyberPeace research has found the claim to be false. The researchrevealed that the video being shared is from 2022 and has no connection whatsoever with the UGC or any recent protests related to it. An old video has been misleadingly linked to a current issue to spread misinformation on social media.
Claim:
An Instagram user shared a video on January 26 claiming that Bihar Chief Minister Nitish Kumar had resigned. The post further alleged that the news was first aired on Republic channel and that Kumar had submitted his resignation to then-Governor Phagu Chauhan. The link to the post, its archived version, and screenshots can be seen below. (Links as provided)
Fact Check:
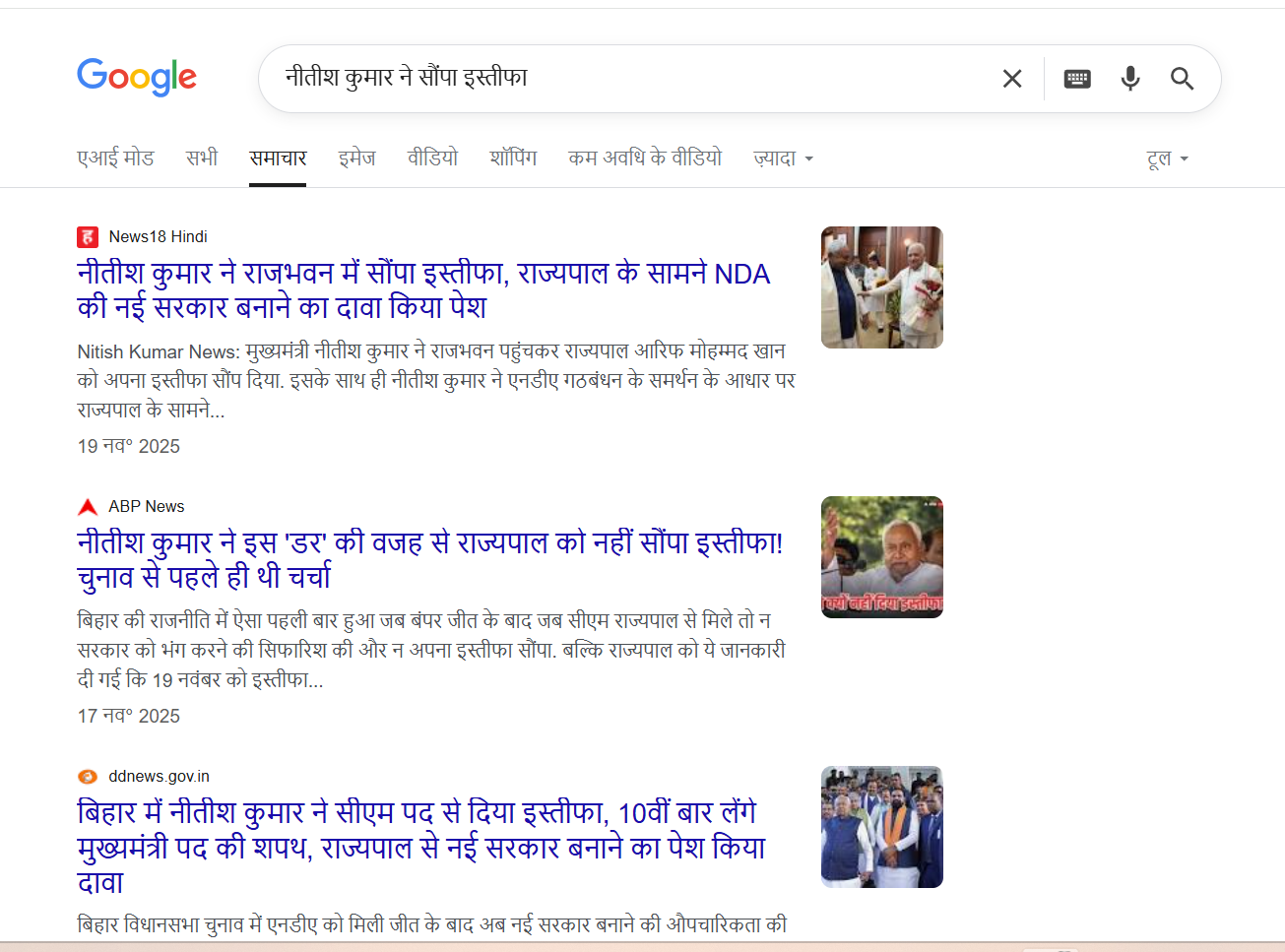
To verify the claim, CyberPeace first conducted a keyword-based search on Google. No credible or established media organisation reported any such resignation, clearly indicating that the viral claim lacked authenticity.
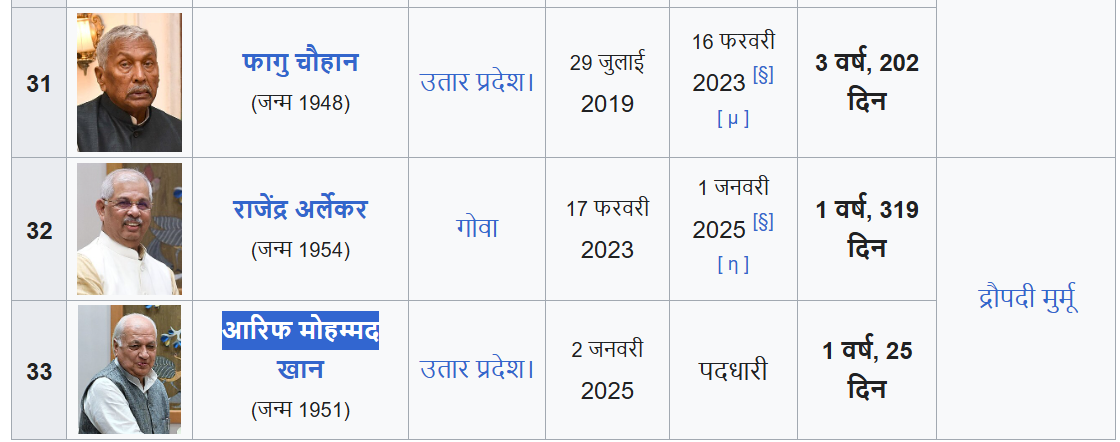
Further, the voiceover in the viral video states that Nitish Kumar handed over his resignation to Governor Phagu Chauhan. However, Phagu Chauhan ceased to be the Governor of Bihar in February 2023. The current Governor of Bihar is Arif Mohammad Khan, making the claim in the video factually incorrect and misleading.
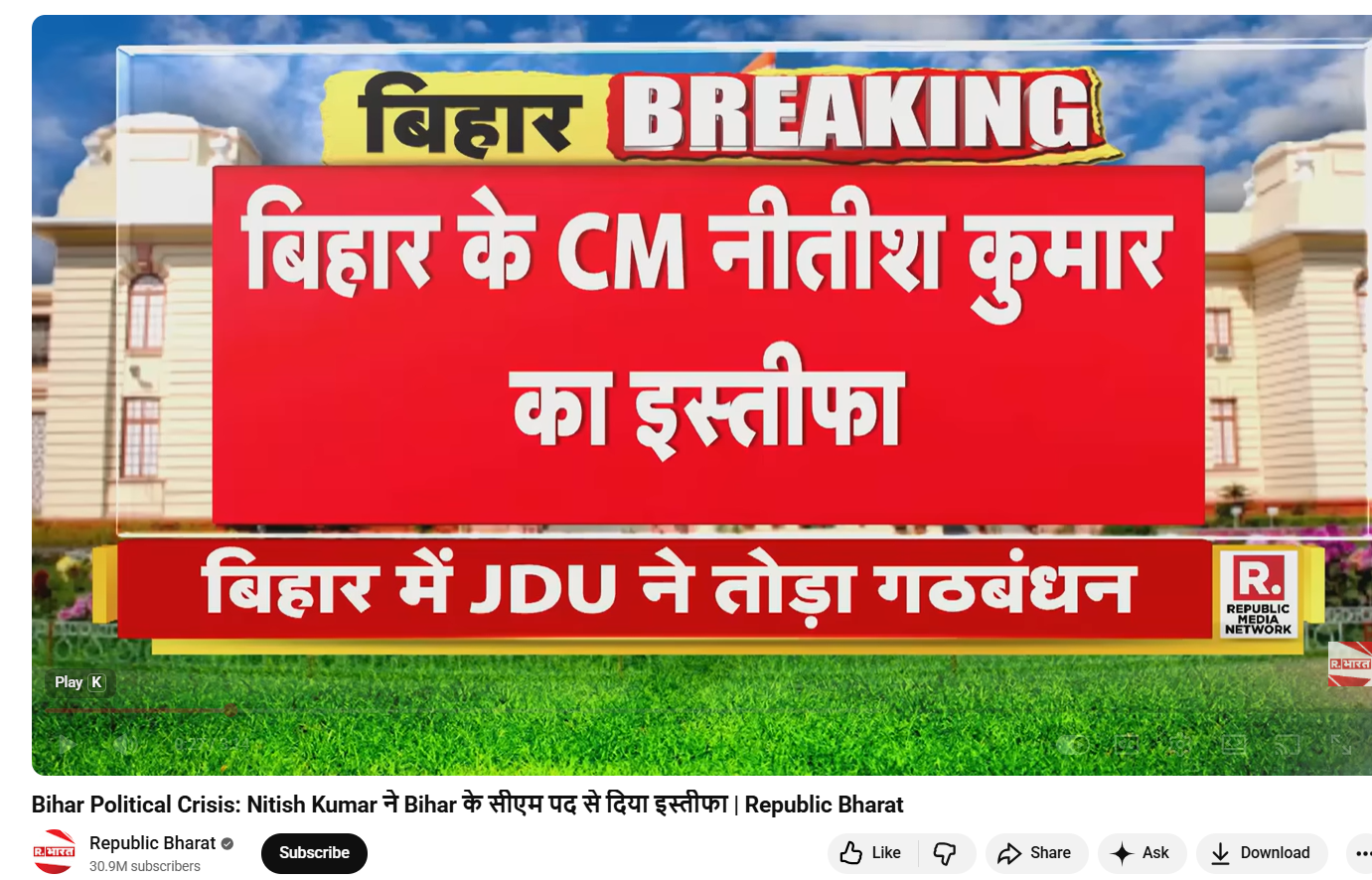
In the next step, keyframes from the viral video were extracted and reverse-searched using Google Lens. This led to the official YouTube channel of Republic Bharat, where the full version of the same video was found. The video was uploaded on August 9, 2022. This clearly establishes that the clip circulating on social media is not recent and is being shared out of context.
Conclusion
CyberPeace’s research confirms that the viral video claiming Nitish Kumar resigned over the UGC issue is false. The video dates back to 2022 and has no link to the current UGC controversy. An old political video has been deliberately circulated with a misleading narrative to create confusion on social media.

Executive Summary
A video widely circulated on social media claims to show a confrontation between a Zee News journalist and Chief of Army Staff (COAS) General Upendra Dwivedi during the Indian Army’s Annual Press Briefing 2026. The video alleges that General Dwivedi made sensitive remarks regarding ‘Operation Sindoor’, including claims that the operation was still ongoing and that diplomatic intervention by former US President Donald Trump had restricted India’s military response. Several social media users shared the clip while questioning the Indian Army’s operational decisions and demanding accountability over the alleged remarks. The CyberPeace concludes that the viral video claiming to show a discussion between a Zee News journalist and Chief of Army Staff General Upendra Dwivedi on ‘Operation Sindoor’ is misleading and digitally manipulated. Although the visuals were sourced from the Indian Army’s Annual Press Briefing 2026, the audio was artificially created and added later to misinform viewers. The Army Chief did not make any remarks regarding diplomatic interference or limitations on military action during the briefing.
Claim:
An X (formerly Twitter) user, Abbas Chandio (@AbbasChandio__), shared the video on January 14, asserting that it showed a Zee News journalist questioning the Army Chief about the status and outcomes of ‘Operation Sindoor’ during a recent press conference. In the clip, the journalist is purportedly heard challenging the Army Chief over his earlier statement that the operation was “still ongoing,” while the COAS is allegedly heard responding that diplomatic intervention during the conflict limited the Army’s ability to pursue further military action. Here is the link and archive link to the post, along with a screenshot.
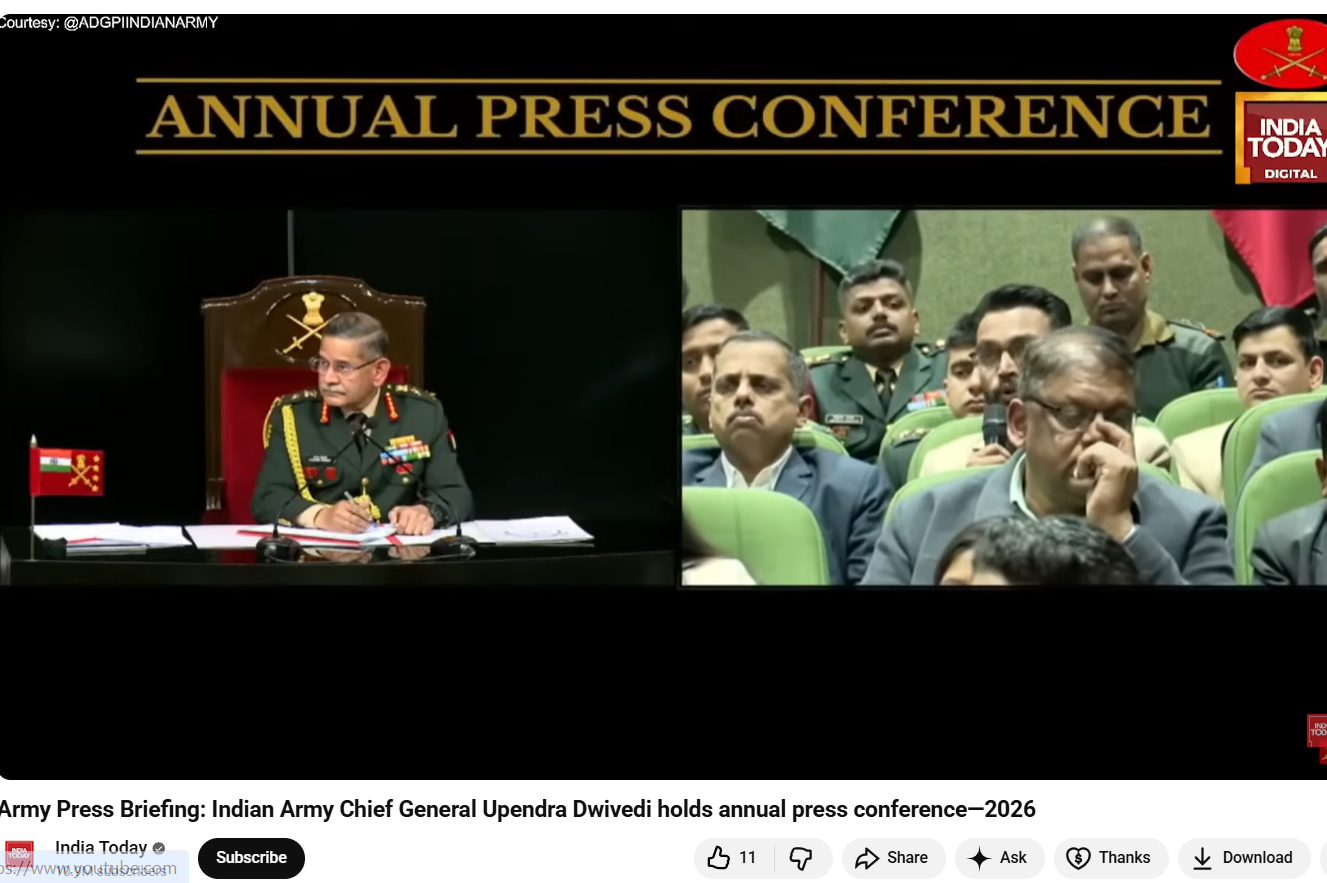
The reverse image search also directed to an extended version of the footage uploaded on the official YouTube channel of India Today. The original video was identified as coverage from the Indian Army’s Annual Press Conference 2026, held on January 13 in New Delhi and addressed by COAS General Upendra Dwivedi. Upon reviewing the original press briefing footage, CyberPeace found no instance where a Zee News journalist questioned the Army Chief about ‘Operation Sindoor’. There was also no mention of the statements attributed to General Dwivedi in the viral clip.
In the authentic footage, journalist Anuvesh Rath was seen raising questions related to defence procurement and modernization, not military operations or diplomatic interventions. Here is the link to the original video, along with a screenshot.
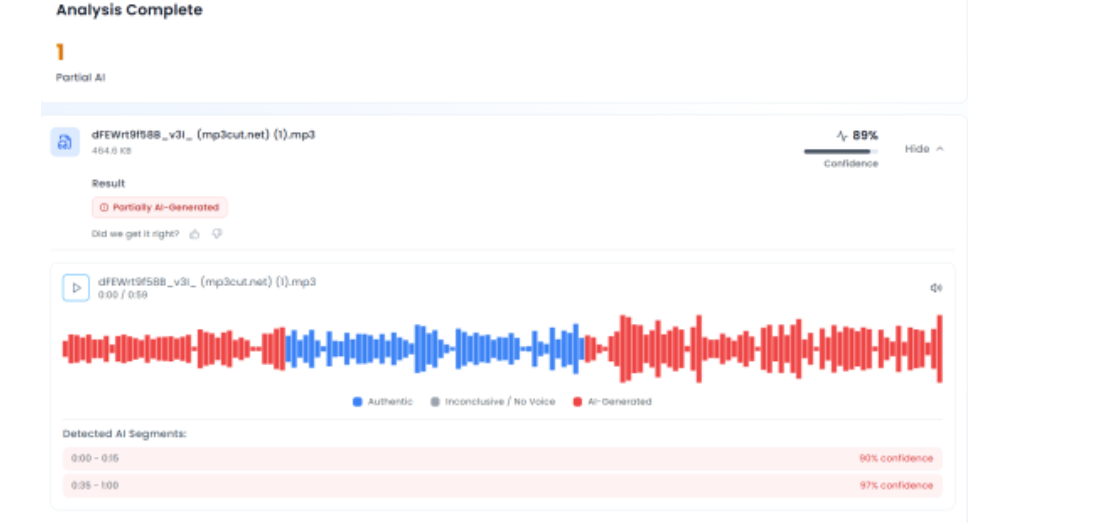
To further verify the claim, CyberPeace extracted the audio track from the viral video and analysed it using the AI-based voice detection tool Aurigin. The analysis revealed that the voice heard in the clip was artificially generated, indicating the use of synthetic or manipulated audio. This confirmed that while genuine visuals from the Army’s official press briefing were used, a fabricated audio track had been overlaid to falsely attribute controversial statements to the Army Chief and a Zee News journalist.
Conclusion
The CyberPeace concludes that the viral video claiming to show a discussion between a Zee News journalist and Chief of Army Staff General Upendra Dwivedi on ‘Operation Sindoor’ is misleading and digitally manipulated. Although the visuals were sourced from the Indian Army’s Annual Press Briefing 2026, the audio was artificially created and added later to misinform viewers. The Army Chief did not make any remarks regarding diplomatic interference or limitations on military action during the briefing. The video is a clear case of digital manipulation and misinformation, aimed at creating confusion and casting doubts over the Indian Army’s official position.

Executive Summary
A video showing a group of people wearing Muslim caps raising provocative slogans against the Rashtriya Swayamsevak Sangh (RSS) is being widely shared on social media. Users sharing the clip claim that the incident took place recently in Uttar Pradesh. However, CyberPeace research found the claim to be false. The probe established that the video is neither recent nor related to Uttar Pradesh. In fact, the footage dates back to 2022 and is from Telangana. The slogans heard in the video were raised during a protest against Goshamahal MLA T. Raja Singh, and the clip is now being circulated with a misleading claim.
Claim
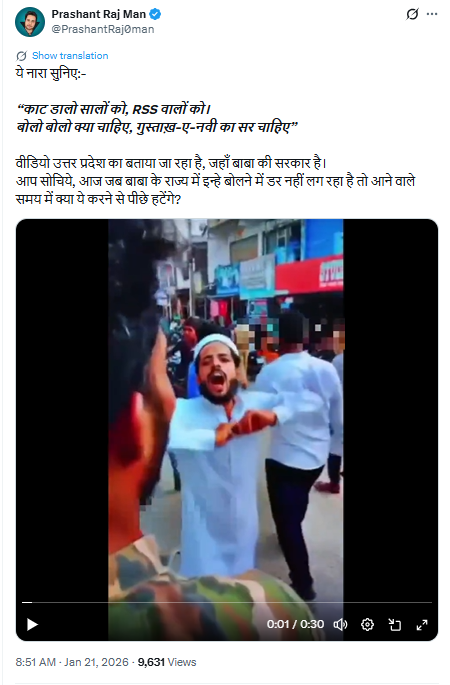
On January 21, 2026, a user on social media platform X (formerly Twitter) shared the video claiming it showed people in Uttar Pradesh chanting slogans such as, “Kaat daalo saalon ko, RSS walon ko” and “Gustakh-e-Nabi ka sar chahiye.” The post suggested that such slogans were being raised openly in Uttar Pradesh despite strict law enforcement. Links to the post and its archive are provided below.
Fact Check:
To verify the claim, CyberPeace research conducted a reverse image search using keyframes from the viral video. The same footage was found on a Facebook account where it had been uploaded on August 26, 2022, indicating that the video is not recent.
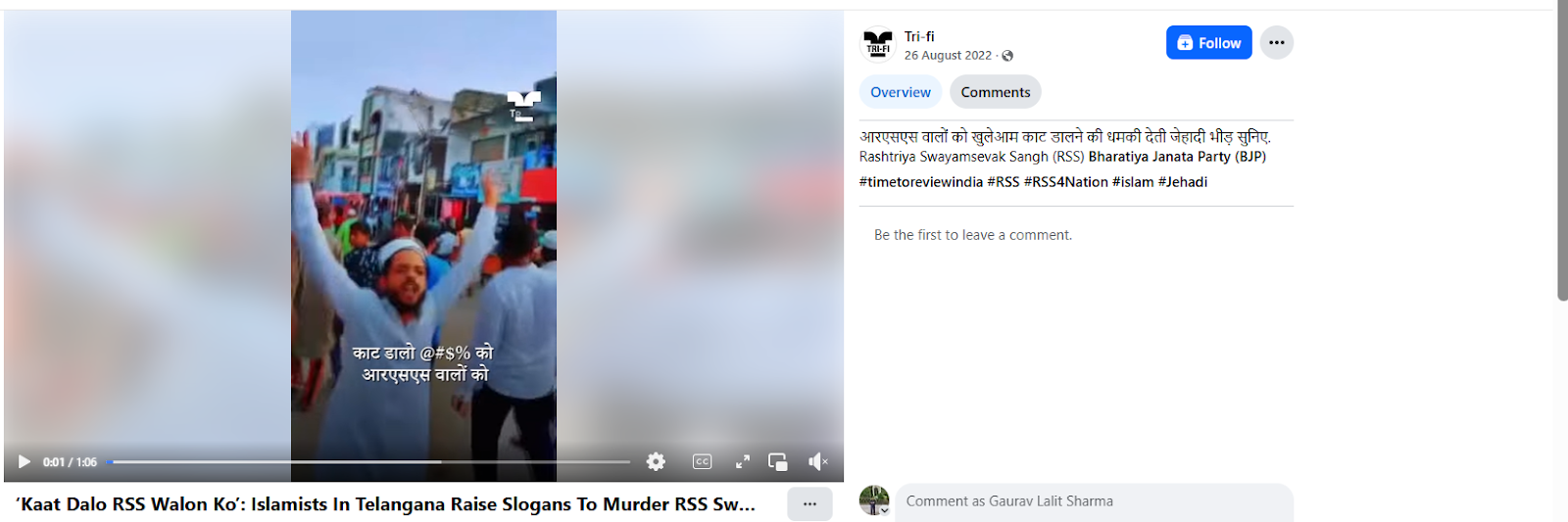
Further verification led the team to a report published by news portal OpIndia on August 25, 2022, which featured identical visuals from the viral clip. According to the report, the video showed a protest march organised against BJP MLA T. Raja Singh following his alleged controversial remarks about Prophet Muhammad. The report identified one of the individuals in the video as Kaleem Uddin, who was allegedly heard raising the slogan “Kaat daalo saalon ko,” to which the crowd responded “RSS walon ko.” The slogan was linked to incitement against RSS members.
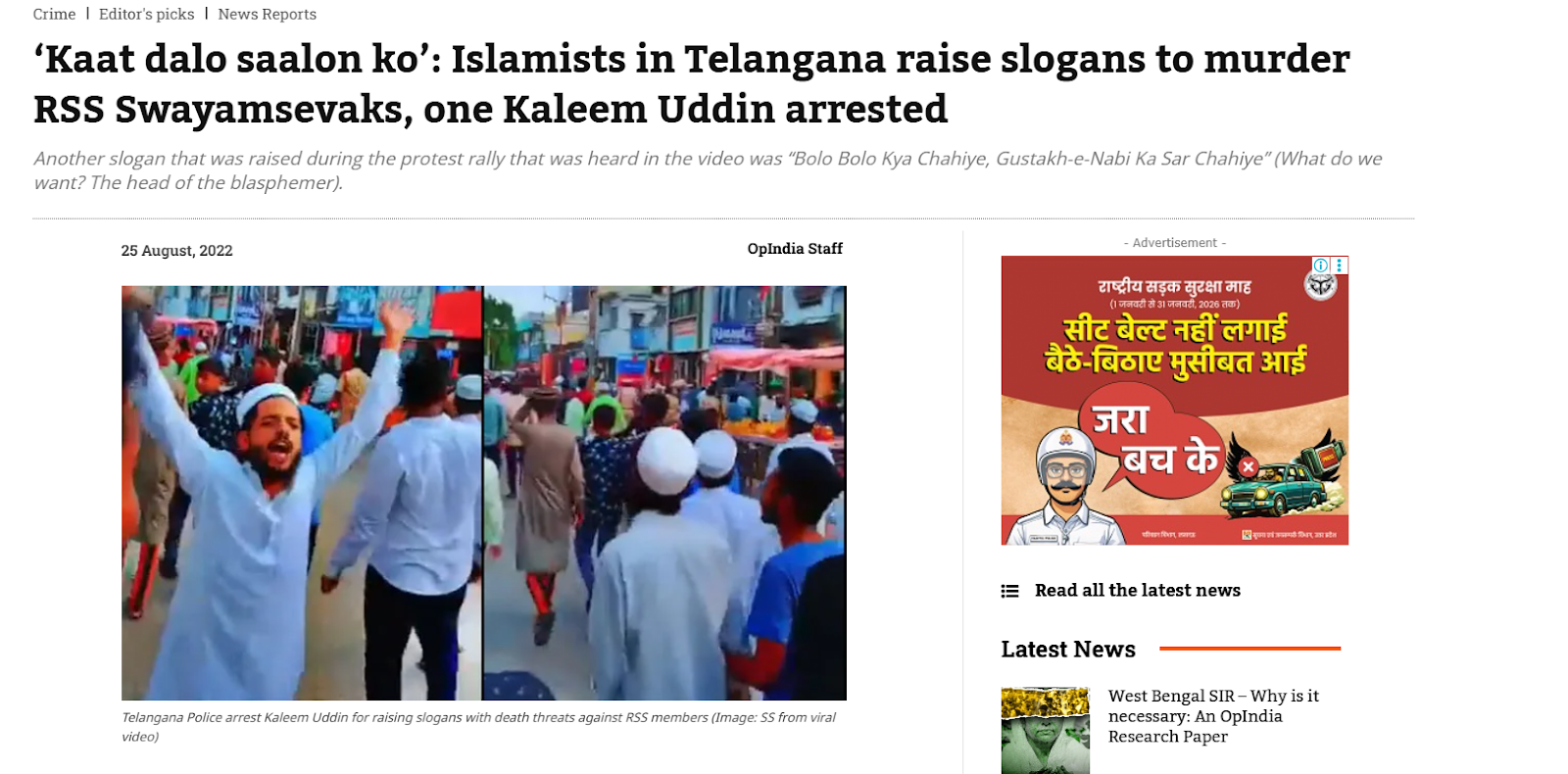
To confirm the location, the video was examined closely. A shop sign reading “Royal Time House” was visible in the footage. Using Google Street View, the same shop was located in Nalgonda, Telangana, conclusively establishing that the video was filmed there and not in Uttar Pradesh.
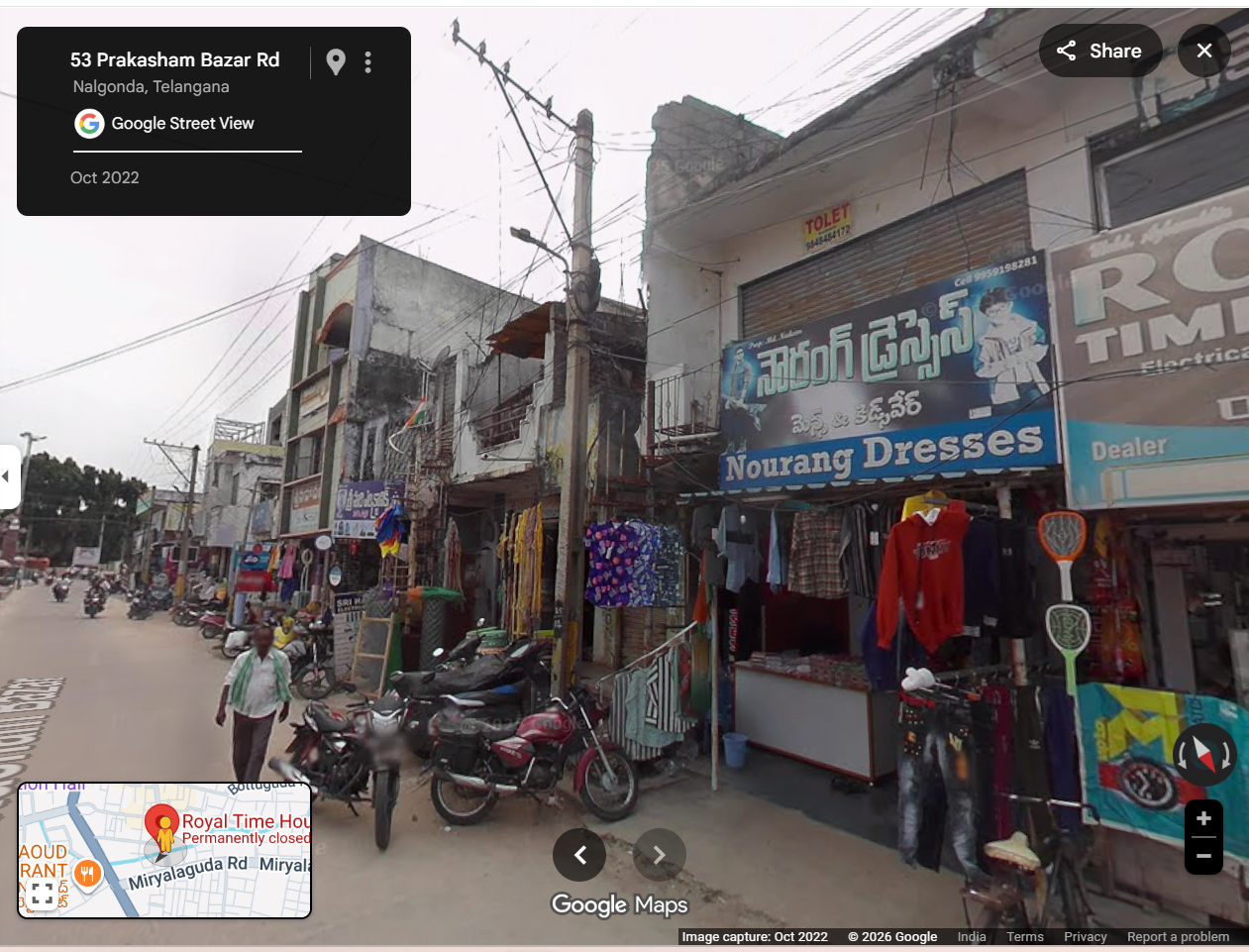
Conclusion
CyberPeace research confirmed that the viral video is from 2022 and was recorded in Telangana, not Uttar Pradesh. The clip is being falsely circulated with a misleading claim to give it a communal and political angle.

Executive Summary
A video of the Leader of the Opposition in the Lok Sabha and Congress MP Rahul Gandhi is being widely shared on social media. In the clip, Gandhi is seen saying that he does not know what “G Gram G” is. Several users are sharing the video with the claim that Rahul Gandhi insulted Lord Ram. However, CyberPeace research found that the claim is misleading. Rahul Gandhi was not referring to Lord Ram in the video. Instead, he was speaking about a newly introduced law titled Viksit Bharat–G RAM G (VB–G RAM G), which has been brought in to replace the Mahatma Gandhi National Rural Employment Guarantee Act (MGNREGA). The viral clip has been shared with a false narrative.
Claim
On January 22, 2026, an Instagram user apnisarkar2024 shared the video claiming, “Rahul Gandhi once again insulted Shri Ram.” (Link, archive link, and screenshot available above)
- https://www.instagram.com/reel/DTzeiy0k3l5
- https://perma.cc/J3A3-NGBM?type=standard
Research
As part of the Research, we first closely examined the viral video. In the clip, Rahul Gandhi is heard saying: “I don’t know what Gram G is. I don’t even know the name of this new law… what is G Gram G…” At no point in the video does Rahul Gandhi mention Lord Ram or make any comment related to religion. To verify the context, we extracted keyframes from the viral clip and conducted a Google Lens search. This led us to a longer version of the same speech uploaded on the official YouTube channel of the Indian National Congress on January 22, 2026. The viral segment appears after the 39:50-minute mark.
The video is from the National MGNREGA Convention held in New Delhi, where Rahul Gandhi criticised the central government over the replacement of MGNREGA with the new VB–G RAM G law. During his speech, he expressed his opposition to the new legislation and stated that he was unfamiliar with its details. Throughout the address, he did not mention or refer to Lord Ram in any manner.
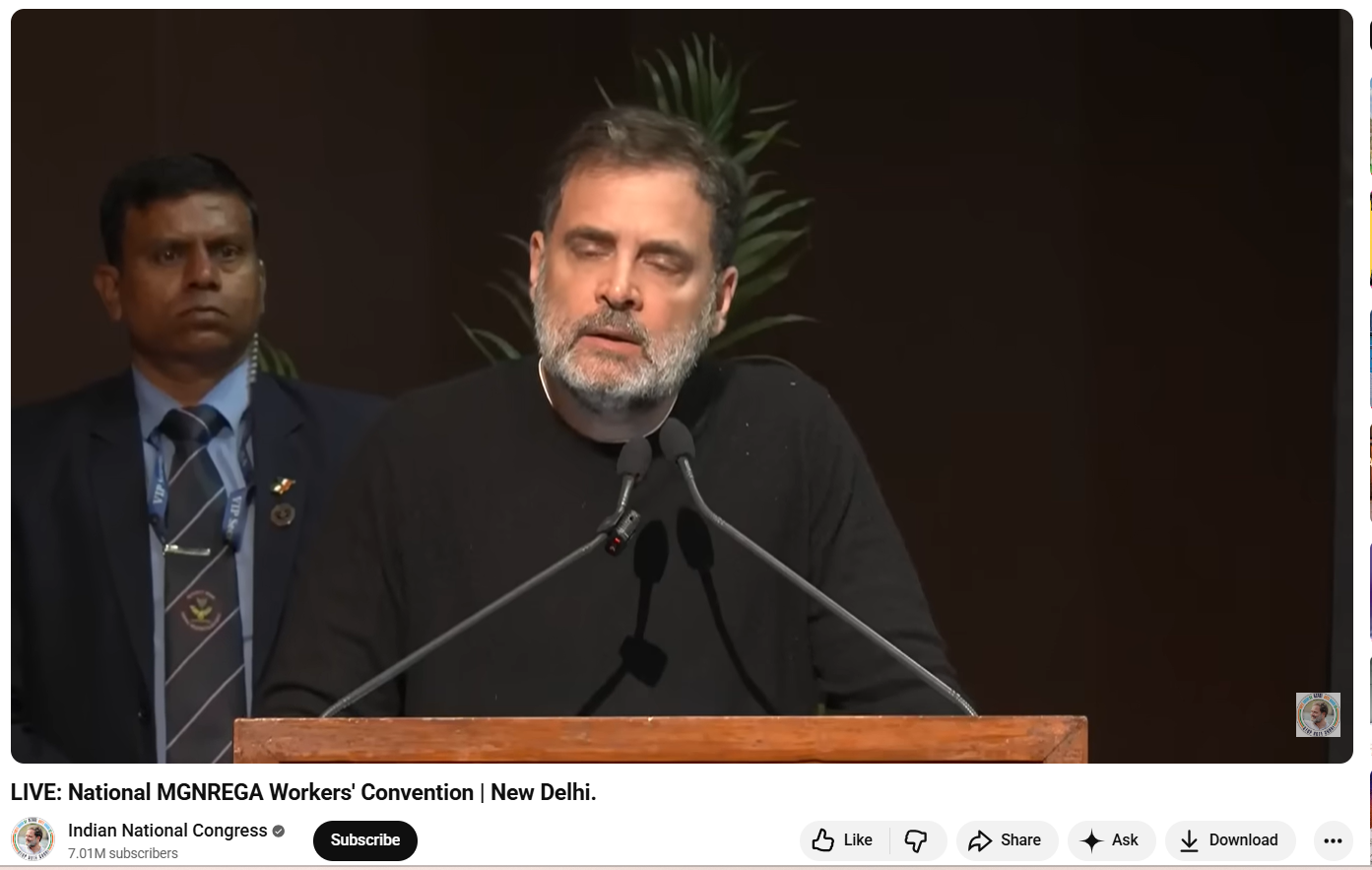
Conclusion
Rahul Gandhi’s remarks in the viral video were related to the newly introduced VB–G RAM G law and were part of his criticism of the central government’s policy decisions. He did not insult Lord Ram. The video is being shared on social media with a misleading and false claim.
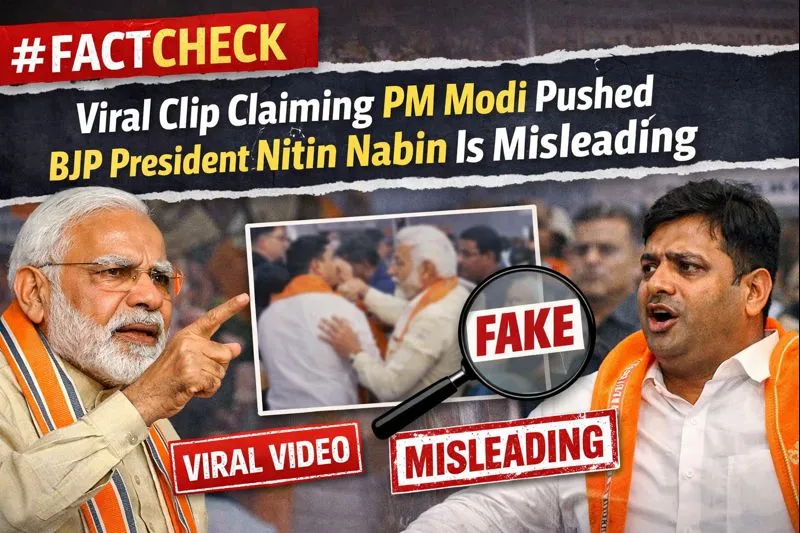
Executive Summary:
A video clip featuring Prime Minister Narendra Modi and the newly elected Bharatiya Janata Party (BJP) national president, Nitin Nabin, is going viral on social media. In the clip, PM Modi is seen apparently pushing Nitin Nabin, prompting claims that Nabin had accidentally stepped between the Prime Minister and the camera, after which Modi allegedly pushed him out of the frame. CyberPeace’s research found that the viral clip is misleading and cropped. The original, unedited video shows Prime Minister Modi gesturing for Nitin Nabin to move ahead and offer floral tributes to the statues of Bharatiya Jana Sangh founder Syama Prasad Mukherjee and Pandit Deendayal Upadhyaya at the BJP headquarters in Delhi. It is pertinent to note that on 20 January 2026, BJP leader Nitin Nabin was elected as the party’s national president. Several senior BJP leaders, including Prime Minister Narendra Modi, were present at the event. During his address, PM Modi remarked, “Nitin Nabin ji is my boss, and I am a party worker.” The statement received widespread attention, following which multiple videos linking to the remark began circulating on social media. A Facebook user shared the viral clip with a Hindi caption alleging that despite calling himself a “party worker,” PM Modi pushed his “boss” out of the camera frame. The post further mocked the position of BJP president, claiming it to be merely ceremonial. (Archived link)
To verify the claim, we conducted a reverse image and video search, which led us to a longer version of the video uploaded on news agency INS’s official X handle on 20 January 2026. The caption stated that PM Modi, BJP president Nitin Nabin, Defence Minister Rajnath Singh, Home Minister Amit Shah, Union Minister Nitin Gadkari and senior leader J.P. Nadda paid tributes to Syama Prasad Mukherjee and Pandit Deendayal Upadhyaya at the BJP headquarters.
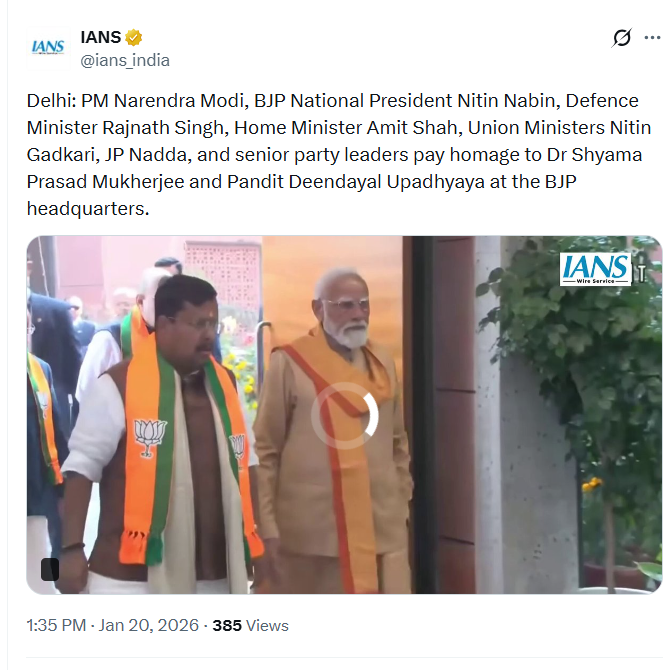
In the full video, PM Modi and Nitin Nabin are seen walking together. PM Modi then requests Nitin Nabin to proceed first for the floral tribute, placing his hand on Nabin’s back as a gesture to move forward. The viral clip selectively cuts this moment out of context and loops it to create a misleading impression. The complete footage clearly shows that PM Modi asked Nitin Nabin to offer tributes first, after which other leaders followed. There is no indication whatsoever that Nitin Nabin was pushed out of the camera frame, as claimed in the viral posts. We also found the live broadcast of the ‘Bharatiya Janata Party Sangathan Parv’ on BJP’s official YouTube channel. The same visuals appear at the end of the live stream, further confirming that PM Modi was merely gesturing for Nitin Nabin to proceed first.
Additionally, photographs available on Nitin Nabin’s official X handle show him offering floral tributes ahead of PM Modi, who is seen standing behind and waiting.

Conclusion:
CyberPeace research confirms that the viral clip has been cropped and shared with a false narrative. In the original context, Prime Minister Narendra Modi was respectfully inviting BJP national president Nitin Nabin to move ahead and pay tributes, not pushing him out of the camera frame.

Introduction
Devices and interconnectivity are the pipelines which drive the data into cyberspace, and in turn, the users consume this data to perform different tasks in the digital age. The security of devices and networks is essential as they are the first defenders of cyberspace. Bad actors often target systems and networks with malware and ransomware, these attacks are differently motivated, but all wreak havoc upon the system and can impact individuals and organisations alike. Mobile users worldwide prefer iOS or Android, but both operating systems are vulnerable to cyberattacks these days. Some of these attacks go undetected for a long time.
Op Triangulation
As reported by Kaspersky, While monitoring the network traffic of their own corporate Wi-Fi network dedicated to mobile devices using the Kaspersky Unified Monitoring and Analysis Platform (KUMA), Kaspersky noticed suspicious activity that originated from several iOS-based phones. Since it is impossible to inspect modern iOS devices from the inside, they created offline backups of the devices in question, inspected them using the Mobile Verification Toolkit’s mvt-ios and discovered traces of compromise. This is known as Operation Triangulation and has been in action since 2019 and got detected in 2023.
The Malware
A portion of the filesystem, including some of the user data and service databases, is included in mobile device backups. The files, directories, and database entries’ timestamps make it possible to reconstruct the events that happened to the device roughly. The “timeline.csv” file created by the mvt-ios software contains a sorted timeline of events that is comparable to the super-timeline utilised by traditional digital forensic tools. Pinpointing particular artefacts that show the compromise using this timeframe. This made it possible to advance the research and reassemble the broad infection sequence:
Through the iMessage service, a message with an attachment containing an exploit is delivered to the target iOS device.
The message initiates a vulnerability that results in code execution without any user input.
The exploit’s code downloads multiple additional stages, including additional exploits for privilege escalation, from the C&C server.
After successful exploitation, a fully functional APT platform is downloaded as the final payload from the C&C server.
The first message and the attachment’s exploit are removed

The lack of persistence support in the harmful toolset is most likely a result of OS restrictions. Multiple devices’ timeframes suggest that after rebooting, they might get infected again. The earliest signs of infection that we found date to 2019. The most recent version of the devices that have been successfully attacked as of the time of writing in June 2023 is iOS 15.7.
The final payload analysis is still ongoing. The programme executes with root rights, implements a set of commands for gathering user and system data, and can run any code downloaded as plugin modules from the C&C server.
Malicious Domains
Using the forensic artefacts, it was possible to identify the domain name set used by the exploits and further malicious stages. They can be used to check the DNS logs for historical information and to identify the devices currently running the malware:
addatamarket[.]net
backuprabbit[.]com
businessvideonews[.]com
cloudsponcer[.]com
datamarketplace[.]net
mobilegamerstats[.]com
snoweeanalytics[.]com
tagclick-cdn[.]com
topographyupdates[.]com
unlimitedteacup[.]com
virtuallaughing[.]com
web-trackers[.]com
growthtransport[.]com
anstv[.]netAns7tv[.]net
Safeguards for iOS users
Despite its world-class safety and privacy architecture, iOS is vulnerable to a few attacks; the following steps can be undertaken to safeguard iOS users –
Keeping Device updated
Security patches
Disabling iMessage would prevent Zero clicks exploits or the Triangulation attacks
Paying zero attention to unwanted, unsolicited messages
The user should make sure that any application they are downloading or installing; it should be from a trusted source ( This Zero click attack does not occur by any other means, It exploits / it targets software vulnerabilities in operating systems networks and applications)
Being cautious with the messaging app and emails
Implement device restrictions (management features like parental control and restrictions over using necessary applications)

Conclusion
Operation Triangulation is one of the recent operations combating cyber attacks, but such operations are launched nearly daily. This is also due to a rapid rise in internet and technology penetration across the world. Cyberattacks have taken a new face as they have evolved with the new and emerging technology. The influence of the Darknet has allowed many hackers to remain on the black hat side due to easy accessibility to illegal tools and material over the dark net, which facilitates such crimes.

Introduction
Social media has become integral to our lives and livelihood in today’s digital world. Influencers are now strong people who shape trends, views, and consumer behaviour. Influencers have become targets for bad actors aiming to abuse their fame due to their significant internet presence. Unfortunately, account hacking has grown frequently, with significant ramifications for influencers and their followers. Furthermore, the emergence of social media platforms in recent years has opened the way for influencer culture. Influencers exert power over their followers’ ideas, lifestyle choices, and purchase decisions. Influencers and brands frequently collaborate to exploit their reach, resulting in a mutually beneficial environment. As a result, the value of influencer accounts has risen dramatically, attracting the attention of hackers trying to abuse their potential for financial gain or personal advantage.
Instances of recent attacks
Places of worship
The hackers have targeted renowned temples for fulfilling their malicious activities the recent attack happened on The Khautji Shyam Temple, a famous religious institution with enormous cultural and spiritual value for its adherents. It serves as a place of worship, community events, and numerous religious activities. However, since technology has invaded all sectors of life, the temple’s online presence has developed, giving worshippers access to information, virtual darshans (holy viewings), and interactive forums. Unfortunately, this digital growth has also rendered the shrine vulnerable to cyber threats. The hackers hacked the Facebook page twice in the month, demanded donations and hacked the cheques the devotes gave to the trust. The second event happened by posting objectional images on the page and hurting the sentiments of the devotees. The Committee of the temple has filed an FIR under various charges and is also seeking help from the cyber cell.
Social media Influencers
Influencers enjoy a vast online following worldwide, but their presence is limited to the digital space. Hence every video, photo is of importance to them. An incident took place with leading news anchor and reporter Barkha Dutt, where in her youtube channel was hacked into, and all the posts made from the channel were deleted. The hackers also replaced the channel’s logo with Tesla and were streaming a live video on the channel featuring Elon Musk. A similar incident was reported by influencer Tanmay Bhatt, who also lost all the content e had posted on his channel. The hackers use the following methods to con social media influencers:
- Social engineering
- Phishing
- Brute Force Attacks
Such attacks on influencers can cause harm to their reputation, can also cause financial loss, and even lose the trust of the viewers or the followers who follow them, thus further impacting the collaborations.

Safeguards
Social media influencers need to be very careful about their cyber security as their prominent presence is in the online world. The influencers from different platforms should practice the following safeguards to protect themselves and their content better online
Secure your accounts
Protecting your accounts with passphrases or strong passwords is the first step. The best strategy for doing this is to create a passphrase, a phrase only you know. We advise choosing a passphrase with at least four words and 15 characters.
To further secure your accounts, you must enable multi-factor authentication in the second step.
To access your account, a hacker must guess your password and provide a second authentication factor (such as a face scan or fingerprint) that matches yours.
Be careful about who has access
Many social media influencers collaborate with a team to help generate and post content while building their personal brands.
This entails using team members who can write and produce material that influencers can share themselves, according to some of them. In these situations, the influencer is the only person who still has access to the account.
There are more potential weak spots when more people have access. Additionally, it increases the number of ways a password or account access could fall into the hands of a cybercriminal. Only some staff members will be as cautious about password security as you may be.
Stay up-to-date on the threats
What’s the most significant way to combat threats to computer security? Information.
Cybercriminals constantly adapt their methods. It’s crucial to stay informed about these threats and how they can be utilised against you.
But it’s not just threats. Social media platforms and other service providers are likewise changing their offerings to avoid these challenges.
Educate yourself to protect yourself. You can keep one step ahead of the hazards that cybercriminals offer by continuously educating yourself.
Preach cybersecurity
As influencers, cyber security should be preached, no matter your agenda.
This will also enable users to inculcate best practices for digital hygiene.
This will also boost the reporting numbers and increase population awareness, thus eradicating such bad actors from our cyberspace.
Acknowledge the risks
Keeping a blind eye will always hurt the safety aspects, as ignorance always causes issues.
Risks should be kept in mind while creating the digital routine and netiquette
Always inform your users of risk existing and potential risks
Monitor threats
After the acknowledgement, it is essential to monitor threats.
Active lookout for threats will allow you to understand the modus Operandi and the vulnerabilities to avoid criminals
Threats monitoring is also a basic netizens’ responsibility to ensure that the threats are reported as they emerge.
Interpret the data
All cyber nodal agencies release data and trends of cybercrimes, understand the trends and protect your vulnerabilities.
Data interpretation can lead to an early flagging of threats and issues, thus protecting the cyber ecosystem by and large.
Create risk profiles
All influencers should create risk profiles and backup profiles.
This will also help protect one’s data as it can be stored on different profiles.
Risk profiles and having a private profile are essential to safeguard the basic cyber interests of an influencer.

Conclusion
As we go deeper into the digital age, we see more technologies emerging, but along with them, we see a new generation of cyber threats and challenges. The physical, as well as the cyberspace, is now inter twinned and interdependent. Practising basic cyber security practices, hygiene, netiquette, and monitoring best practices will go a long way in protecting the online interests of the Influencers and will impact their followers to engage in best practices thus safeguarding the cyber ecosystem at large.

Introduction
All citizens are using tech to their advantage, and so we see a lot of upskilling among the population leading to innovation in India. As we go deeper into cyberspace, we must maintain our cyber security efficiently and effectively. When bad actors use technology to their advantage, we often see data loss or financial loss of the victim, In this blog, we will shine light upon two new forms of cyber attacks, causing havoc upon the innocent. The “Daam” Malware and a new malicious app are the two new issues.
Daam Botnet
Since 2021, the DAAM Android botnet has been used to acquire unauthorised access to targeted devices. Cybercriminals use it to carry out different destructive actions. Using the DAAM Android botnet’s APK binding service, threat actors can combine malicious code with a legitimate application. Keylogging, ransomware, VOIP call records, runtime code execution, browser history collecting, incoming call recording, PII data theft, phishing URL opening, photo capture, clipboard data theft, WiFi and data status switching, and browser history gathering are just a few of the functions offered by the DAAM Android botnet. The DAAM botnet tracks user activity using the Accessibility Service and stores keystrokes it has recorded together with the name of the programme package in a database. It also contains a ransomware module that encrypts and decrypts data on the infected device using the AES method.
Additionally, the botnet uses the Accessibility service to monitor the VOIP call-making features of social media apps like WhatsApp, Skype, Telegram, and others. When a user engages with these elements, the virus begins audio recording.
The Malware
CERT-IN, the central nodal institution that reacts to computer security-related issues, claims that Daam connects with various Android APK files to access a phone. The files on the phone are encrypted using the AES encryption technique, and it is distributed through third-party websites.
It is claimed that the malware can damage call recordings and contacts, gain access to the camera, change passwords, take screenshots, steal SMS, download/upload files, and perform a variety of other things.

Safeguards and Guidelines by Cert-In
Cert-In has released the guideline for combating malware. These were issued in the public interest. The recommendations by Cert-In are as follows-
Only download from official app stores to limit the risk of potentially harmful apps.
Before downloading an app, always read the details and user reviews; likewise, always give permissions that are related to the program’s purpose.
Install Android updates solely from Android device vendors as they become available.
Avoid visiting untrustworthy websites or clicking on untrustworthy
Install and keep anti-virus and anti-spyware software up to date.
Be cautious if you see mobile numbers that appear to be something other than genuine/regular mobile numbers.
Conduct sufficient investigation Before clicking on a link supplied in a communication.
Only click on URLs that clearly display the website domain; avoid abbreviated URLs, particularly those employing bit.ly and tinyurl.
Use secure browsing technologies and filtering tools in antivirus, firewall, and filtering services.
Before providing sensitive information, look for authentic encryption certificates by looking for the green lock in your browser’s URL information, look for authentic encryption certificates by looking for the green lock in your browser’s URL bar.
Any ‘strange’ activity in a user’s bank account must be reported immediately to the appropriate bank.
New Malicious App
From the remote parts of Jharkhand, a new form of malicious application has been circulated among people on the pretext of a bank account closure. The bad actors have always used messaging platforms like Whatsapp and Telegram to circulate malicious links among unaware and uneducated people to dupe them of their hard-earned money.
They send an ordinary-looking message on Whatsapp or Telegram where they mention that the user has a bank account at ICICI bank and, due to irregularity with the credentials, their account is being deactivated. Further, they ask users to update their PAN card to reactivate their account by uploading the PAN card on an application. This app, in turn, is a malicious app that downloads all the user’s personal credentials and shares them with the bad actors via text message, allowing them to bypass banks’ two-factor authentication and drain the money from their accounts. The Jharkhand Police Cyber Cells have registered numerous FIRs pertaining to this type of cybercrime and are conducting full-scale investigations to apprehend the criminals.
Conclusion
Malware and phishing attacks have gained momentum in the previous years and have become a major contributor to the tally of cybercrimes in the country. DaaM malware is one of the examples brought into light due to the timely action by Cert-In, but still, a lot of such malware are deployed by bad actors, and we as netizens need to use our best practices to keep such criminals at bay. Phishing crimes are often substantiated by exploiting vulnerabilities and social engineering. Thus working towards a rise in awareness is the need of the hour to safeguard the population by and large.

Introduction
In today’s time, everything is online, and the world is interconnected. Cases of data breaches and cyberattacks have been a reality for various organisations and industries, In the recent case (of SAS), Scandinavian Airlines experienced a cyberattack that resulted in the exposure of customer details, highlighting the critical importance of preventing customer privacy. The incident is a wake-up call for Airlines and businesses to evaluate their cyber security measures and learn valuable lessons to safeguard customers’ data. In this blog, we will explore the incident and discuss the strategies for protecting customers’ privacy in this age of digitalisation.
Analysing the backdrop
The incident has been a shocker for the aviation industry, SAS Scandinavian Airlines has been a victim of a cyberattack that compromised consumer data. Let’s understand the motive of cyber crooks and the technique they used :
Motive Behind the Attack: Understanding the reasons that may have driven the criminals is critical to comprehending the context of the Scandinavian Airlines cyber assault. Financial gain, geopolitical conflicts, activism, or personal vendettas are common motivators for cybercriminals. Identifying the purpose of the assault can provide insight into the attacker’s aims and the possible impact on both the targeted organisation and its consumers. Understanding the attack vector and strategies used by cyber attackers reveals the amount of complexity and possible weaknesses in an organisation’s cybersecurity defences. Scandinavian Airlines’ cyber assault might have included phishing, spyware, ransomware, or exploiting software weaknesses. Analysing these tactics allows organisations to strengthen their security against similar assaults.
Impact on Victims: The Scandinavian Airlines (SAS) cyber attack victims, including customers and individuals related to the company, have suffered substantial consequences. Data breaches and cyber-attack have serious consequences due to the leak of personal information.
1)Financial Losses and Fraudulent Activities: One of the most immediate and upsetting consequences of a cyber assault is the possibility of financial loss. Exposed personal information, such as credit card numbers, can be used by hackers to carry out illegal activities such as unauthorised transactions and identity theft. Victims may experience financial difficulties and the need to spend time and money resolving these concerns.
2)Concerns about privacy and personal security: A breach of personal data can significantly impact the privacy and personal security of victims. The disclosed information, including names, addresses, and contact information, might be exploited for nefarious reasons, such as targeted phishing or physical harassment. Victims may have increased anxiety about their safety and privacy, which can interrupt their everyday life and create mental pain.
3) Reputational Damage and Trust Issues: The cyber attack may cause reputational harm to persons linked with Scandinavian Airlines, such as workers or partners. The breach may diminish consumers’ and stakeholders’ faith in the organisation, leading to a bad view of its capacity to protect personal information. This lack of trust might have long-term consequences for the impacted people’s professional and personal relationships.
4) Emotional Stress and Psychological Impact: The psychological impact of a cyber assault can be severe. Fear, worry, and a sense of violation induced by having personal information exposed can create emotional stress and psychological suffering. Victims may experience emotions of vulnerability, loss of control, and distrust toward digital platforms, potentially harming their overall quality of life.
5) Time and Effort Required for Remediation: Addressing the repercussions of a cyber assault demands significant time and effort from the victims. They may need to call financial institutions, reset passwords, monitor accounts for unusual activity, and use credit monitoring services. Resolving the consequences of a data breach may be a difficult and time-consuming process, adding stress and inconvenience to the victims’ lives.
6) Secondary Impacts: The impacts of an online attack could continue beyond the immediate implications. Future repercussions for victims may include trouble acquiring credit or insurance, difficulties finding future work, and continuous worry about exploiting their personal information. These secondary effects can seriously affect victims’ financial and general well-being.
Apart from this, the trust lost would take time to rebuild.

Takeaways from this attack
The cyber-attack on Scandinavian Airlines (SAS) is a sharp reminder of cybercrime’s ever-present and increasing menace. This event provides crucial insights that businesses and people may use to strengthen cybersecurity defences. In the lessons that were learned from the Scandinavian Airlines cyber assault and examine the steps that may be taken to improve cybersecurity and reduce future risks. Some of the key points that can be considered are as follows:
Proactive Risk Assessment and Vulnerability Management: The cyber assault on Scandinavian Airlines emphasises the significance of regular risk assessments and vulnerability management. Organisations must proactively identify and fix possible system and network vulnerabilities. Regular security audits, penetration testing, and vulnerability assessments can help identify flaws before bad actors exploit them.
Strong security measures and best practices: To guard against cyber attacks, it is necessary to implement effective security measures and follow cybersecurity best practices. Lessons from the Scandinavian Airlines cyber assault emphasise the importance of effective firewalls, up-to-date antivirus software, secure setups, frequent software patching, and strong password rules. Using multi-factor authentication and encryption technologies for sensitive data can also considerably improve security.
Employee Training and Awareness: Human mistake is frequently a big component in cyber assaults. Organisations should prioritise employee training and awareness programs to educate employees about phishing schemes, social engineering methods, and safe internet practices. Employees may become the first line of defence against possible attacks by cultivating a culture of cybersecurity awareness.
Data Protection and Privacy Measures: Protecting consumer data should be a key priority for businesses. Lessons from the Scandinavian Airlines cyber assault emphasise the significance of having effective data protection measures, such as encryption and access limits. Adhering to data privacy standards and maintaining safe data storage and transfer can reduce the risks connected with data breaches.
Collaboration and Information Sharing: The Scandinavian Airlines cyber assault emphasises the need for collaboration and information sharing among the cybersecurity community. Organisations should actively share threat intelligence, cooperate with industry partners, and stay current on developing cyber threats. Sharing information and experiences can help to build the collective defence against cybercrime.
Conclusion
The Scandinavian Airlines cyber assault is a reminder that cybersecurity must be a key concern for organisations and people. Organisations may improve their cybersecurity safeguards, proactively discover vulnerabilities, and respond effectively to prospective attacks by learning from this occurrence and adopting the lessons learned. Building a strong cybersecurity culture, frequently upgrading security practices, and encouraging cooperation within the cybersecurity community are all critical steps toward a more robust digital world. We may aim to keep one step ahead of thieves and preserve our important information assets by constantly monitoring and taking proactive actions.

Introduction
WhatsApp has become the new platform for scams, and the number of cases of WhatsApp scams is increasing daily. Just like that, a new WhatsApp scam has been started, and many WhatsApp users in India have reported receiving missed calls from unknown international numbers. Worse, one does not even have to answer the call to be scammed. A missed call is sufficient to be scammed.
Millions of populations switch from normal SMS to WhatsApp, usually, people used to get fake messages and marketing messages, but the trend of scamming has been evolving now. Most people get calls from different countries, and they are concerned about how these scammers got the numbers. WhatsApp works through VoIP networks, so no extra charges from any country exist. And about 500 million WhatsApp users are getting these scam calls, the calls are mainly on job-scams of promising part-time employment and opportunities. These types of job scam calls have been started reporting in 2023.
People reporting missed calls from countries like Ethiopia (+251), Malaysia (+60), Indonesia (+62), Vietnam (+84), etc.
The agenda of these calls are still unclear. Still, in some cases, the scammers ask for confidential information from WhatsApp users, like bank details, so the users must not reveal their personal information. Also, it is important to note that if you get any calls from a particular country, it necessarily does not mean it is from that country. Various agencies sell international numbers for WhatsApp calls.
Why has WhatsApp become a hub scam?
The generation has evolved and dumped the old SMS into WhatsApp. From school to college and offices, people use WhatsApp for their official work, as it is very easy and user-friendly, so people avoid safety measures. Generally, users need to understand the consequences of technology and use it with safeguards and awareness. Many people lose money and become victims of scams on WhatsApp as they share their confidential information. And the worse is that one does not even have to answer the call to be scammed. A missed call is sufficient to be scammed.
Before these international calls scam, the user received a call from the scam that they were from KBC, and the user won something. Then sought confidential information by the excuse that they would transfer the money to the user, and because of that user got scammed by the scammers. These scams have risen rapidly lately.
Safeguards users can use against these scam calls
WhatsApp responds to complaints regarding international calls to “block and report.”
If you have already received such calls, the best thing you can do is report and block them right away. As a result, the same number does not return to your phone, and numerous identical reports may persuade WhatsApp to delete the number entirely.
WhatsApp is also working on an update allowing users to block calls from unknown numbers on the service.

Users must modify their phone’s and app’s fundamental privacy settings to protect themselves from data breaches. The calls are directed toward app users who are actively using the app. However, by modifying the account’s appearance, a user can lessen the likelihood of being added to the scammers’ attack lists.
Limit Privacy
Begin by modifying WhatsApp’s ‘who can see’ settings. If your profile photo, last seen, and online status are visible to anybody, restrict them to persons on your contact list only. Change the About and Groups options as well.
Turn on two-factor authentication
Enabling two-factor authentication on WhatsApp adds more security to your data. In addition, the app also supports biometric protection in case of theft or loss.
Active Reporting
The users should report as soon as they see something odd or suspicious activity.
A typical question that users have is, ‘Where do the scammers acquire my phone number from?’
The answer is a little more complicated than we thought. Your data is retained on the company database from the time you sign up on a website or reveal your phone number at a store in order to take advantage of promotional offers and promotions. Due to a lack of technological infrastructure and legislation to protect personal data, a scammer can simply obtain your information.
According to Palo Alto research, India is the second most vulnerable country in the APAC region in terms of cyberattacks and data breaches. A data protection law is essential in the face of increasing calls and data breaches.
The Digital Personal Data Protection bill is set to be introduced in the parliament’s monsoon session. The bill has the potential to protect data, which will help to eliminate scams.
Conclusion
Several people had tweeted on tweeter about receiving fake calls on WhatsApp from international numbers more than once. WhatsApp encrypts calls and messages, making it difficult to track the person, and it appears that hackers are taking advantage of this to swindle customers. If you receive a WhatsApp call from any of the above ISD codes, we strongly advise you not to answer it and to block the number so the bad actors do not call you again. Report & block immediately that’s what WhatsApp has been responding to the complainants.

Introduction
A recent massive scam has been uncovered in the Indian state of Gujarat, where the Criminal Investigation Department (CID) has blacklisted 30,000 SIM cards that were used for illegal activities. The scam has created a huge uproar in the state, and its implications are significant. In this blog, we will discuss the details of the Gujarat scam and its impact on the state.
What is sim card fraud?
Sim card fraud occurs when someone uses a fake or cloned sim card to impersonate someone else. This allows the fraudster to gain access to sensitive information or conduct transactions on behalf of the victim. The use of fraudulent sim cards has become increasingly common in recent years, with scammers targeting individuals and businesses around the world.
The Gujarat Scam: The Gujarat scam involves the use of SIM cards for illegal activities such as extortion, blackmail, and cybercrime. The CID has identified that the SIM cards were obtained using fake documents and were used for illegal activities. The scam has been happening for a while, involving several individuals, including businessmen, politicians, and government officials.
The CID has conducted raids across the state and has arrested several individuals involved in the scam. They have also seized a significant amount of cash, mobile phones, and other electronic devices used for illegal activities. The investigation is ongoing, and more arrests are expected in the coming days.
The Gujarat scam is not an isolated incident, as similar scams have been reported in other parts of the country. The Telecom Regulatory Authority of India (TRAI) has also reported that several telecom operators are not following the regulations and are not verifying the authenticity of documents used to obtain SIM cards.
Impact on the State: The Gujarat scam has caused significant damage to the state’s reputation, and it has also affected the economy. The scam has highlighted the lack of regulation in the telecom industry, and it has exposed the loopholes in the system that criminals are exploiting.
The blacklisting of 30,000 SIM cards will affect several individuals who may have obtained them legally but were unaware of their use for illegal activities. The blacklisting may also impact businesses that rely on mobile phones for their operations.
The scam has also raised concerns about personal information and data safety. With the use of fake documents to obtain SIM cards, it is evident that personal information is not secure and can be easily misused. The government needs to take steps to ensure that personal information is protected and that the telecom industry is regulated to prevent such scams from happening in the future.
Steps Taken by the Government: The Gujarat scam has prompted the government to take action to prevent such incidents from happening in the future. The government has announced that it will implement stricter regulations in the telecom industry to prevent the misuse of SIM cards. The government has also announced that it will introduce a system to verify the authenticity of documents used to obtain SIM cards.
The government has also urged citizens to be vigilant and report any suspicious activity related to the misuse of SIM cards. The government has assured citizens that it will take strict action against those involved in the scam and that it will ensure the safety of personal information and data.
The TRAI has also taken steps to address the issue. It has directed telecom operators to verify the authenticity of documents used to obtain SIM cards and to follow the regulations. The TRAI has also introduced a new system to identify and deactivate inactive SIM cards.
Here are some key takeaways from the Gujarat Sim scam: These takeaways should be kept in mind to prevent such incidents from happening in the future and to ensure the safety of citizens and businesses.
Need for Stricter Regulations: The Gujarat Sim scam has highlighted the need for stricter regulations in the telecom industry. The government needs to ensure that telecom operators follow the regulations and verify the authenticity of documents used to obtain SIM cards. This will help prevent the misuse of SIM cards and illegal activities.
Importance of Personal Information Security: The scam has raised concerns about personal information and data safety. It is important to ensure that personal information is protected and that the telecom industry is regulated to prevent such scams from happening in the future.
Impact on Reputation and Economy: The Gujarat scam has caused significant damage to the state’s reputation, and it has also affected the economy. The blacklisting of 30,000 SIM cards will impact several individuals who may have obtained them legally but were unaware of their use for illegal activities. The scam has also raised concerns about the safety of businesses that rely on mobile phones for their operations.
Need for Vigilance: The government has urged citizens to be vigilant and report any suspicious activity related to the misuse of SIM cards. It is important for citizens to be aware of the regulations and to report any illegal activities to prevent such incidents from happening in the future.
Strong Action Against Criminals: The blacklisting of 30,000 SIM cards and the arrests made by the CID sends a strong message to those involved in illegal activities that they will not be spared. It is important for the government to take strict action against those involved in the scam to deter others from engaging in such activities.
Conclusion
The Gujarat scam has exposed vulnerabilities in the telecom industry and highlighted the need for stricter regulations to prevent such incidents from happening in the future. The blacklisting of 30,000 SIM cards has sent a strong message to those involved in illegal activities that they will not be spared. The government’s efforts to implement stricter regulations and ensure the safety of personal information and data are commendable. It is now up to the citizens to be vigilant and report any suspicious activity to prevent such incidents from happening in the future.
The telecom industry plays a vital role in the country’s development, and it is important to ensure that it is regulated to prevent the misuse of its services. Overall, the Gujarat Sim scam has highlighted the need for stricter regulations, personal information security, vigilance, and strong action against criminals.
Reference:

Introduction
In todays time, we can access any information in seconds and from the comfort of our homes or offices. The internet and its applications have been substantial in creating an ease of access to information, but the biggest question which still remains unanswered is Which information is legit and which one is fake? As netizens, we must be critical of what information we access and how.
Influence of Bad actors
The bad actors are one of the biggest threats to our cyberspace as they make the online world full of fear and activities which directly impact the users financial or emotional status by exploitaing their vulnerabilities and attacking them using social engineering. One such issue is website spoofing. In website spoofing, the bad actors try and create a website similar to the original website of any reputed brand. The similarity is so uncanny that the first time or occasional website users find it very difficult to find the difference between the two websites. This is basically an attempt to access sensitive information, such as personal and financial information, and in some cases, to spread malware into the users system to facilitate other forms of cybercrimes. Such websites will have very lucrative offers or deals, making it easier for people to fall prey to such phoney websites In turn, the bad actors can gain sensitive information right from the users without even calling or messaging them.
The Incident
A Noida based senior citizen couple was aggreved by using their dishwasher, and to get it fixed, they looked for the customer care number on their web browser. The couple came across a customer care number- 1800258821 for IFB, a electronics company. As they dialed the number and got in touch with the fake customer care representative, who, upon hearing the couple’s issue, directed them to a supposedly senior official of the company. The senior official spoke to the lady, despite of the call dropping few times, he was admant on staying in touch with the lady, once he had established the trust factor, he asked the lady to download an app which he potrayed to be an app to register complaints and carry out quick actions. The fake senior offical asked the lady to share her location and also asked her to grant few access permissions to the application along with a four digit OTP which looked harmless. He further asked the kady to make a transaction of Rs 10 as part of the complaint processing fee. Till this moment, the couple was under the impression that their complaimt had been registred and the issue with their dishwasher would be rectified soon.
The couple later at night recieved a message from their bank, informing them that Rs 2.25 lakh had been debited from their joint bank account, the following morning, they saw yet another text message informing them of a debit of Rs 5.99 lakh again from their account. The couple immediatly understood that they had become victims to cyber fraud. The couple immediatly launched a complaint on the cyber fraud helpline 1930 and their respective bank. A FIR has been registerd in the Noida Cyber Cell.
How can senior citizens prevent such frauds?
Senior citizens can be particularly vulnerable to cyber frauds due to their lack of familiarity with technology and potential cognitive decline. Here are some safeguards that can help protect them from cyber frauds:
- Educate seniors on common cyber frauds: It’s important to educate seniors about the most common types of cyber frauds, such as phishing, smishing, vishing, and scams targeting seniors.
- Use strong passwords: Encourage seniors to use strong and unique passwords for their online accounts and to change them regularly.
- Beware of suspicious emails and messages: Teach seniors to be wary of suspicious emails and messages that ask for personal or financial information, even if they appear to be from legitimate sources.
- Verify before clicking: Encourage seniors to verify the legitimacy of links before clicking on them, especially in emails or messages.
- Keep software updated: Ensure seniors keep their software, including antivirus and operating system, up to date.
- Avoid public Wi-Fi: Discourage seniors from using public Wi-Fi for sensitive transactions, such as online banking or shopping.
- Check financial statements: Encourage seniors to regularly check their bank and credit card statements for any suspicious transactions.
- Secure devices: Help seniors secure their devices with antivirus and anti-malware software and ensure that their devices are password protected.
- Use trusted sources: Encourage seniors to use trusted sources when making online purchases or providing personal information online.
- Seek help: Advise seniors to seek help if they suspect they have fallen victim to a cyber fraud. They should contact their bank, credit card company or report the fraud to relevant authorities. Calling 1930 should be the first and primary step.
Conclusion
The cyberspace is new space for people of all generations, the older population is a little more vulnerble in this space as they have not used gadgets or internet for most f theur lives, and now they are dependent upon the devices and application for their convinience, but they still do not understand the technology and its dark side. As netizens, we are responsible for safeguarding the youth and the older population to create a wholesome, safe, secured and sustainable cyberecosystem. Its time to put the youth’s understanding of tech and the life experience of the older poplaution in synergy to create SoPs and best practices for erradicating such cyber frauds from our cyberspace. CyberPeace Foundation has created a CyberPeace Helpline number for victims where they will be given timely assitance for resolving their issues; the victims can reach out the helpline on +91 95700 00066 and thay can also mail their issues on helpline@cyberpeace.net.

Along with the loss of important files and information, data loss can result in downtime and lost revenue. Unexpected occurrences, including natural catastrophes, cyber-attacks, hardware malfunctions, and human mistakes, can result in the loss of crucial data. Recovery from these without a backup plan may be difficult, if not impossible.
The fact is that the largest threat to the continuation of your organization today is cyberattacks. Because of this, disaster recovery planning should be approached from a data security standpoint. If not, you run the risk of leaving your vital systems exposed to a cyberattack. Cybercrime has been more frequent and violent over the past few years. In the past, major organizations and global businesses were the main targets of these attacks by criminals. But nowadays, businesses of all sizes need to be cautious of digital risks.
Many firms might suffer a financial hit even from a brief interruption to regular business operations. But imagine if a situation forced a company to close for a few days or perhaps weeks! The consequences would be disastrous.
One must have a comprehensive disaster recovery plan in place that is connected with the cybersecurity strategy, given the growing danger of cybercrime.
Let’s look at why having a solid data security plan and a dependable backup solution are essential for safeguarding a company from external digital threats.
1. Apply layered approaches
One must specifically use precautionary measures like antivirus software and firewalls. One must also implement strict access control procedures to restrict who may access the network.
One must also implement strict access control procedures to restrict who may access the network.
2. Understand the threat situation
If someone is unaware of the difficulties one should be prepared for, how can they possibly expect to develop a successful cybersecurity strategy? They can’t, is the simple response.
Without a solid understanding of the threat landscape, developing the plan will require a lot too much speculation. With this strategy, one can allocate resources poorly or perhaps completely miss a threat.
Because of this, one should educate themselves on the many cyber risks that businesses now must contend with.
3. Adopt a proactive security stance
Every effective cybersecurity plan includes a number of reactive processes that aren’t activated until an attack occurs. Although these reactive strategies will always be useful in cybersecurity, the main focus of your plan should be proactiveness.
There are several methods to be proactive, but the most crucial one is to analyze your network for possible threats regularly. your network securely. Having a SaaS Security Posture Management (SSPM) solution in place is beneficial for SaaS applications, in particular.
A preventive approach can lessen the effects of a data breach and aid in keeping data away from attackers.
4. Evaluate your ability to respond to incidents
Test your cybersecurity disaster recovery plan’s effectiveness by conducting exercises and evaluating the outcomes. Track pertinent data during the exercise to see if your plan is working as expected.
Meet with your team after each drill to evaluate what went well and what didn’t. This strategy enables you to continuously strengthen your plan and solve weaknesses. This procedure may be repeated endlessly and should be.
You must include cybersecurity protections in your entire disaster recovery plan if you want to make sure that your business is resilient in the face of cyber threats. You may strengthen data security and recover from data loss and corruption by putting in place a plan that focuses on both the essential components of proactive data protection and automated data backup and recovery.
For instance, Google distributes all data among several computers in various places while storing each user’s data on a single machine or collection of machines. To prevent a single point of failure, chunk the data and duplicate it across several platforms. As an additional security safeguard, they give these data chunks random names that are unreadable to the human eye.[1]
The process of creating and storing copies of data that may be used to safeguard organizations against data loss is referred to as backup and recovery. In the case of a main data failure, the backup’s goal is to make a duplicate of the data that can be restored.
5. Take zero-trust principles
Don’t presume that anything or anybody can be trusted; zero trust is a new label for an old idea. Check each device, user, service, or other entity’s trustworthiness before providing it access, then periodically recheck trustworthiness while access is allowed to make sure the entity hasn’t been hacked. Reduce the consequences of any breach of confidence by granting each entity access to only the resources it requires. The number of events and the severity of those that do happen can both be decreased by using zero-trust principles.
6. Understand the dangers posed by supply networks
A nation-state can effectively penetrate a single business, and that business may provide thousands of other businesses with tainted technological goods or services. These businesses will then become compromised, which might disclose their own customers’ data to the original attackers or result in compromised services being offered to customers. Millions of businesses and people might be harmed as a result of what began with one infiltrating corporation.
In conclusion, a defense-in-depth approach to cybersecurity won’t vanish. Organizations may never be able to totally eliminate the danger of a cyberattack, but having a variety of technologies and procedures in place can assist in guaranteeing that the risks are kept to a minimum.
References:

One of the best forums for many video producers is YouTube. It also has a great chance of generating huge profits. YouTube content producers need assistance to get the most views, likes, comments, and subscribers for their videos and channels. As a result, some people could use YouTube bots to unnaturally raise their ranks on the YouTube site, which might help them get more organic views and reach a larger audience. However, this strategy is typically seen as unfair and can violate the YouTube platform’s terms of service.
As YouTube grows in popularity, so does the usage of YouTube bots. These bots are software programs that may automate operations on the YouTube platform, such as watching, liking, or disliking videos, subscribing to or unsubscribing from channels, making comments, and adding videos to playlists, among others. There have been YouTube bots around for a while. Many YouTubers widely use these computer codes to increase the number of views on their videos and accounts, which helps them rank higher in YouTube’s algorithm. Researchers discovered a new bot that takes private information from YouTube users’ accounts.
CRIL (Cyble Research and Intelligence Labs) has been monitoring new and active malware families CRIL has discovered a new YouTube bot virus capable of viewing, liking, and commenting on YouTube videos. Furthermore, it is capable of stealing sensitive information from browsers and acting as a bot that accepts orders from the Command and Control (C&C) server to carry out other harmful operations.
The Bot Insight
This YouTube bot has the same capabilities as all other YouTube bots, including the ability to view, like, and comment on videos. Additionally, it has the ability to steal private data from browsers and act as a bot that takes commands from a Command and Control (C&C) server for various malicious purposes. Researchers from Cyble discovered the inner workings of this information breach the Youtube bot uses the sample hash(SHA256) e9dac8b677a670e70919730ee65ab66cc27730378b9233d944ad7879c530d312.They discovered that it was created using the.NET compiler and is an executable file with a 32-bit size.
- The virus runs an AntiVM check as soon as it is executed to thwart researchers’ attempts to find and analyze malware in a virtual environment.
- It stops the execution if it finds that it is operating in a regulated setting. If not, it will carry out the tasks listed in the argument strings.
- Additionally, the virus creates a mutex, copies itself to the %appdata% folder as AvastSecurity.exe, and then uses cmd.exe to run.
- The new mutex makes a task scheduler entry and aids in ensuring
- The victim’s system’s installed Chromium browsers are used to harvest cookies, autofill information, and login information by the AvastSecurity.exe program.
- In order to view the chosen video, the virus runs the YouTube Playwright function, passing the previously indicated arguments along with the browser’s path and cookie data.
- YouTube bot uses the YouTube Playwright function to launch the browser environment with the specified parameters and automate actions like watching, liking, and commenting on YouTube videos. The feature is dependent on Microsoft. playwright’s kit.
- The malware establishes a connection to a C2 server and gets instructions to erase the entry for the scheduled task and end its own process, extract log files to the C2 server, download and run other files, and start/stop watching a YouTube movie.
- Additionally, it verifies that the victim’s PC has the required dependencies, including the Playwright package and the Chrome browser, installed. When it gets the command “view,” it will download and install these dependencies if they are missing.
Recommendations
The following is a list of some of the most critical cybersecurity best practices that serve as the first line of defense against intruders. We propose that our readers follow the advice provided below:
- Downloading pirated software from warez/torrent websites should be avoided. Such a virus is commonly found in “Hack Tools” available on websites such as YouTube, pirate sites, etc.
- When feasible, use strong passwords and impose multi-factor authentication.
- Enable automatic software updates on your laptop, smartphone, and other linked devices.
- Use a reputable antivirus and internet security software package on your linked devices, such as your computer, laptop, and smartphone.
- Avoid clicking on suspicious links and opening email attachments without verifying they are legitimate.Inform staff members on how to guard against dangers like phishing and unsafe URLs.
- Block URLs like Torrent/Warez that might be used to propagate malware.To prevent malware or TAs from stealing data, keep an eye on the beacon at the network level.
Conclusion
Using YouTube bots may be a seductive strategy for content producers looking to increase their ranks and expand their viewership on the site. However, the employment of bots is typically regarded as unfair and may violate YouTube’s terms of service. Utilizing YouTube bots carries additional risk because they might be identified, which could lead to account suspension or termination for the user. Mitigating this pressing issue through awareness drives and surveys to determine the bone of contention is best. NonProfits and civil society organizations can bridge the gap between the tech giant and the end user to facilitate better know-how about these unknown bots.

Introduction
DDoS – Distributed Denial of Service Attack is one of the cyber-attacks which has been evolving at the fastest pace, the new technologies have created a blanket of vulnerability for the victim which allows the cyber criminals to stay under the radar and keep launching small scale high intensity cyber attacks. A distributed denial-of-service (DDoS) attack is a malicious attempt to disrupt the normal traffic of a targeted server, service, or network by overwhelming the target or its surrounding infrastructure with a flood of Internet traffic. DDoS attacks achieve effectiveness by utilizing multiple compromised computer systems as sources of attack traffic. Exploited machines can include computers and other networked resources such as IoT devices. From a high level, a DDoS attack is like an unexpected traffic jam clogging up the highway, preventing regular traffic from arriving at its destination.
Op Power Off
In a recent Operation by Law enforcement agencies known as Op Power Off, LEAs from United Kingdom, United States of America, Netherlands, Poland, and Germany joined hands to target the cybergroups committing such large-scale attacks which can paralyse the Internet become inaccessible for a large faction of netizens. The services collectively seized were by far the most popular DDoS booter services on the market, receiving top billing on search engines. One such service taken down had been used to carry out over 30 million attacks. As part of this action, seven administrators have been arrested so far in the United States and the United Kingdom, with further actions planned against the users of these illegal services. International police cooperation was central to the success of this operation as the administrators, users, critical infrastructure, and victims were scattered across the world. Europol’s European Cybercrime Centre coordinated the activities in Europe through its Joint Cybercrime Action Taskforce (J-CAT).
Participating Authorities
- United States: US Department of Justice (US DOJ), Federal Bureau of Investigation (FBI)
- United Kingdom: National Crime Agency (NCA)
- The Netherlands: National High Tech Crime Unit Landelijke Eenheid, Cybercrime team Midden-Nederland, Cybercrime team Noord-Holland and Cybercrime team Den Haag
- Germany: Federal Criminal Police Office (Bundeskriminalamt), Hanover Police Department (Polizeidirektion Hannover), Public Prosecutor’s Office Verden (Staatsanwaltschaft Verden)
- Poland: National Police Cybercrime Bureau (Biuro do Walki z Cyber-przestępczością)
Issue related to DDoS Attacks
DDoS booter services have effectively lowered the entry barrier into cybercrime: for a fee as low as EUR 10, any low-skilled individual can launch DDoS attacks with the click of a button, knocking offline whole websites and networks by barraging them with traffic. The damage they can do to victims can be considerable, crippling businesses financially and depriving people of essential services offered by banks, government institutions, and police forces. Emboldened by perceived anonymity, many young IT enthusiasts get involved in this seemingly low-level crime, unaware of the consequences that such online activities can carry. The influence of toolkits available on the dark net has made it easier for criminals to commit such crimes and at times even get away with it as well.
Recent examples of DDoS Attacks
- In February 2020, Amazon Web Services (AWS) suffered a DDoS attack sophisticated enough to keep its incident response teams occupied for several days also affecting customers worldwide.
- In February 2021, the EXMO Cryptocurrency exchange fell victim to a DDoS attack that rendered the organization inoperable for almost five hours.
- Recently, Australia experienced a significant, sustained, state-sponsored DDoS attack.
- Belgium also became a victim of a DDoS attack that targeted the country’s parliament, police services, and universities.
DDoS vs. DoS Attacks: What’s the Difference?
It’s important to avoid confusing a DDoS (distributed denial of service) attack with a DoS (denial of service) attack. Although only one word separates the two, these attacks vary significantly in nature.
- Strictly defined, a typical DDoS attack manipulates many distributed network devices between the attacker and the victim into waging an unwitting attack, exploiting legitimate behavior.
- A traditional DoS attack doesn’t use multiple, distributed devices, nor does it focus on devices between the attacker and the organization. These attacks also tend not to use multiple internet devices.
Conclusion
In this era of cyberspace, it is of paramount importance to maintain digital safety and security equivalent to physical safety, the cybercriminals will not stop at anything and can stoop to any level to target netizens and critical infrastructures in order to commit ransomware and malware attacks. As we can see DDoS-ing is taken seriously by law enforcement, at all levels of users, and are on the radar of law enforcement, be it a gamer booting out the competition out of a video game, or a high-level hacker carrying out DDoS attacks against commercial targets for financial gain.

Introduction
Data Breaches have taken over cyberspace as one of the rising issues, these data breaches result in personal data making its way toward cybercriminals who use this data for no good. As netizens, it's our digital responsibility to be cognizant of our data and the data of one's organization. The increase in internet and technology penetration has made people move to cyberspace at a rapid pace, however, awareness regarding the same needs to be inculcated to maximise the data safety of netizens. The recent AIIMS cyber breach has got many organisations worried about their cyber safety and security. According to the HIPPA Journal, 66% of healthcare organizations reported ransomware attacks on them. Data management and security is the prime aspect of clients all across the industry and is now growing into a concern for many. The data is primarily classified into three broad terms-
- Personal Identified Information (PII) - Any representation of information that permits the identity of an individual to whom the information applies to be reasonably inferred by either direct or indirect means.
- Non-Public Information (NPI) - The personal information of an individual that is not and should not be available to the public. This includes Social Security Numbers, bank information, other personal identifiable financial information, and certain transactions with financial institutions.
- Material Non-Public Information (MNPI) - Data relating to a company that has not been made public but could have an impact on its share price. It is against the law for holders of nonpublic material information to use the information to their advantage in trading stocks.
This classification of data allows the industry to manage and secure data effectively and efficiently and at the same time, this allows the user to understand the uses of their data and its intensity in case of breach of data. Organisations process data that is a combination of the above-mentioned classifications and hence in instances of data breach this becomes a critical aspect. Coming back to the AIIMS data breach, it is a known fact that AIIMS is also an educational and research institution. So, one might assume that the reason for any attack on AIIMS could be either to exfiltrate patient data or could be to obtain hands-on the R & D data including research-related intellectual properties. If we postulate the latter, we could also imagine that other educational institutes of higher learning such as IITs, IISc, ISI, IISERs, IIITs, NITs, and some of the significant state universities could also be targeted. In 2021, the Ministry of Home Affairs through the Ministry of Education sent a directive to IITs and many other institutes to take certain steps related to cyber security measures and to create SoPs to establish efficient data management practices. The following sectors are critical in terms of data protection-
- Health sector
- Financial sector
- Education sector
- Automobile sector
These sectors are generally targeted by bad actors and often data breach from these sectors result in cyber crimes as the data is soon made available on Darkweb. These institutions need to practice compliance like any other corporate house as the end user here is the netizen and his/her data is of utmost importance in terms of protection.Organisations in today's time need to be in coherence to the advancement in cyberspace to find out keen shortcomings and vulnerabilities they may face and subsequently create safeguards for the same. The AIIMS breach is an example to learn from so that we can protect other organisations from such cyber attacks. To showcase strong and impenetrable cyber security every organisation should be able to answer these questions-
- Do you have a centralized cyber asset inventory?
- Do you have human resources that are trained to model possible cyber threats and cyber risk assessment?
- Have you ever undertaken a business continuity and resilience study of your institutional digitalized business processes?
- Do you have a formal vulnerability management system that enumerates vulnerabilities in your cyber assets and a patch management system that patches freshly discovered vulnerabilities?
- Do you have a formal configuration assessment and management system that checks the configuration of all your cyber assets and security tools (firewalls, antivirus management, proxy services) regularly to ensure they are most securely configured?
- Do have a segmented network such that your most critical assets (servers, databases, HPC resources, etc.) are in a separate network that is access-controlled and only people with proper permission can access?
- Do you have a cyber security policy that spells out the policies regarding the usage of cyber assets, protection of cyber assets, monitoring of cyber assets, authentication and access control policies, and asset lifecycle management strategies?
- Do you have a business continuity and cyber crisis management plan in place which is regularly exercised like fire drills so that in cases of exigencies such plans can easily be followed, and all stakeholders are properly trained to do their part during such emergencies?
- Do you have multi-factor authentication for all users implemented?
- Do you have a supply chain security policy for applications that are supplied by vendors? Do you have a vendor access policy that disallows providing network access to vendors for configuration, updates, etc?
- Do you have regular penetration testing of the cyberinfrastructure of the organization with proper red-teaming?
- Do you have a bug-bounty program for students who could report vulnerabilities they discover in your cyber infrastructure and get rewarded?
- Do you have an endpoint security monitoring tool mandatory for all critical endpoints such as database servers, application servers, and other important cyber assets?
- Do have a continuous network monitoring and alert generation tool installed?
- Do you have a comprehensive cyber security strategy that is reflected in your cyber security policy document?
- Do you regularly receive cyber security incidents (including small, medium, or high severity incidents, network scanning, etc) updates from your cyber security team in order to ensure that top management is aware of the situation on the ground?
- Do you have regular cyber security skills training for your cyber security team and your IT/OT engineers and employees?
- Do your top management show adequate support, and hold the cyber security team accountable on a regular basis?
- Do you have a proper and vetted backup and restoration policy and practice?
If any organisation has definite answers to these questions, it is safe to say that they have strong cyber security, these questions should not be taken as a comparison but as a checklist by various organisations to be up to date in regard to the technical measures and policies related to cyber security. Having a strong cyber security posture does not drive the cyber security risk to zero but it helps to reduce the risk and improves the fighting chance. Further, if a proper risk assessment is regularly carried out and high-risk cyber assets are properly protected, then the damages resulting from cyber attacks can be contained to a large extent.

Cyber attacks in India besides becoming common are also getting deadlier. Each strike has taken proportions to drive home the fact that no one is safe.
Hacker ‘John Wick’, hasn’t spared India’s PM or Paytm. Cyber intelligence firm Cyble which dredges the Dark Web has red-flagged hacking episodes at Truecaller, Dunzo, Unacademy, Naukri.com, Bharat Earth Movers Limited (BEML), LimeRoad and IndiaBulls.Picture this, Mumbai-based cybersecurity firm Sequretek, says in Covid-hit 2020, India has seen a 4000% spike in phishing emails and a 400% uptake in the number of policy violations that have grown over 400% as per the latest statistics.Besides the threat to crucial data, the cost suffered by companies is phenomenal. According to a report by IBM’s ‘Cost of a Data Breach Report 2020’ report, Indian companies witnessed an average $2 Mn total cost of data breach in 2020, this is an increase of 9.4% from 2019.
Another survey by Barracuda Networks revealed that 66% of Indian organisations have had at least one data breach or cybersecurity incident since shifting to a remote working model during the pandemic.
Indian Startups At Mercy Of Cyber Attacks
More recently personal data of 2.8 Lakh WhiteHat Jr students and teachers were exposed, where crucial details of minors have been made available on the dark web. Another major breach that took place this week and exclusively reported by Inc42 was when data of 1.4 Mn job seekers was leaked when jobs portal IIMjobs was hacked.
Vineet Kumar, the founder of Cyber Peace Foundation (CPF), a think tank of cybersecurity and policy experts, said that with the increased digitisation of companies and their processes, data has become the new oil.
“You get good money when you sell users data on the dark web. Hackers discovering vulnerabilities and using SQL injections to pull entire databases remains a common practice for hacking,” Kumar told Inc42.
The CyberPeace Foundation says from mid-April to the end of June it noticed 8,98,7841 attacks, July and August saw 64,52,898 attacks. Whereas September and October saw 1,37,37,516 attacks and 18,149,233 attacks respectively.
Speaking to Inc42, Pankit Desai, cofounder and CEO, Sequretek says, “Originally only a limited set of systems were being exposed, now with WFH all systems have to be exposed to the internet as all your processes are enabled remotely. WFH also creates an additional challenge where ‘personal assets are being used for professional purposes’ and ‘professional assets are being used for personal purposes.”
Malwares like SpyMax, Blackwater are being used as a combination of phishing mails and poorly secured home computers to harvest credentials. These credentials are then used for carrying out attacks. The number of attacks with harvested credentials is already up 30%, the company revealed.
Government data shows that in 2019 alone, India witnessed 3.94 lakh instances of cybersecurity breaches. In terms of hacking of state and central government websites, Indian Computer Emergency Response Team (CERT-In) data shows that a total of 336 websites belonging to central ministries, departments, and state governments were hacked between 2017 and 2019.
According to Nasscom’s Data Security Council of India (DSCI) report 2019, India witnessed the second-highest number of cyber attacks in the world between 2016 and 2018. This comes at a time when digitisation of the Indian economy is predicted to result in a $435 Bn opportunity by 2025.On September 22, the Ministry of Electronics and Information Technology (MeITY) told the Parliament that Indian citizens, commercial and legal entities faced almost 7 lakh cyberattacks till August this year.
The Indian Computer Emergency Response Team (CERT-In) has “reported 49,455, 50,362, 53,117, 208,456, 394,499 and 696,938 cybersecurity incidents during the year 2015, 2016, 2017, 2018, 2019 and 2020 (till August) respectively,” the MeITY said while responding to an unstarred question in the Lok Sabha regarding cyberattacks on Indian citizens and India-based commercial and legal entities.“
India also lacks a cohesive nation-wide cyber-strategy, policies, and procedures. Regulations around data privacy, protection, and penalty should be enacted and enforced as these measures will help businesses evaluate their cybersecurity posture and seek ways to improve. Currently, incident reporting is not mandatory. By making it compulsory, there will be a body of research data that can provide insights on threats to India and inform the government on strategies it can undertake to strengthen the nation’s cyber posture,” said Kumar Ritesh, founder and CEO, Cyfirma.The Internet Crime Report for 2019, released by the USA’s Internet Crime Complaint Centre of the Federal Bureau of Investigation (FBI), has revealed that India stands third in the world among top 20 countries that are victims of internet crimes.
Kumar attributes these numbers to Indian’s lack of basic cyber awareness. However, a poignant point is also the lack of a robust cybersecurity policy in India. Though the issue was touched upon by Prime Minister Narendra Modi during his Independence Day speech on Aug 15, 2020, not much movement has happened on that front.
“Cybersecurity is a very important aspect, which cannot be ignored. The government is alert on this and is working on a new, robust policy,” Modi said.The PM’s announcement was made in the backdrop of the government’s initiative to connect 1.5 lakh gram panchayats through an optical fiber network, thereby increasing the country’s internet connectivity.
With India pipped to take on the world with its IT prowess and increased digital integration the need for a robust policy is now more than ever.
Source: https://inc42.com/buzz/3-94-lakhs-and-counting-how-cyberattacks-are-a-worry-for-digital-india/

Introduction
The two-day Apple’s Worldwide Developer Conference (WWDC) 2023, which was held on the 6th & 7th of June, has become an essential and highly anticipated part of our calendar as frequently as the trend. This year’s keynote announcements will include all of the usual enhancements for iOS, iPadOS, watchOS, macOS, and more. However, this year is also unique due to the unveiling of the Vision Pro headset, a brand-new Apple product.
In this blog, we will examine the exciting announcements made at Apple WWDC 2023, which was a ground-breaking event.
macOS Sonoma
macOS Sonoma, the new presentation of macOS disclosed at the WWDC full of exciting features. It comes with stunning video screensavers that show stunning scenes from all over the world. Gadgets can now be added genuinely to the work area and adjusted totally based on the client’s action. Also, it changes variety and blurring out of the spotlight while utilising applications. In addition, Death Stranding: Directors Cut for Mac announced that the Game Mode is added to make Macs more suitable for gaming. A presenter overlay enhances video presentations, and viewers can respond to them with interactive responses. Updated Safari is also included in the WebApp feature that turns frequently used websites into dedicated windows, a new Profile system for separating browsing history, and secure password sharing. Currently, the developer beta is available and the public beta will be available in July, and the final release is anticipated for the fall.
ios 16
Apple WWDC 2023 shows the following iOS, and iOS 16 replication, offering plenty of energising highlights for iPhone and iPad clients. Apple maintains its commitment to privacy with iOS 16, which introduces enhanced privacy settings that give users even more control over their data and online privacy. Users can also personalise their devices according to their preferences thanks to the new operating system’s refinement and customisable user interface.Improved multitasking capabilities like redesigned Files app and advanced note-taking features are just a few of the productivity enhancements included in the iOS 16. With iOS 16, Apple also improves its AR capabilities, allowing developers to develop even more immersive and interactive AR experiences.

WatchOS 9
Apple WWDC 2023 carried energising updates to the Apple Watch with the presentation of watchOS 9. The Apple Watch is an essential companion for sustaining a healthy lifestyle because the most recent version of the operating system includes cutting-edge health and fitness features. WatchOS 9 gives users unprecedented control over their health, offering personalised fitness recommendations and advanced sleep tracking.
Additionally, new watch faces were added, enhancing communication capabilities and improving app performance in watchOS 9, making the Apple Watch even easier to use daily.
ios 17
Rather than focusing on major features, Apple focused on quality-of-life enhancements when it announced iOS 17 at WWDC 2023. Live Voicemail with real-time transcripts of voicemails, personalised personal contact “posters,” and video voicemails for FaceTime are all part of the update. Search filters, a catch-up arrow, live location sharing, and a safety feature called Check-In are all available in Messages. AirDrop now supports NameDrop for transferring contact information; stickers have been expanded. The autocorrect and recording features on the keyboard have been improved for accuracy. Standby in the lock screen is an intelligent home display that shows the weather, upcoming appointments, and notifications. Siri works on Standby and adjusts itself for the night. The developer beta is currently available now, and a public beta will take place next month before the full release is in the fall.
Vision Pro VR Headset
Apple unveiled the Vision Pro AR headset, their first foray into virtual reality (VR), during the WWDC keynote. The Vision Pro is a virtual reality headset that competes with PlayStation VR2 and Meta Quest 3. This is in contrast to the long-awaited Apple smart glasses. Apple put a lot of effort into making a thin and light headset by using premium materials when needed. Voice, hand, and eye commands are all used to operate the Digital Crown-equipped device. The showcases offer extraordinary clarity, which is fueled by Apple’s M2 processor with a committed R1 chip. The Vision Pro combines virtual reality (VR) and augmented reality (AR), enabling users to interact with Apple apps and gain access to the company’s existing ecosystem. The expanded reality space created by the headset’s sensors and cameras allows users to place apps in real-world environments and adjust their level of concentration. Optic ID is a security and unlocking eye-tracking technology that is incorporated into the Vision Pro. It allows for a more immersive screen experience because it is compatible with Apple accessories like Magic Keyboard and Mac. At launch, the Vision Pro supports over a hundred Apple game galleries. Disney gave a hint that Apple and Disney might work together in the future by announcing support for the Vision Pro and making the Disney Plus app available immediately. The show highlighted the headset’s lightweight plan and recommended Apple clients wear it for extended periods. However, widespread adoption may be difficult due to the high price of $3,499 (₹289,093.01 approx). Apple is expected to release the Vision Pro for public use in 2024.

15-inch MacBook Air
At the WWDC event, Apple revealed a new MacBook Air with a larger 15-inch model instead of the standard 13-inch model. The 15-inch MacBook Air features a powerful Apple M2 processor, a thin, light, and long-lasting design, and a stunning 15.3-inch Retina display. It comes in four colours and has a headphone jack, two USB-C ports, and MagSafe charging. The display has six spatial speakers, a 1080p webcam, and 500 nits of brightness. Apple claims a battery life of up to 18 hours.
Conclusion
At Apple’s 2023 WWDC, the company demonstrated its commitment to developing technology that is user-friendly and accessible to all. Apple’s commitment to improving the user experience across all of its products is demonstrated in the updates to operating systems, improvements of Siri, breakthroughs in augmented reality, and enhancements to health and fitness.By making complex innovations more like-minded and easy to understand, Apple is enabling people to use the maximum capacity of their gadgets. Apple’s innovations at WWDC 2023 are expected to shape the future of technology, simplifying everyday tasks and revolutionising how we interact with the digital world.As we push ahead, it is exciting to guess what these advancements will proceed to develop and decidedly mean for our lives. The future holds even more incredible possibilities for all of us because of Apple’s focus on privacy, user-centric design, and pushing the boundaries of innovation. Thus, prepare to embrace a future where innovation flawlessly incorporates into our lives because of the endeavours displayed at Apple WWDC 2023.

Introduction
In recent years, India has witnessed a significant rise in the popularity and recognition of esports, which refers to online gaming. Esports has emerged as a mainstream phenomenon, influencing players and youngsters worldwide. In India, with the penetration of the internet at 52%, the youth has got its attracted to Esports. In this blog post, we will look at how the government is booting the players, establishing professional leagues, and supporting gaming companies and sponsors in the best possible manner. As the ecosystem continues to rise in prominence and establish itself as a mainstream sporting phenomenon in India.
Factors Shaping Esports in India: A few factors are shaping and growing the love for esports in India here. Let’s have a look.
Technological Advances: The availability and affordability of high-speed internet connections and smart gaming equipment have played an important part in making esports more accessible to a broader audience in India. With the development of smartphones and low-cost gaming PCs, many people may now easily participate in and watch esports tournaments.
Youth Demographic: India has a large population of young people who are enthusiastic gamers and tech-savvy. The youth demographic’s enthusiasm for gaming has spurred the expansion of esports in the country, as they actively participate in competitive gaming and watch major esports competitions.
Increase in the Gaming community: Gaming has been deeply established in Indian society, with many people using it for enjoyment and social contact. As the competitive component of gaming, esports has naturally gained popularity among gamers looking for a more competitive and immersive experience.
Esports Infrastructure and Events: The creation of specialised esports infrastructure, such as esports arenas, gaming cafés, and tournament venues, has considerably aided esports growth in India. Major national and international esports competitions and leagues have also been staged in India, offering exposure and possibilities for prospective esports players. Also supports various platforms such as YouTube, Twitch, and Facebook gaming, which has played a vital role in showcasing and popularising Esports in India.
Government support: Corporate and government sectors in India have recognised the potential of esports and are actively supporting its growth. Major corporate investments, sponsorships, and collaborations with esports organisations have supplied the financial backing and resources required for the country’s esports development. Government attempts to promote esports have also been initiated, such as forming esports governing organisations and including esports in official sporting events.
Growing Popularity and Recognition: Esports in India has witnessed a significant surge in viewership and fanbase, all thanks to online streaming platforms such as Twitch, YouTube which have provided a convenient way for fans to watch live esports events at home and at high-definition quality social media platforms let the fans to interact with their favourite players and stay updated on the latest esports news and events.

Esports Leagues in India
The organisation of esports tournaments and leagues in India has increased, with the IGL being one of the largest and most popular. The ESL India Premiership is a major esports event the Electronic Sports League organised in collaboration with NODWIN Gaming. Viacom18, a well-known Indian media business, established UCypher, an esports league. It focuses on a range of gaming games such as CS: GO, Dota 2, and Tekken in order to promote esports as a professional sport in India. All of these platforms provide professional players with a venue to compete and establish their profile in the esports industry.
India’s Performance in Esports to Date
Indian esports players have achieved remarkable global success, including outstanding results in prominent events and leagues. Individual Indian esports players’ success stories illustrate their talent, determination, and India’s ability to flourish in the esports sphere. These accomplishments contribute to the worldwide esports landscape’s awareness and growth of Indian esports. To add the name of the players and their success stories that have bought pride to India, they are Tirth Metha, Known as “Ritr”, a CS:GO player, Abhijeet “Ghatak”, Ankit “V3nom”, Saloni “Meow16K”.Apart from this Indian women’s team has also done exceptionally well in CS:GO and has made it to the finale.
Government and Corporate Sectors support: The Indian esports business has received backing from the government and corporate sectors, contributing to its growth and acceptance as a genuine sport.
Government Initiatives: The Indian government has expressed increased support for esports through different initiatives. This involves recognising esports as an official sport, establishing esports regulating organisations, and incorporating esports into national sports federations. The government has also announced steps to give financial assistance, subsidies, and infrastructure development for esports, therefore providing a favourable environment for the industry’s growth. Recently, Kalyan Chaubey, joint secretary and acting CEO of the IOA, personally gave the athletes cutting-edge training gear during this occasion, providing kits to the players. The kit includes the following:
Advanced gaming mouse.
Keyboard built for quick responses.
A smooth mousepad
A headphone for crystal-clear communication
An eSports bag to carry the equipment.
Corporate Sponsorship and Partnerships
Indian corporations have recognised esports’ promise and actively sponsored and collaborated with esports organisations, tournaments, and individual players. Companies from various industries, including technology, telecommunications, and entertainment, have invested in esports to capitalise on its success and connect with the esports community. These sponsorships and collaborations give financial support, resources, and visibility to esports in India. The leagues and championships provide opportunities for young players to showcase their talent.
Challenges and future
While esports provides great job opportunities, several obstacles must be overcome in order for the industry to expand and gain recognition:
Infrastructure & Training Facilities: Ensuring the availability of high-quality training facilities and infrastructure is critical for developing talent and allowing players to realise their maximum potential. Continued investment in esports venues, training facilities, and academies is critical for the industry’s long-term success.
Fostering a culture of skill development and giving outlets for formal education in esports would improve the professionalism and competitiveness of Indian esports players. Collaborations between educational institutions and esports organisations can result in the development of specialised programs in areas such as game analysis, team management, and sports psychology.
Establishing a thorough legal framework and governance structure for esports will help it gain legitimacy as a professional sport. Clear standards on player contracts, player rights, anti-doping procedures, and fair competition policies are all part of this.
Conclusion
Esports in India provide massive professional opportunities and growth possibilities for aspiring esports athletes. The sector’s prospects are based on overcoming infrastructure, perception, talent development, and regulatory barriers. Esports may establish itself as a viable and acceptable career alternative in India with continued support, investment, and stakeholder collaboration

BharOS’s successful testing grabbed massive online attention after Ashwini Vaishnaw, Minister of Communications and Electronics & IT, and Union Education Minister Dharmendra Pradhan unveiled the new mobile operating system. On Data Privacy Day, January 28, it’s appropriate to discuss the safety factors.
The OS is developed by JandKops, which has been incubated by IIT Madras Pravartak Technologies Foundation. It is claimed that BharOS will ensure the prevention of the “execution of any malware” and “execution of any malicious application”.
Even though it is called a Made in India OS, there are many people who disagree with this. It is because the OS is based on an AOSP (Android Open Source Project). It includes similar methodologies, functionalities, and basics used in Google Android.
Global safety factor
Security and data safety has been worldwide issue. A few years ago, Alphabet CEO Sundar Pichai also testified in front of US Congress while facing questions related to privacy, data collection, and location tracking.
While experts say that Android’s app ecosystem is a privacy and security disaster, a study that examined 82,501 apps pre-installed on 1,742 Android smartphones sold by 214 vendors concluded that users are woefully unaware of the significant security and privacy risks posed by pre-installed applications.
Even Apple, which takes cybersafety issues as a top priority, sometimes finds itself in a vulnerable situation. For example, last year Apple users were advised to update their devices to protect against a pair of security flaws that could allow attackers to take complete control.
It was said that one of the software flaws affected the kernel, the deepest layer of the OS shared by all Apple devices, while the other had an impact on WebKit, the technology that powers the Safari web browser.
Security researchers, including NordVPN, said that Apple’s closed development OS makes it more difficult for hackers to develop exploits, while Android raises the threat level since anyone can see its source code to develop exploits.
BharOS is not like iOS but it is kind of similar to Android and based on AOSP. So the question is, how safe would this OS be?
‘Security blanket’
Sandip Kumar Panda, Co-founder and CEO of InstaSafe, told News18: “BharOS acts as a security blanket for devices. The framework is designed in a manner that it prevents the execution of any malicious app and verifies each app on the devices before making it live on the BharOS platform.”
There are no apps without any vulnerabilities, he said. “As the app development progresses, vulnerabilities get introduced either in the form of insecure coding practices or third-party software vulnerabilities integrated with the platform. Since several Android vulnerabilities were discovered over the years, all those bugs would have been fixed now and updates would already have been for AOSP, which will be much more mature now,” he added.
Vineet Kumar, Founder and President of CyberPeace Foundation, believes that “the use of AOSP as the foundation for BharOS is a positive step” as it is a robust platform.
But according to him, it is important to note that no OS can be completely immune to all forms of cyber threats. “The key to staying safe online is to stay vigilant, use security software, keep your software updated, and be mindful of the apps you install and the websites you visit,” he said,
Furthermore, the expert stated that it is possible to make an OS more secure by implementing a variety of security features and technologies such as sandboxing, whitelisting, and application control, as well as rigorous testing and code review processes.
Kumar said: “It would be important for an independent, reputable security firm to evaluate BharOS and test its security features before it can be stated with certainty that it is more secure than other OSs.”
It is difficult to say whether the BharOS will be free of cybersecurity issues without more information about the specific features and security measures that have been implemented, he noted while adding that this OS has to go through a rigorous testing and certification process.
“It will be important to see how it measures up against established security standards and how well it can withstand real-world attacks,” the expert stated.
Reference Link : https://www.news18.com/amp/news/tech/data-privacy-day-how-safe-is-bharos-what-do-cybersecurity-experts-say-you-are-about-to-find-out-6932521.html

Introduction
The world has been surfing the wave of technological advancements and innovations for the past decade, and it all pins down to one device – our mobile phone. For all mobile users, the primary choices of operating systems are Android and iOS. Android is an OS created by google in 2008 and is supported by most brands like – One+, Mi, OPPO, VIVO, Motorola, and many more and is one of the most used operating systems. iOS is an OS that was developed by Apple and was introduced in their first phone – The iPhone, in 2007. Both OS came into existence when mobile phone penetration was slow globally, and so the scope of expansion and advancements was always in favor of such operating systems.
The Evolution
iOS
Ever since the advent of the iPhone, iOS has seen many changes since 2007. The current version of iOs is iOS 16. However, in the course of creating new iOS and updating the old ones, Apple has come out with various advancements like the App Store, Touch ID & Face ID, Apple Music, Podcasts, Augmented reality, Contact exposure, and many more, which have later become part of features of Android phone as well. Apple is one of the oldest tech and gadget developers in the world, most of the devices manufactured by Apple have received global recognition, and hence Apple enjoys providing services to a huge global user base.
Android
The OS has been famous for using the software version names on the food items like – Pie, Oreo, Nougat, KitKat, Eclairs, etc. From Android 10 onwards, the new versions were demoted by number. The most recent Android OS is Android 13; this OS is known for its practicality and flexibility. In 2012 Android became the most popular operating system for mobile devices, surpassing Apple’s iOS, and as of 2020, about 75 percent of mobile devices run Android.
Android vs. iOS
1. USER INTERFACE
One of the most noticeable differences between Android and iPhone is their user interface. Android devices have a more customizable interface, with options to change the home screen, app icons, and overall theme. The iPhone, on the other hand, has a more uniform interface with less room for customization. Android allows users to customize their home screen by adding widgets and changing the layout of their app icons. This can be useful for people who want quick access to certain functions or information on their home screen. IOS does not have this feature, but it does allow users to organize their app icons into folders for easier navigation.
2. APP SELECTION
Another factor to consider when choosing between Android and iOS is the app selection. Both platforms have a wide range of apps available, but there are some differences to consider. Android has a larger selection of apps overall, including a larger selection of free apps. However, some popular apps, such as certain music streaming apps and games, may be released first or only available on iPhone. iOS also has a more curated app store, meaning that all apps must go through a review process before being accepted for download. This can result in a higher quality of apps overall, but it can also mean that it takes longer for new apps to become available on the platform. iPhone devices tend to have less processing power and RAM. But they are generally more efficient in their use of resources. This can result in longer battery life, but it may also mean that iPhones are slower at handling multiple tasks or running resource-intensive apps.
3. PERFORMANCE
When it comes to performance, both Android and iPhone have their own strengths and weaknesses. Android devices tend to have more processing power and RAM. This can make them faster and more capable of handling multiple tasks simultaneously. However, this can also lead to Android devices having shorter battery life compared to iPhones.
4. SECURITY
Security is an important consideration for any smartphone user, and Android and iPhone have their own measures to protect user data. Android devices are generally seen as being less secure than iPhones due to their open nature. Android allows users to install apps from sources other than the Google Play Store, which can increase the risk of downloading malicious apps. However, Android has made improvements in recent years to address this issue. Including the introduction of Google Play Protect, which scans apps for malware before they are downloaded. On the other hand, iPhone devices have a more closed ecosystem, with all apps required to go through Apple‘s review process before being available for download. This helps reduce the risk of downloading malicious apps, but it can also limit the platform’s flexibility.
Conclusion
The debate about the better OS has been going on for some time now, and it looks like it will get more comprehensive in the times to come, as netizens go deeper into cyberspace, they will get more aware and critical of their uses and demands, which will allow them to opt for the best OS for their convenience. Although the Andriod OS, due to its integration, stands more vulnerable to security threats as compared to iOS, no software is secure in today’s time, what is secure is its use and application hence the netizen and the platforms need to increase their awareness and knowledge to safeguard themselves and the wholesome cyberspace.

Introduction
Established in the US, one of the world’s largest cab networks came into existence in 2010 and, since its inception, has expanded all over the globe with operations in 10,000 cities across 71 countries. It made a remarkable start in India in 2017 and, since then, has seen a rise in the customers and drivers for the company. India is among the largest markets for Uber, with 600,000 monthly drivers and 8.5 million monthly riders.
GeM
Government e-Marketplace (GeM) is a one-stop portal to facilitate online procurement of common-use Goods & Services required by various Government Departments / Organizations / PSUs. GeM aims to enhance transparency, efficiency and speed in public procurement. It provides the tools of e-bidding, reverses e-auction and demand aggregation to facilitate government users achieve the best value for their money. Government e-Marketplace owes its genesis to the recommendations of two Groups of Secretaries to the Prime Minister in January 2016. They recommended setting up a dedicated e-market for different goods & services procured or sold by Government/PSUs besides reforming DGS&D. Subsequently, the Finance Minister, in his Budget speech for FY 2016-17, announced setting up of a technology-driven platform to facilitate procurement of goods and services by various Ministries and agencies of the Government. The portal was launched on 9th August 2016 by the Commerce & Industry Minister.
Uber-GeM collaboration
The cab network giant has registered on the portal of the Government E-marketplace and has declared that it will offer its services to Government officials from Ministries and PSUs. The project is currently in its pilot phase and shall be executed systematically to cover all the ministries and PSUs in the nation. The officials can book cabs at a fixed price with no cancellation or surge fees on the rides. The authorised officials will be able to book a cab from the portal and select from the list of drivers available. It will be a cashless/cardless ride for the officials; additional vehicle categories for government riders have been added, namely, GeM Yatraa Hatch and GeM Yatraa Sedan, and there will be hourly rentals for multiple-stops, allowing the government officials to enjoy the flexible and easily accessible network of cabs in major cities.
Advantages
Such collaboration between Government institutions and corporates will go a long way to secure a stable equilibrium in the market. Uber, a US-based company, enjoys a vast user base in India and has created new job avenues. The advantages of the collaboration between GeM and Uber are as follows-
Easy accessibility
This will undoubtedly provide ease in accessibility in terms of being in a new place, and language barriers will no longer exist with such options for Government officials.
Increased jobs for drivers
With more cabs being engaged with ministries and PSUs, it is pertinent that the requirement for drivers will grow, thus increasing the employability rate in India and allowing the user to have an uninterrupted experience.
Ease of travel and commuting
This move will provide flexibility, thus leading to more ease in travel in cases of emergencies or places inaccessible by trains or other modes of transport.
Rise in travel and tourism
Coupled with the other factors, the opportunities for the users to visit different places will be an added advantage which will help boost the tourism industry, thus creating a balance in the market.
Sustainable Government corporate relationship

Such collaborations between the government and corporates will be substantial, signifying the ease of doing business in India. They will also act as a beacon of example for compliance with opportunities for the other companies and stakeholders.
Opportunities for collaboration with ingenious start-ups
With such major corporate joining hands with the government, the indigenous start-ups will have various opportunities to engage with companies and recreate similar businesses rooted in India, thus transforming the economy.
Conclusion
Transportation and communication play a vital role in our lives, thus, such collaboration will go a long way in creating a better and more uniform user experience in the country. This also goes a long way to showcase that the Governmental platforms also offer services of a global standard. Such portals exist in South Korea, Singapore, the US and Europe. The network of cabs can only be sustained using the locals as drivers, hence these collaborations are win-win for all as the market dynamics are improving, employability will increase, and improved user experience will be seen.

THREE CENTRES OF EXCELLENCE IN ARTIFICIAL INTELLIGENCE:
India’s Finance Minister, Mrs. Nirmala Sitharaman, with a vision of ‘Make AI for India’ and ‘Make AI work for India, ’ announced during the presentation of Union Budget 2023 that the Indian Government is planning to set up three ‘Centre of Excellence’ for Artificial Intelligence in top Educational Institutions to revolutionise fields such as health, agriculture, etc.
Under the ‘Amirt Kaal,’ i.e., the budget of 2023 is a stepping stone by the government to have a technology-driven knowledge-based economy and the seven priorities that have been set up by the government called ‘Saptarishi’ such as inclusive development, reaching the last mile, infrastructure investment, unleashing potential, green growth, youth power, and financial sector will guide the nation in this endeavor along with leading industry players that will partner in conducting interdisciplinary research, developing cutting edge applications and scalable problem solutions in such areas.
The government has already formed the roadmap for AI in the nation through MeitY, NASSCOM, and DRDO, indicating that the government has already started this AI revolution. For AI-related research and development, the Centre for Artificial Intelligence and Robotics (CAIR) has already been formed, and biometric identification, facial recognition, criminal investigation, crowd and traffic management, agriculture, healthcare, education, and other applications of AI are currently being used.
Even a task force on artificial intelligence (AI) was established on August 24, 2017. The government had promised to set up Centers of Excellence (CoEs) for research, education, and skill development in robotics, artificial intelligence (AI), digital manufacturing, big data analytics, quantum communication, and the Internet of Things (IoT) and by announcing the same in the current Union budget has planned to fulfill the same.
The government has also announced the development of 100 labs in engineering institutions for developing applications using 5G services that will collaborate with various authorities, regulators, banks, and other businesses.
Developing such labs aims to create new business models and employment opportunities. Among others, it will also create smart classrooms, precision farming, intelligent transport systems, and healthcare applications, as well as new pedagogy, curriculum, continual professional development dipstick survey, and ICT implementation will be introduced for training the teachers.
POSSIBLE ROLES OF AI:
The use of AI in top educational institutions will help students to learn at their own pace, using AI algorithms providing customised feedback and recommendations based on their performance, as it can also help students identify their strengths and weaknesses, allowing them to focus their study efforts more effectively and efficiently and will help train students in AI and make the country future-ready.
The main area of AI in healthcare, agriculture, and sustainable cities would be researching and developing practical AI applications in these sectors. In healthcare, AI can be effective by helping medical professionals diagnose diseases faster and more accurately by analysing medical images and patient data. It can also be used to identify the most effective treatments for specific patients based on their genetic and medical history.
Artificial Intelligence (AI) has the potential to revolutionise the agriculture industry by improving yields, reducing costs, and increasing efficiency. AI algorithms can collect and analyse data on soil moisture, crop health, and weather patterns to optimise crop management practices, improve yields and the health and well-being of livestock, predict potential health issues, and increase productivity. These algorithms can identify and target weeds and pests, reducing the need for harmful chemicals and increasing sustainability.
ROLE OF AI IN CYBERSPACE:
Artificial Intelligence (AI) plays a crucial role in cyberspace. AI technology can enhance security in cyberspace, prevent cyber-attacks, detect and respond to security threats, and improve overall cybersecurity. Some of the specific applications of AI in cyberspace include:
- Intrusion Detection: AI-powered systems can analyse large amounts of data and detect signs of potential cyber-attacks.
- Threat Analysis: AI algorithms can help identify patterns of behaviour that may indicate a potential threat and then take appropriate action.
- Fraud Detection: AI can identify and prevent fraudulent activities, such as identity theft and phishing, by analysing large amounts of data and detecting unusual behaviour patterns.
- Network Security: AI can monitor and secure networks against potential cyber-attacks by detecting and blocking malicious traffic.
- Data Security: AI can be used to protect sensitive data and ensure that it is only accessible to authorised personnel.
CONCLUSION:
Introducing AI in top educational institutions and partnering it with leading industries will prove to be a stepping stone to revolutionise the development of the country, as Artificial Intelligence (AI) has the potential to play a significant role in the development of a country by improving various sectors and addressing societal challenges. Overall, we hope to see an increase in efficiency and productivity across various industries, leading to increased economic growth and job creation, improved delivery of healthcare services by increasing access to care and, improving patient outcomes, making education more accessible and effective as AI has the potential to improve various sectors of a country and contribute to its overall development and progress. However, it’s important to ensure that AI is developed and used ethically, considering its potential consequences and impact on society.
References:

Introduction
It’s a proud moment for Indians that India will host the G- 20 administration, which will bring the world’s 20 largest profitable nations together on a single platform during the post-economic recovery and the Russia- Ukraine conflict, which has increased geopolitical pressures among nations over the last many times and made the G- 20 a precedence of nations. With this administration, India has to make cybersecurity precedence, as the security and integrity of the critical structure and digital platforms are top precedence in 2023. The necessity for a secure cyberspace is pivotal given the exponential increase in the volume and kind of cyber-attacks, particularly to crucial structures the most recent illustration is the ongoing interruption at New Delhi’s All India Institute of Medical lores caused by a ransomware assault. It has been observed that the mode of attacks are more sophisticated and targets communication structure, critical structure, transport systems, and especially the information technology sector and fiscal system.
The structure that enables the delivery of government services to be more effective. As a result,cyber-secured critical structures and digital public forums are necessary for public security, bettered governance, and, most importantly, maintaining people’s trust. The G20 can be enhanced and contribute towards securing digital public platforms and the integrity of the critical structure. This time, in 2023, digital security is the top precedence.
G20 cybersecurity enterprises and politic sweat
The emphasis on cybersecurity was maintained throughout the Italian and Indonesian regulations in 2021 and 2022, independently, by emphasizing the significance of cyberspace during Digital Economy Working Group addresses. Specifically, under the Indonesian Presidency, the prominent cybersecurity focus was clear in the recent Bali Leaders’ protestation, which noted, among other effects, the significance of fighting misinformation juggernauts and cyber attacks, as well as guaranteeing connectivity structure security. The cyber incident report by the Financial Stability Board on carrying further uniformity in cyber incident reporting In 2016, a G20 digital task force was created under the Chinese administration to understand digital technology issues. Under the Saudi administration, the cybersecurity gap at the G20 was bridged by addressing the issues of MSMs. India has also refocused on the significance of creating secure, secure, and stronger-friendly digital platforms.
G20- India’s digital invention alliance( G-20-DIA) a cyber-secure Bharat
- Under India’s administration, the G20’s Digital Economy Working Group is led by the Ministry of Electronics and Information Technology( MeitY, DEWG).
- The Ministry concentrated on three major areas during India’s G20 administration digital skill development, digital public structure, and cyber security.
- The EWG’s DIA and Stay Safe Online enterprise further the ideal of lesser digital metamorphosis by guaranteeing a safe and creative cyber terrain. They want to offer a smooth and secure delivery of public services.

The G20 Digital Innovation Alliance
(G20- DIA) strives to find, admit, and encourage the relinquishment of innovative and poignant digital technologies produced by invited G20 startups and-member governments.
- These technologies must meet humanity’s conditions in six crucial areas husbandry, health, education, finance, secure digital structure, and indirect frugality.
- The inventions created around these motifs will be supported by the Digital Public Goods structure, allowing them to be espoused encyclopedically, closing the digital gap and icing sustainable and indifferent growth.
- The G20 Digital Innovation Alliance( G20- DIA) conference will be held on the perimeters of the Digital Economy Working Group( DEWG) meeting in Bengaluru.
- Top-nominated entrepreneurs from each order will present their ideas to a worldwide community of investors, instructors, pots, and other stakeholders at this event.
India’s” Stay Safe Online crusade”
The” Stay Safe Online” crusade attempts to raise mindfulness about the significance of remaining safe in the online world amid our adding reliance on it. With the fast expansion of the technical terrain and the growing number of internet druggies in India, new difficulties are arising. The Stay Safe Online crusade aims to educate individuals about cyber pitfalls and how to avoid them. The time-long crusade will target children, women, scholars, and aged citizens, as well as individuals with disabilities, preceptors, and government officers in particular. It’ll be done in Hindi, English, and indigenous languages to reach a larger followership. It’ll distribute mindfulness information in infographics, short pictures, cartoon stories, and so on through extensively employed social media platforms and other channels. The primary stakeholders will be government agencies, civil societies, and NGOs.
Conclusion
To wind up, it can be said that cyber security has become the most essential part of transnational affairs. As India hosts the G20 administration in 2023, the docket relating to cybersecurity gains a global stage, where cyber-related issues are addressed and honored encyclopedically, and nations can combat these issues; also, India aims to raise cyber mindfulness among its citizens.

Introduction
The year, 2022 has been a year of transition and change for the gaming industry. This year esports and gaming including the industry’s greater increased acceptance by the sports authorities and higher prize pools for top players, has been more commercial than ever, according to research by the year 2025 the industry will witness growth by 5 million dollars and around 420 million active gamers from India. Since, India is on the way to become world’s largest gaming market, with revenue earned in 2021 increasing by up to 28%, or 1.2 billion dollars, and predicted to reach 2 billion dollars by 2024 as a result of the COVID-19 expanding internet access throughout the country.
After a lengthy debate, the government has finally decided to bring online gaming under the purview of the law. The President of India has changed the rules governing e-sports and requested that the Sports Ministry and the Ministry of Electronics and Information Technology (MeitY) include e-sports in multi-sport competitions. India’s gaming sector has reached new heights this year, with the country winning its first bronze medal in the first esports event organized by this year’s Commonwealth Games, and this is only the beginning.
Indian government takes on E-sports
The Indian government has given esports a huge boost. It has been introduced into the traditional sports disciplines of the nation. Droupadi Murmu, the President of India, changed the regulations governing eSports using the authority “conferred by clause (3) of Article 77 of the Constitution,” and requested that “e-Sports be included as part of multi-sports events” from the Ministries of Electronics and Information Technology and Sports. Some crucial points will clarify the government’s position on e-sports.
- E-sports were added as a demonstration sport to the 2018 Asian Games in Jakarta, which meant that medals earned in the sport were not counted in the official total of medals.
- There is a greater desire for Esports to be integrated with school curricula.
- E-Sports (Electronic Sports) have been acknowledged by the Indian government as a component of multi-sport tournaments.

Why is e-sports important?
The Indian Esports Industry has worked hard to distinguish Esports from the broader category of “Gaming.” Esports is a competitive sport in which esports athletes compete in specific video game genres in a virtual, electronic environment using their physical and mental prowess, according to the industry.
According to studies, as individuals have gotten more screen aware and online gaming has become a part of their life, internet gaming not only improves fine motor skills but also sharpens the mind. The industry has the most users and stakeholders, and it has become critical to governing it; consequently, legislation is required to regulate it.
The online regulation bill 2022
The Online Gaming (Regulations) Bill, 2022, was recently filed in the Lok Sabha to create an effective regulatory mechanism for the online gaming business to prevent fraud and misuse of things related to or incidental to it. There are 20 sections spread throughout three chapters. It intends to establish an Online Gaming Commission, the authority, mandate, and jurisdiction of which will be specified by the Bill. An online gaming server will be licensed, relinquished, revoked, or suspended by the Commission’s key highlights of the bill to make it more clear
- The Bill establishes a regulating agency, the Online Gaming Commission (“OGC”), comprised of five members chosen by the Central Government, each with at least one specialist in the fields of law, cyber technology, and law enforcement experience.
- The OGC will be able to oversee the functions of online gaming websites, issue periodic or special reports on Online Gaming issues, recommend appropriate measures to control and curb illegal Online Gaming, grant, suspend, and revoke licenses for online gaming websites, and set fees for license applications and renewals.
- Without a website and a non-transferable and non-assignable license, the Bill proposes to make online gambling illegal. Anyone operating an online gaming server or website without a license risks up to three years in prison and a fine. The permission will be good for a six-year term.
- The license intended to be given under the Bill may be terminated or canceled if the licensee violates any of the license’s requirements or any of Bill’s provisions. However, the Bill does not apply to anybody providing backend services in India, including hosting and maintenance for any international gaming website situated outside of India.
- The bill also mentions the Foreign Direct Investment and Technology Collaboration in Online Gaming

Few misses in the bill that can be addressed to make it stronger and a better version
- The law does not address Know Your Customer (KYC) requirements, customer complaint procedures, advertising and marketing restrictions, user data protection, responsible gaming guidelines, and other concerns.
- In the bill, there is no clear distinction between money involved in the game. This is a matter of concern and needs to be addressed so the money laundering aspect can be determined.
- The distinction between “games of chance” and “games of skill” is not addressed in the Bill. Furthermore, the Bill does not specify whether its prohibitions apply only to for-real-money games or to free games.
Conclusion
Despite the bill’s flaws, it has offered optimism to the burgeoning gaming sector, which desperately needs a robust regulatory and legal framework free of ambiguity, allowing players to play safely, and encouraging entrepreneurs to enter the field with safety and security. An improved regulatory framework will increase job prospects while also assisting the government. A transparent framework will also aid in the protection of the rights of actors and stakeholders.

Introduction
With the increasing reliance on digital technologies in the banking industry, cyber threats have become a significant concern. Cyberlaw plays a crucial role in safeguarding the banking sector from cybercrimes and ensuring the security and integrity of financial systems.
The banking industry has witnessed a rapid digital transformation, enabling convenient services and greater access to financial resources. However, this digitalisation also exposes the industry to cyber threats, necessitating the formulation and implementation of effective cyber law frameworks.
Recent Trends in the Banking Industry
Digital Transformation: The banking industry has embraced digital technologies, such as mobile banking, internet banking, and financial apps, to enhance customer experience and operational efficiency.
Open Banking: The concept of open banking has gained prominence, enabling data sharing between banks and third-party service providers, which introduces new cyber risks.

How Cyber Law Helps the Banking Sector
The banking sector and cyber crime share an unspoken synergy due to the mass digitisation of banking services. Thanks to QR codes, UPI and online banking payments, India is now home to 40% of global online banking transactions. Some critical aspects of the cyber law and banking sector are as follows:
Data Protection: Cyberlaw mandates banks to implement robust data protection measures, including encryption, access controls, and regular security audits, to safeguard customer data.
Incident Response and Reporting: Cyberlaw requires banks to establish incident response plans, promptly report cyber incidents to regulatory authorities, and cooperate in investigations.
Customer Protection: Cyberlaw enforces regulations related to online banking fraud, identity theft, and unauthorised transactions, ensuring that customers are protected from cybercrimes.
Legal Framework: Cyberlaw provides a legal foundation for digitalisation in the banking sector, assuring customers that regulations protect their digital transactions and data.
Cybersecurity Training and Awareness: Cyberlaw encourages banks to conduct regular training programs and create awareness among employees and customers about cyber threats, safe digital practices, and reporting procedures.

RBI Guidelines
The RBI, as India’s central banking institution, has issued comprehensive guidelines to enhance cyber resilience in the banking industry. These guidelines address various aspects, including:
Technology Risk Management
Cyber Security Framework
IT Governance
Cyber Crisis Management Plan
Incident Reporting and Response
Recent Trends in Banking Sector Frauds and the Role of Cyber Law
Phishing Attacks: Cyberlaw helps banks combat phishing attacks by imposing penalties on perpetrators and mandating preventive measures like two-factor authentication.
Insider Threats: Cyberlaw regulations emphasise the need for stringent access controls, employee background checks, and legal consequences for insiders involved in fraudulent activities.
Ransomware Attacks: Cyberlaw frameworks assist banks in dealing with ransomware attacks by enabling legal actions against hackers and promoting preventive measures, such as regular software updates and data backups.
Master Directions on Cyber Resilience and Digital Payment Security Controls for Payment System Operators (PSOs)
Draft of Master Directions on Cyber Resilience and Digital Payment Security Controls for Payment System Operators (PSOs) issued by the Reserve Bank of India (RBI). The directions provide guidelines and requirements for PSOs to improve the safety and security of their payment systems, with a focus on cyber resilience. These guidelines for PSOs include mobile payment service providers like Paytm or digital wallet payment platforms.
Here are the highlights-
The Directions aim to improve the safety and security of payment systems operated by PSOs by providing a framework for overall information security preparedness, with an emphasis on cyber resilience.
The Directions apply to all authorised non-bank PSOs.
PSOs must ensure adherence to these Directions by unregulated entities in their digital payments ecosystem, such as payment gateways, third-party service providers, vendors, and merchants.
The PSO’s Board of Directors is responsible for ensuring adequate oversight over information security risks, including cyber risk and cyber resilience. A sub-committee of the Board may be delegated with primary oversight responsibilities.
PSOs must formulate a Board-approved Information Security (IS) policy that covers roles and responsibilities, measures to identify and manage cyber security risks, training and awareness programs, and more.
PSOs should have a distinct Board-approved Cyber Crisis Management Plan (CCMP) to detect, contain, respond, and recover from cyber threats and attacks.
A senior-level executive, such as a Chief Information Security Officer (CISO), should be responsible for implementing the IS policy and the cyber resilience framework and assessing the overall information security posture of the PSO.
PSOs need to define Key Risk Indicators (KRIs) and Key Performance Indicators (KPIs) to identify potential risk events and assess the effectiveness of security controls. The sub-committee of the Board is responsible for monitoring these indicators.
PSOs should conduct a cyber risk assessment when launching new products, services, technologies, or significant changes to existing infrastructure or processes.
PSOs, including inventory management, identity and access management, network security, application security life cycle, security testing, vendor risk management, data security, patch and change management life cycle, incident response, business continuity planning, API security, employee awareness and training, and other security measures should implement various baseline information security measures and controls.
PSOs should ensure that payment transactions involving debit to accounts conducted electronically are permitted only through multi-factor authentication, except where explicitly permitted/relaxed.

Conclusion
The relationship between cyber law and the banking industry is crucial in ensuring a secure and trusted digital environment. Recent trends indicate that cyber threats are evolving and becoming more sophisticated. Compliance with cyber law provisions and adherence to guidelines such as those provided by the RBI is essential for banks to protect themselves and their customers from cybercrimes. By embracing robust cyber law frameworks, the banking industry can foster a resilient ecosystem that enables innovation while safeguarding the interests of all stakeholders or users.

Introduction
The insurance industry is a target for cybercriminals due to the sensitive nature of the information it holds. This makes it essential for insurance companies to have robust cybersecurity measures to protect their data and customers’ personal information.
Cyber fraud in India’s insurance industry is increasing. It is reported that the Indian insurance sector has witnessed a surge in cyber-attacks, with several instances of data breaches, identity thefts, and financial fraud being reported. These cybercrimes not only pose a significant threat to the financial stability of the insurance industry but also to the privacy and security of policyholders.
Cyber Frauds in the Insurance Industry
The insurance industry in India has been the target of increasing cyber fraud in recent years. With the growing digital transformation trend, insurance companies have become increasingly vulnerable to cyber-attacks. Cyber frauds in the insurance industry are initiated by hackers who use various techniques such as phishing, malware, ransomware, and social engineering to gain unauthorised access to policyholders’ personal data and sensitive information
Kinds of cyber frauds in the insurance industry
It is essential for insurers and policyholders alike to be aware of these kinds of cyber-attacks on insurance companies in today’s digital age. Staying educated about these threats can help prevent them from happening in the future.
Identity theft– One common type of cyber fraud that occurs in the insurance industry is identity theft. In this type of fraud, criminals steal personal information such as name, address, date of birth and social security numbers through phishing emails or fraudulent websites. They then use this information to open fraudulent policies or access existing ones.
Payment fraud- Another type of cyber fraud that is on the rise is payment fraud. In this type of fraud, hackers intercept electronic payments made by policyholders or agents using fake bank accounts or compromised payment gateways. The money is then siphoned into untraceable accounts, making it difficult for law enforcement agencies to identify and arrest the perpetrators.
Phishing attacks- Where the fraudsters posed as company officials and sent emails to policyholders requesting their account details. The unsuspecting customers fell for this scam and shared their sensitive information, which was then used to access their accounts and steal funds.
Hacking- Where hackers breach the company’s system to gain access to policyholder data. The hackers’ stoles personal records, including names, addresses, phone numbers, social security numbers, and financial information, which they later sell on the dark web.
Fake policies scam- Fraudsters create fake policies using stolen identities and collect premiums from innocent customers. The insurer then voided these policies due to fraudulent activity leaving those people without valid coverage when they needed it most. The victims suffer significant financial losses due to this scam.
Fake Insurance Websites- Discuss the creation of deceptive websites that imitate well-known insurance companies, where unsuspecting individuals provide their personal details, leading to identity theft or financial losses.

Prevention of Cyber Frauds in the Insurance Industry- Best practices to follow
Prevention is better than cure, which also holds true in the case of cyber fraud in the insurance industry. The industry must take proactive steps to prevent such frauds from occurring in the first place. One of the most effective ways to do so is by investing in cybersecurity measures that are specifically designed for the insurance sector.
Insurance companies must conduct regular employee training programs on cybersecurity best practices. This includes educating employees on how to identify and avoid phishing emails, create strong passwords, and recognise potential cyber threats. Companies should also establish a reporting mechanism for employees to report suspicious activity or incidents immediately.
Having proper access controls in place is also necessary. This means limiting access to sensitive data only to those employees who need it, implementing two-factor authentication, and regularly monitoring user activity logs. Regular audits can also provide an extra layer of protection against potential threats by identifying vulnerabilities that may have been overlooked during routine security checks.
Another essential step is encrypting all data transmitted between different systems and devices. Encryption scrambles data into unreadable codes that can only be deciphered using a decryption key, making it difficult for hackers to intercept or steal information in transit.
Legal Framework for Cyber Frauds in the Insurance Industry
The legal framework for cyber fraud in the insurance industry is critical to preventing such crimes. The Insurance Regulatory and Development Authority of India (IRDAI) has issued guidelines for insurers to establish a cybersecurity framework. The guidelines require insurers to conduct regular risk assessments, implement security measures, and ensure compliance with data privacy laws.
The Information Technology Act 2000, is another significant piece of legislation dealing with cyber fraud in India. The act defines offences such as unauthorised access to a computer system, hacking, and tampering with data. It also provides for stringent penalties and imprisonment for those found guilty of such offences.
The IRDAI’s guidelines provide insurers with a roadmap to establish robust cybersecurity measures to help prevent cyber fraud in the insurance industry. Stringent implementation of these guidelines will go a long way in safeguarding sensitive customer information from falling into the wrong hands.
Best Practices for Insurers and Policyholders
Insurers:
Implementing Strong Authentication: Encouraging the use of multi-factor authentication and secure login processes to safeguard customer accounts and prevent unauthorised access.
Regular Employee Training: Conduct cybersecurity awareness programs to educate employees about the latest threats and preventive measures.
Investing in Advanced Technologies: Utilizing robust cybersecurity tools and systems to promptly detect and mitigate potential cyber threats.
Policyholders:
Vigilance and Awareness: Policyholders must stay vigilant while sharing personal information online and verify the authenticity of insurance websites and communication channels.
Regular Updates and Patches: Advising individuals to keep their devices and software up to date to minimise vulnerabilities that cybercriminals can exploit.
Secure Online Practices: Encouraging the use of strong and unique passwords, avoiding sharing sensitive information on unsecured networks, and exercising caution when clicking on suspicious links or attachments.

Conclusion
As the Indian insurance industry embraces digitisation, the risk of cyber scams and data breaches becomes a significant concern. Insurers and policyholders must collaborate to ensure robust cybersecurity measures are in place to protect sensitive information and financial interests.
It is essential for insurance companies to invest in robust cybersecurity measures that can detect and prevent fraud attempts. Additionally, educating employees on the dangers of cyber fraud and implementing strict compliance measures can go a long way in mitigating risks. With these efforts, the insurance industry can continue to provide trustworthy and reliable services to its customers while protecting against cyber threats. As technology continues to evolve, it is imperative that the insurance industry adapts accordingly and remains vigilant against emerging threats.

Introduction
The European Union has fined the meta $ 1.3 billion for infringing the EU privacy laws by transferring the personal data of Facebook users to the United States. The EU fined Meta’s business in Ireland. As per the European Union, transferring Personal data to the US is a breach of the General data protection Regulation or European Union law on data protection and privacy.
GDPR Compliance
The terms of GDPR promise to gather users’ personal information legally and under strict conditions. And those who collect and manage personal data must protect users’ personal data from exploitation. The GDPR restricts an organisation’s capacity to transfer personal data outside the EU if the transfer is solely based on that body’s evaluation of the sufficiency of the personal data’s protection. Transfers should only be made where European authorities have determined that a third country, a territory within that third country, or an international organisation provides acceptable protection for data protection.
Violation by Meta
The punishment, announced by Ireland’s Data Protection Commission, might be one of the most significant in the five years since the European Union passed the landmark General Data Protection Regulation. According to regulators, Facebook failed to comply with a 2020 judgment by the European Union’s top court that Facebook data transferred over the Atlantic was not sufficiently safeguarded from American espionage agencies. However, whether Meta will ever need to encrypt Facebook users’ data in Europe is still being determined. Meta announced it would appeal the ruling, launching a potentially legal procedure.
Simultaneously, European Union and American officials are negotiating a new data-sharing pact that would provide legal protections for Meta and scores of other companies to continue moving information between the US and Europe. This pact could overturn much of the European Union’s Monday ruling.
Article 46(1) GDPR Has been violated by the meta, And as per the Irish privacy.
What is required by the GDPR before transferring personal information across national boundaries?

Personal data transfers to countries outside the European Economic Area are generally permitted if these nations are regarded to provide a sufficient degree of data protection. According to Article 45 of the GDPR, the European Commission evaluates the degree of personal data protection in third countries.
The European Union judgment demonstrates how government rules are upending the borderless way data has traditionally migrated. Companies are increasingly being pressed to store data within the country where it is acquired rather than allowing it to transfer freely to data centres around the world as a result of data-protection requirements, national security laws, and other regulations.
The US internet giant had previously warned that if forced to stop using SCCs (standard contractual clauses) without a proper alternative data transfer agreement in place, it would be compelled to shut down services such as Facebook and Instagram in Europe.
What will happen next for Facebook in Europe?
The ruling includes a six-month transition period before it must halt data flows, meaning the service will continue to operate in the meantime. (More specifically, Meta has been given a five-month transition period to freeze any future transfer of personal data to the United States and a six-month deadline to terminate the unlawful processing and/or storage of European user data it has previously transferred without a legitimate legal basis. Meta has also stated that it will appeal and appears to seek a stay of execution while it pursues its legal arguments in court.
Conclusion
The GDPR places restrictions on transferring personal data outside the European Union to third-party nations or international bodies to ensure that the GDPR’s level of protection for individuals is not jeopardised. But the meta violated the European Union’s privacy laws by the user’s personal information to the US. Under the compliance of GDPR, transferring and sending personal information to users intentionally is an offence. and presently, the personal data of Facebook users has been breached by the Meta, as they shared the information with the US.

Introduction
Recent advances in space exploration and technology have increased the need for space laws to control the actions of governments and corporate organisations. India has been attempting to create a robust legal framework to oversee its space activities because it is a prominent player in the international space business. In this article, we’ll examine India’s current space regulations and compare them to the situation elsewhere in the world.
Space Laws in India
India started space exploration with Aryabhtta, the first satellite, and Rakesh Sharma, the first Indian astronaut, and now has a prominent presence in space as many international satellites are now launched by India. NASA and ISRO work closely on various projects
India currently lacks any space-related legislation. Only a few laws and regulations, such as the Indian Space Research Organisation (ISRO) Act of 1969 and the National Remote Sensing Centre (NRSC) Guidelines of 2011, regulate space-related operations. However, more than these rules and regulations are essential to control India’s expanding space sector. India is starting to gain traction as a prospective player in the global commercial space sector. Authorisation, contracts, dispute resolution, licencing, data processing and distribution related to earth observation services, certification of space technology, insurance, legal difficulties related to launch services, and stamp duty are just a few of the topics that need to be discussed. The necessary statute and laws need to be updated to incorporate space law-related matters into domestic laws.
India’s Space Presence
Space research activities were initiated in India during the early 1960s when satellite applications were in experimental stages, even in the United States. With the live transmission of the Tokyo Olympic Games across the Pacific by the American Satellite ‘Syncom-3’ demonstrating the power of communication satellites, Dr Vikram Sarabhai, the founding father of the Indian space programme, quickly recognised the benefits of space technologies for India.
As a first step, the Department of Atomic Energy formed the INCOSPAR (Indian National Committee for Space Research) under the leadership of Dr Sarabhai and Dr Ramanathan in 1962. The Indian Space Research Organisation (ISRO) was formed on August 15, 1969. The prime objective of ISRO is to develop space technology and its application to various national needs. It is one of the six largest space agencies in the world. The Department of Space (DOS) and the Space Commission were set up in 1972, and ISRO was brought under DOS on June 1, 1972.

Since its inception, the Indian space programme has been orchestrated well. It has three distinct elements: satellites for communication and remote sensing, the space transportation system and application programmes. Two major operational systems have been established – the Indian National Satellite (INSAT) for telecommunication, television broadcasting, and meteorological services and the Indian Remote Sensing Satellite (IRS) for monitoring and managing natural resources and Disaster Management Support.
Global Scenario
The global space race has been on and ever since the moon landing in 1969, and it has now transformed into the new cold war among developed and developing nations. The interests and assets of a nation in space need to be safeguarded by the help of effective and efficient policies and internationally ratified laws. All nations with a presence in space do not believe in good for all policy, thus, preventive measures need to be incorporated into the legal system. A thorough legal framework for space activities is being developed by the United Nations Office for Outer Space Affairs (UNOOSA). The “Outer Space Treaty,” a collection of five international agreements on space law, establishes the foundation of international space law. The agreements address topics such as the peaceful use of space, preventing space from becoming militarised, and who is responsible for damage caused by space objects. Well-established space laws govern both the United States and the United Kingdom. The National Aeronautics and Space Act, which was passed in the US in 1958 and established the National Aeronautics and Space Administration (NASA) to oversee national space programmes, is in place there. The Outer Space Act of 1986 governs how UK citizens and businesses can engage in space activity.

Conclusion
India must create a thorough legal system to govern its space endeavours. In the space sector, there needs to be a legal framework to avoid ambiguity and confusion, which may have detrimental effects. The Pacific use of space for the benefit of humanity should be covered by domestic space legislation in India. The overall scenario demonstrates the requirement for a clearly defined legal framework for the international acknowledgement of a nation’s space activities. India is fifth in the world for space technology, which is an impressive accomplishment, and a strong legal system will help India maintain its place in the space business.

Pretext
On 20th October 2022, the Competition Commission of India (CCI) imposed a penalty of Rs. 1,337.76 crores on Google for abusing its dominant position in multiple markets in the Android Mobile device ecosystem, apart from issuing cease and desist orders. The CCI also directed Google to modify its conduct within a defined timeline. Smart mobile devices need an operating system (OS) to run applications (apps) and programs. Android is one such mobile operating system that Google acquired in 2005. In the instant matter, the CCI examined various practices of Google w.r.t. licensing of this Android mobile operating system and various proprietary mobile applications of Google (e.g., Play Store, Google Search, Google Chrome, YouTube, etc.).
The Issue
Google was found to be misusing its dominant position in the tech market, and the same was the reason behind the penalty. Google argued about the competitive constraints being faced from Apple. In relation to understanding the extent of competition between Google’s Android ecosystem and Apple’s iOS ecosystem, the CCI noted the differences in the two business models, which affect the underlying incentives of business decisions. Apple’s business is primarily based on a vertically integrated smart device ecosystem that focuses on the sale of high-end smart devices with state-of-the-art software components. In contrast, Google’s business was found to be driven by the ultimate intent of increasing users on its platforms so that they interact with its revenue-earning service, i.e., online searches, which directly affects the sale of online advertising services by Google. It was seen that google had created a dominant position among the android phone manufacturers as they were made to have a set of google apps preinstalled in the device to increase the user’s dependency on google services. The CCI felt that Google had created a dominant position to which they replied that the same operations are done by Apple as well, to which the commission responded that apple is a phone and app manufacturer and they have Apple-owned apps in Apple devices only, but Google here in had made a pseudo mandate for android manufactures to have the google apps pre-installed which is, in turn, a possible way of disrupting the market equilibrium and violative of market practices. The CCI imposed a penalty of Rs. 1,337.76 for abusing its dominant position in multiple markets in India, CCI delineated the following five relevant markets in the present matter –

- The market for licensable OS for smart mobile devices in India
- The market for app store for Android smart mobile OS in India
- The market for general web search services in India
- The market for non-OS specific mobile web browsers in India
- The market for online video hosting platforms (OVHP) in India.
Supreme Courts Opinion
In October 2022, the Competition Commission of India (CCI) ruled that Google, owned by Alphabet Inc, exploited its dominant position in Android and told it to remove restrictions on device makers, including those related to the pre-installation of apps and ensuring exclusivity of its search. Google lost a challenge in the Supreme Court to block the directives, as the learned court refused to put a stay on the imposed penalty, further giving seven days to comply. The Supreme Court has said a lower tribunal—where Google first challenged the Android directives—can continue to hear the company’s appeal and must rule by March 31.
Counterpoint Research estimates that about 97% of 600 million smartphones in India run on Android. Apple has just a 3% share. Hoping to block the implementation of the CCI directives, Google challenged the CCI order in the Supreme Court by warning it could stall the growth of the Android ecosystem. It also said it would be forced to alter arrangements with more than 1,100 device manufacturers and thousands of app developers if the directives kick in. Google has been concerned about India’s decision as the steps are seen as more sweeping than those imposed in the European Commission’s 2018 ruling. There it was fined for putting in place what the Commission called unlawful restrictions on Android mobile device makers. Google is still challenging the record $4.3 billion fine in that case. In Europe, Google made changes later, including letting Android device users pick their default search engine, and said device makers would be able to license the Google mobile application suite separately from the Google Search App or the Chrome browser.
Conclusion
As the world goes deeper into cyberspace, the big tech companies have more control over the industry and the markets, but the same should not turn into anarchy in the global markets. The Tech giants need to be made aware that compliance is the utmost duty for all companies, and enforcement of the law of the land will be maintained no matter what. Earlier India lacked policies and legislation to govern cyberspace, but in the recent proactive stance by the govt, a lot of new bills have been tabled, one of them being the Intermediary Rules 2021, which has laid down the obligations nand duties of the companies by setting up an intermediary in the country. Such bills coupled with such crucial judgments on tech giants will act as a test and barrier for other tech companies who try to flaunt the rules and avoid compliance.

What are Wi-Fi attacks?
Wi-fi is an important area of cyber security and there is no need for physical cable for the network. Wi-Fi has access to a network signal radius everywhere. The devices and systems can have a network without physical access due to Wi-fi. But everything comes with cons and pros, and if we talk about cybersecurity, it has been established that Wi-fi networks are extremely vulnerable to security breaches and it is very easy to be hacked by hackers. Wi-Fi can be accessed by almost every device in the modern day: it can be smartphones, tablets, computers, and laptops. To know whether someone has been tampering with your personal Wi-Fi there are certain signs that can prove it. The first and most important sign is that your internet speed gets slower, as someone else is using your Wi-Fi surf.
Why would anyone hack someone’s Wi-Fi network?
Usually, hackers hack the network because they want access to the confidential data of someone and they can observe all the online activities and data that have been sent through a network. An unauthorize hacker will pretty much be able to see everything you do online. Wi-Fi allows hackers o view information on sites. Any financial information which is saved in the browser can be accessed by hackers and they can alter it and can alter the content you see online. And all the information saved in Wi-fi networks can be used by hackers for their own benefit, they can sell it, impersonate you, or even take money out of your bank through Wi-Fi.
Avoiding vulnerable Wi-Fi networks
The first and foremost rule of protection is that you should not use public networks if that network is easily open to you then that is also available to others and from others, and someone can who wishes to use your confidential and sensitive information, can access that. If you really need to access the public network in an urgent situation, then you must make sure to limit your activities while connected. And avoid accessing your online banking or pages that require login information. Also, a good measure to take as well is to always delete your cookies after using public WIFI.
How To Secure Your Home Wi-Fi Network
Your home’s wireless internet connection is your Wi-Fi network. Typically, a wireless router is used, which broadcasts a signal into the atmosphere. You can connect to the internet using that signal. However, if your network is not password-protected, any nearby device can grab the signal off the air and connect to your internet. The benefit of Wi-Fi? Wireless access to the internet is possible. The negative? Your internet activity, including your personal information, may be visible to neighboring users who connect to your unprotected network. Furthermore, if someone uses your network to conduct a crime or send out unauthorized spam, you might be held accountable.
Wi-Fi or Li-Fi? –
The common consensus is that Li-Fi technology is more secure than Wi-Fi. Li-Fi systems can be made more secure by integrating a variety of security features. Although these qualities might appear when Li-Fi is widely used in the near future, it is already thought to be safer because of a number of security features. Since the connection’s characteristics make it simpler to lock connections, limit access, and track users even in the absence of encryption and other security features, Li-Fi is seen as being safer. Li-Fi systems will be able to support new security protocols, which will not only enable high-speed networking but also open the door for innovative security techniques to strengthen connections.
Conclusion
A hacker can sniff the network packets without having to be in the same building where the network is located. As wireless networks communicate through radio waves, a hacker can easily sniff the network from a nearby location. Most attackers use network sniffing to find the SSID and hack a wireless network.
Any wireless network can theoretically be attacked in a number of different ways. Use of the default SSID or password, WPS pin authentication, insufficient access control, and leaving the access point available in open locations are all examples of potential vulnerabilities that could allow for the theft of sensitive data. Kismet’s architecture in WIDS mode may guard against DOS, MiTM, and MAC spoofing attacks. routine software updates on the other hand, the use of firewalls may help defend the network against outside intrusion. The act of finding infrastructure issues that could allow harmful code to be injected into a service, system, or organization is known as ethical hacking. They use this technique to prevent invasions by lawfully breaking into networks and looking for weak spots.

Introduction
Google Play has announced its new policy which will ensure trust and transparency on google play by providing a new framework for developer verification and app details. The new policy requires that new developer accounts on Google Play will have to provide a D-U-N-S number to verify the business. So when an organisation will create a new Play Console developer account the organisation will need to provide a D-U-N-S number. Which is a nine-digit unique identifier which will be used to verify their business. The new google play policy aims to enhance user trust. And the developer will provide detailed developer details on the app’s listing page. Users will get to know who is behind the app which they are installing.
Verifying Developer Identity with D-U-N-S Numbers
To boost security the google play new policy requires the developer account to provide the D-U-N-S number when creating a new Play Console developer account. The D-U-N-S number assigned by Dun & Bradstreet will be used to verify the business. Once the developer creates his new Play Console developer account by providing a D-U-N-S number, Google Play will verify the developer’s details, and he will be able to start publishing the apps. Through this step, Google Play aims to validate the business information in a more authentic way.
If your organisation does not have a D-U-N-S number, you may check on or request for it for free on this website (https://www.dnb.com/duns-number/lookup.html). The request process for D-U-N-S can take up to 30 days. Developers are also required to keep the information up to date.
Building User Trust with Enhanced App Details
In addition to verifying developer identities in a more efficient way, google play also requires that developer provides sufficient app details to the users. There will be an “App Support” section on the app’s store listing page, where the developer will display the app’s support email address and even can include their website and phone number for support.
The new section “About the developer” will also be introduced to provide users with verified identity information, including the developer’s name, address, and contact details. Which will make the users more informed about the valuable information of the app developers.
Key highlights of the Google Play Polic
- Google Play came up with the policy to keep the platform safe by verifying the developers’ identity and it will also help to reduce the spread of malware apps and help the users to make confident informed decisions about the apps they download. Google Play announced the policy by expanding its developer verification requirement to strengthen Google Play as a platform and build user trust. When you create a new Play Console Developer account and choose organisation as your account type you will now need to provide a D-U-N-S number.
- Users will get detailed information about the developers’ identities and contact information, building more transparency and encouraging responsible app development practices.
- This policy will enable the users to make informed choices about the apps they download.
- The new “App support” section will provide enhanced communication between users and developers by displaying support email addresses, website and support phone numbers, streamlining the support process and user satisfaction.
Timeline and Implementation
The new policy requirements for D-U-N-S numbers will start rolling out on 31 August 2023 for all new Play Console developer accounts. The “About the developer” section will be visible to users as soon as a new app is published. and In October 2023, existing developers will also be required to update and verify their existing accounts to comply with the new verification policy.
Conclusion
Google Play’s new policy will aim to enhance the more transparent app ecosystem. This new policy will provide the users with more information about the developers. Google Play aims to establish a platform where users can confidently discover and download apps. This new policy will enhance the user experience on google play in terms of a reliable and trustworthy platform.

Introduction
Recently, a Consultation Paper on Regulatory Mechanisms for Over-The-Top (OTT) Communication Services was published by the Telecom Regulatory Authority of India (TRAI). The paper explores several OTT regulation-related challenges and solicits input from stakeholders on a suggested regulatory framework. We’ll summarise the paper’s main conclusions in this blog.
Structure of the Paper
The Telecom Regulatory Authority of India’s Consultation Paper on Regulatory Mechanism for Over-The-Top (OTT) Communication Services and Selective Banning of OTT Services intends to solicit comments and recommendations from stakeholders about the regulation of OTT services in India. The paper is broken up into five chapters that cover the introduction and background, issues with regulatory mechanisms for OTT communication services, issues with the selective banning of OTT services, a summary of the issues for consultation, and an overview of international practices on the topic. Written comments from interested parties are requested and may be sent electronically to the Advisor (Networks, Spectrum and Licencing) at TRAI. These comments will also be posted on the TRAI website.
Overview of the Paper
- Chapter 1: Introduction and Background
- The first chapter of the essay introduces the subject of OTT communication services and argues why regulatory frameworks are necessary. The chapter also gives a general outline of the topics and the paper’s organisation that will be covered in the following chapters.
- Chapter 2: Examination of the Issues Related to Regulatory Mechanism for Over-The-Top Communication Services
- The second chapter of the essay looks at the problems with OTT communication service regulation. It talks about the many kinds of OTT services and how they affect the conventional telecom sector. The chapter also looks at the regulatory issues raised by OTT services and the various strategies used by various nations to address them.
- Chapter 3: Examination of the Issues Related to Selective Banning of OTT Services
- The final chapter of the essay looks at the problems of selectively outlawing OTT services. It analyses the justifications for government restrictions on OTT services as well as the possible effects of such restrictions on consumers and the telecom sector. The chapter also looks at the legal and regulatory structures that determine how OTT services are prohibited in various nations.
- Chapter 4: International Practices
- An overview of global OTT communication service best practices is given in the paper’s fourth chapter. It talks about the various regulatory strategies used by nations throughout the world and how they affect consumers and the telecom sector. The chapter also looks at the difficulties regulators encounter when trying to create efficient regulatory frameworks for OTT services.
- Chapter 5: Issues for Consultation
- This chapter is the spirit of the consultation paper as it covers the points and questions for consultation. This chapter has been classified into two sub-sections – Issues Related to Regulatory Mechanisms for OTT Communication Services and Issues Related to the Selective Banning of OTT Services. The inputs will be entirely focused on these sub headers, and the scope, extent, and ambit of the consultation paper rests on these questions and necessary inputs.
Conclusion
An important publication that aims to address the regulatory issues raised by OTT services is the Consultation Paper on Regulatory Mechanisms for Over-The-Top Communication Services. The paper offers a thorough analysis of the problems with OTT service regulation and requests input from stakeholders on the suggested regulatory structure. In order to make sure that the regulatory framework is efficient and advantageous for everyone, it is crucial for all stakeholders to offer their opinion on the document.

Introduction
Twitter Inc.’s appeal against barring orders for specific accounts issued by the Ministry of Electronics and Information Technology was denied by a single judge on the Karnataka High Court. Twitter Inc. was also given an Rs. 50 lakh fine by Justice Krishna Dixit, who claimed the social media corporation had approached the court defying government directives.
As a foreign corporation, Twitter’s locus standi had been called into doubt by the government, which said they were ineligible to apply Articles 19 and 21 to their situation. Additionally, the government claimed that because Twitter was only designed to serve as an intermediary, there was no “jural relationship” between Twitter and its users.
The Issue
In accordance with Section 69A of the Information Technology Act, the Ministry issued the directives. Nevertheless, Twitter had argued in its appeal that the orders “fall foul of Section 69A both substantially and procedurally.” Twitter argued that in accordance with 69A, account holders were to be notified before having their tweets and accounts deleted. However, the Ministry failed to provide these account holders with any notices.
On June 4, 2022, and again on June 6, 2022, the government sent letters to Twitter’s compliance officer requesting that they come before them and provide an explanation for why the Blocking Orders were not followed and why no action should be taken against them.
Twitter replied on June 9 that the content against which it had not followed the blocking orders does not seem to be a violation of Section 69A. On June 27, 2022, the Government issued another notice stating Twitter was violating its directions. On June 29, Twitter replied, asking the Government to reconsider the direction on the basis of the doctrine of proportionality. On June 30, 2022, the Government withdrew blocking orders on ten account-level URLs but gave an additional list of 27 URLs to be blocked. On July 10, more accounts were blocked. Compiling the orders “under protest,” Twitter approached the HC with the petition challenging the orders.
Legality
Additionally, the government claimed that because Twitter was only designed to serve as an intermediary, there was no “jural relationship” between Twitter and its users.
Government attorney Additional Solicitor General R Sankaranarayanan argued that tweets mentioning “Indian Occupied Kashmir” and the survival of LTTE commander Velupillai Prabhakaran were serious enough to undermine the integrity of the nation.
Twitter, on the other hand, claimed that its users have pushed for these rights. Additionally, Twitter maintained that under Article 14 of the Constitution, even as a foreign company, they were entitled to certain rights, such as the right to equality. They also argued that the reason for the account blocking in each case was not stated and that Section 69a’s provision for blocking a URL should only apply to the offending URL rather than the entire account because blocking the entire account would prevent the creation of information while blocking the offending tweet only applied to already-created information.
Conclusion
The evolution of cyberspace has been substantiated by big tech companies like Facebook, Google, Twitter, Amazon and many more. These companies have been instrumental in leading the spectrum of emerging technologies and creating a blanket of ease and accessibility for users. Compliance with laws and policies is of utmost priority for the government, and the new bills and policies are empowering the Indian cyberspace. Non Compliance will be taken very seriously, and the same is legalised under the Intermediary Guidelines 2021 and 2022 by Meity. Referring to Section 79 of the Information Technology Act, which pertains to an exemption from liability of intermediary in some instances, it was said, “Intermediary is bound to obey the orders which the designate authority/agency which the government fixes from time to time.”

Introduction
Cert-In (Indian Computer Emergency Response Team) has recently issued the “Guidelines on Information Security Practices” for Government Entities for Safe & Trusted Internet. The guideline has come at a critical time when the Draft Digital India Bill is about to be released, which is aimed at revamping the legal aspects of Indian cyberspace. These guidelines lay down the policy framework and the requirements for critical infrastructure for all government organisations and institutions to improve the overall cyber security of the nation.
What is Cert-In?
A Computer Emergency Response Team (CERT) is a group of information security experts responsible for the protection against, detection of and response to an organisation’s cybersecurity incidents. A CERT may focus on resolving data breaches and denial-of-service attacks and providing alerts and incident handling guidelines. CERTs also conduct ongoing public awareness campaigns and engage in research aimed at improving security systems. The Ministry of Electronics and Information Technology (MeitY) oversees CERT-In. It regularly releases alerts to help individuals and companies safeguard their data, information, and ICT (Information and Communications Technology) infrastructure.
Indian Computer Emergency Response Team (CERT-In) has been established and appointed as national agency in respect of cyber incidents and cyber security incidents in terms of the provisions of section 70B of Information Technology (IT) Act, 2000.
CERT-In requests information from service providers, intermediaries, data centres, and body corporates to coordinate reaction actions and emergency procedures regarding cyber security incidents. It is a focal point for incident reporting and offers round-the-clock security services. It manages cyber occurrences that are tracked and reported while continuously analysing cyber risks. It strengthens the security barriers for the Indian Internet domain.
Background
India is fast becoming one of the world’s largest connected nations – with over 80 Crore Indians (Digital Nagriks) presently connected and using the Internet and cyberspace – and with this number is expected to touch 120 Crores in the coming few years. The Digital Nagriks of the country are using the Internet for business, education, finance and various applications and services including Digital Government services. Internet provides growth and innovation and at the same time it has seen rise in cybercrimes, user harm and other challenges to online safety. The policies of the Government are aimed at ensuring an Open, Safe & Trusted and Accountable Internet for its users. Government is fully cognizant and aware of the growing cyber security threats and attacks.
It is the Government of India’s objective to ensure that Digital Nagriks experience a Safe & Trusted Internet. Along with ubiquitous applications of Information & Communication Technologies (ICT) in almost all facets of service delivery and operations, continuously evolving cyber threats have become a concern for the Government. Cyber-attacks can come in the form of malware, ransomware, phishing, data breach etc., that adversely affect an organisation’s information and systems. Cyber threats leading to cyber-attacks or incidents can compromise the confidentiality, integrity, and availability of an organisation’s information and systems and can have far reaching impact on essential services and national interests. To protect against cyber threats, it is important for government entities to implement strong cybersecurity measures and follow best practices. As ICT infrastructure of the Government entities is one of the preferred targets of the malicious actors, responsibility of implementing good cyber security practices for protecting computers, servers, applications, electronic systems, networks, and data from digital attacks, also remain with the ICT assets’ owner i.e. Government entity.
What are the new Guidelines about?
The Government of India (distribution of business) Rules, 1961’s First Schedule lists a number of Ministries, Departments, Secretariats, and Offices, along with their affiliated and subordinate offices, which are all subject to the rules. They also comprise all governmental organisations, businesses operating in the public sector, and other governmental entities under their administrative control.
“The government has launched a number of steps to guarantee an accessible, trustworthy, and accountable digital environment. With a focus on capabilities, systems, human resources, and awareness, we are extending and speeding our work in the area of cyber security, according to Rajeev Chandrasekhar, Minister of State for Electronics, Information Technology, Skill Development, and Entrepreneurship.
The Recommendations
- Various security domains are covered in the standards, including network security, identity and access management, application security, data security, third-party outsourcing, hardening procedures, security monitoring, incident management, and security audits.
- For instance, the rules advise using only a Standard User (non-administrator) account to use computers and laptops for regular work regarding desktop, laptop, and printer security in the workplace. Users may only be granted administrative access with the CISO’s consent.
- The usage of lengthy passwords containing at least eight characters that combine capital letters, tiny letters, numerals, and special characters; Never save any usernames or passwords in your web browser. Likewise, never save any payment-related data there.
- They include guidelines created by the National Informatics Centre for Chief Information Security Officers (CISOs) and staff members of Central government Ministries/Departments to improve cyber security and cyber hygiene in addition to adhering to industry best practises.
Conclusion
The government has been proactive in the contemporary times to eradicate the menace of cybercrimes and therreats from the Indian cyberspace and hence now we have seen a series of new bills and polices introduced by the Ministry of Electronics and Information Technology, and various other government organisations like Cert-In and TRAI. These policies have been aimed towards being relevant to time and current technologies. The threats from emerging technologies like web 3.0 cannot be ignored and hence with active netizen participation and synergy between government and corporates will lead to a better and improved cyber ecosystem in India.

Introduction
The Telecom Regulatory Authority of India (TRAI) issued a consultation paper titled “Encouraging Innovative Technologies, Services, Use Cases, and Business Models through Regulatory Sandbox in Digital Communication Sector. The paper presents a draft sandbox structure for live testing of new digital communication products or services in a regulated environment. TRAI seeks comments from stakeholders on several parts of the framework.
What is digital communication?
Digital communication is the use of internet tools such as email, social media messaging, and texting to communicate with other people or a specific audience. Even something as easy as viewing the content on this webpage qualifies as digital communication.
Aim of Paper
- Frameworks are intended to support regulators’ desire for innovation while also ensuring economic resilience and consumer protection. Considering this, the Department of Telecom (DoT) asked TRAI to offer recommendations on a regulatory sandbox framework. TRAI approaches the issue with the goal of encouraging creativity and hastening the adoption of cutting-edge digital communications technologies.
- Artificial intelligence, the Internet of Things, edge computing, and other emerging technologies are revolutionizing how we connect, communicate, and access information, driving the digital communication sector to rapidly expand. To keep up with this dynamic environment, an enabling environment for the development and deployment of novel technologies, services, use cases, and business models is required.
- The regulatory sandbox concept is becoming increasingly popular around the world as a means of encouraging innovation in a range of industries. A regulatory sandbox is a regulated environment in which businesses and innovators can test their concepts, commodities, and services while operating under changing restrictions.
- Regulatory Sandbox will benefit the telecom startup ecosystem by providing access to a real-time network environment and other data, allowing them to evaluate the reliability of new applications before releasing them to the market. Regulatory Sandbox also attempts to stimulate cross-sectoral collaboration for carrying out such testing by engaging the assistance of other ministries and departments in order to give the starting company with a single window for acquiring all clearances.
What is regulatory sandbox?
- A regulatory sandbox is a controlled regulatory environment in which new products or services are tested in real-time.
- It serves as a “safe space” for businesses because authorities may or may not allow certain relaxations for the sole purpose of testing.
- The sandbox enables the regulator, innovators, financial service providers, and clients to perform field testing in order to gather evidence on the benefits and hazards of new financial innovations, while closely monitoring and mitigating their risks.
What are the advantages of having a regulatory sandbox?
- Firstly, regulators obtain first-hand empirical evidence on the benefits and risks of emerging technologies and their implications, allowing them to form an informed opinion on the regulatory changes or new regulations that may be required to support useful innovation while mitigating the associated risks.
- Second, sandbox customers can evaluate the viability of a product without the need for a wider and more expensive roll-out. If the product appears to have a high chance of success, it may be authorized and delivered to a wider market more quickly.
Digital communication sector and Regulatory Sandbox
- Many countries’ regulatory organizations have built sandbox settings for telecom tech innovation.
- These frameworks are intended to encourage regulators’ desire for innovation while also promoting economic resilience and consumer protection.
- In this context, the Department of Telecom (DoT) had asked TRAI to give recommendations on a regulatory sandbox framework.
- Written comments on the drafting framework will be received until July 17, 2023, and counter-comments will be taken until August 1, 2023. The Authority’s goal in the digital communication industry is to foster creativity and expedite the use of emerging technologies such as artificial intelligence (AI), the Internet of Things (IoT), and edge computing. These technologies are changing the way individuals connect, engage, and access information, causing rapid changes in the industry.
Conclusion
According to TRAI, these technologies are changing how individuals connect, engage, and obtain information, resulting in significant changes in the sector.
The regulatory sandbox also wants to stimulate cross-sectoral collaboration for carrying out such testing by engaging the assistance of other ministries and departments in order to give the starting company with a single window for acquiring all clearances. The consultation paper covers some of the worldwide regulatory sandbox frameworks in use in the digital communication industry, as well as some of the frameworks in use inside the country in other sectors.

Introduction
The Telecom Regulatory Authority of India (TRAI) has directed all telcos to set up detection systems based on Artificial Intelligence and Machine Learning (AI/ML) technologies in order to identify and control spam calls and text messages from unregistered telemarketers (UTMs).
The TRAI Directed telcos
The telecom regulator, TRAI, has directed all Access Providers to detect Unsolicited commercial communication (UCC)by systems, which is based on Artificial Intelligence and Machine Learning to detect, identify, and act against senders of Commercial Communication who are not registered in accordance with the provisions of the Telecom Commercial Communication Customer Preference Regulations, 2018 (TCCCPR-2018). Unregistered Telemarketers (UTMs) are entities that do not register with Access Providers and use 10-digit mobile numbers to send commercial communications via SMS or calls.
TRAI steps to curb Unsolicited commercial communication
TRAI has taken several initiatives to reduce Unsolicited Commercial Communication (UCC), which is a major source of annoyance for the public. It has resulted in fewer complaints filed against Registered Telemarketers (RTMs). Despite the TSPs’ efforts, UCC from Unregistered Telemarketers (UTMs) continues. Sometimes, these UTMs use messages with bogus URLs and phone numbers to trick clients into revealing crucial information, leading to financial loss.
To detect, identify, and prosecute all Unregistered Telemarketers (UTMs), the TRAI has mandated that Access Service Providers implement the UCC.
Detect the System with the necessary functionalities within the TRAI’s Telecom Commercial Communication Customer Preference Regulations, 2018 framework.
Access service providers have implemented such detection systems based on their applicability and practicality. However, because UTMs are constantly creating new strategies for sending unwanted communications, the present UCC detection systems provided by Access Service providers cannot detect such UCC.
TRAI also Directs Telecom Providers to Set Up Digital Platform for Customer Consent to Curb Promotional Calls and Messages.
Unregistered Telemarketers (UTMs) sometimes use messages with fake URLs and phone numbers to trick customers into revealing essential information, resulting in financial loss.

TRAI has urged businesses like banks, insurance companies, financial institutions, and others to re-verify their SMS content templates with telcos within two weeks. It also directed telecom companies to stop misusing commercial messaging templates within the next 45 days.
The telecom regulator has also instructed operators to limit the number of variables in a content template to three. However, if any business intends to utilise more than three variables in a content template for communicating with their users, this should be permitted only after examining the example message, as well as adequate justifications and justification.
In order to ensure consistency in UCC Detect System implementations, TRAI has directed all Access Providers to deploy UCC and detect systems based on artificial intelligence and Machine Learning that are capable of constantly evolving to deal with new signatures, patterns, and techniques used by UTMs.
Access Providers have also been directed to use the DLT platform to share intelligence with others. Access Providers have also been asked to ensure that such UCC Detect System detects senders that send unsolicited commercial communications in bulk and do not comply with the requirements. All Access Providers are directed to follow the instructions and provide an update on actions done within thirty days.
The move by TRAI is to curb the menacing calls as due to this, the number of scam cases is increasing, and now a new trend of scams started as recently, a Twitter user reported receiving an automated call from +91 96681 9555 with the message “This call is from Delhi Police.” It then asked her to stay in the queue since some of her documents needed to be picked up. Then he said he works as a sub-inspector at the Kirti Nagar police station in New Delhi. He then inquired whether she had recently misplaced her Aadhaar card, PAN card, or ATM card, to which she replied ‘no’. The scammer then poses as a cop and requests that she authenticate the last four digits of her card because they have found a card with her name on it. And a lot of other people tweeted about it.

Conclusion
TRAI directed the telcos to check the calls and messages from Unregistered numbers. This step of TRAI will curb the pesky calls and messages and catch the Frauds who are not registered with the regulation. Sometimes the unregistered sender sends fraudulent links, and through these fraudulent calls and messages, the sender tries to take the personal information of the customers, which results in financial losses.

Introduction
To combat the problem of annoying calls and SMS, telecom regulator TRAI has urged service providers to create a uniform digital platform in two months that will allow them to request, maintain, and withdraw customers’ approval for promotional calls and messages. In the initial stage, only subscribers will be able to initiate the process of registering their consent to receive promotional calls and SMS, and later, business entities will be able to contact customers to seek their consent to receive promotional messages, according to a statement issued by the Telecom Regulatory Authority of India (TRAI) on Saturday.
TRAI Directs Telecom Providers to Set Up Digital Platform
TRAI has now directed all access providers to develop and deploy the Digital Consent Acquisition (DCA) facility for creating a unified platform and process to digitally register customers’ consent across all service providers and principal entities. Consent is received and maintained under the current system by several key entities such as banks, other financial institutions, insurance firms, trading companies, business entities, real estate businesses, and so on.
The purpose, scope of consent, and the principal entity or brand name shall be clearly mentioned in the consent-seeking message sent over the short code,” according to the statement.
It stated that only approved online or app links, call-back numbers, and so on will be permitted to be used in consent-seeking communications.
TRAI issued guidelines to guarantee that all voice-based Telemarketers are brought under a single Distributed ledger technology (DLT) platform for more efficient monitoring of nuisance calls and unwanted communications. It also instructs operators to actively deploy AI/ML-based anti-phishing systems as well as to integrate tech solutions on the DLT platform to deal with malicious calls and texts.
TRAI has issued two separate Directions to Access Service Providers under TCCCPR-2018 (Telecom Commercial Communications Customer Preference Regulations) to ensure that all promotional messages are sent through Registered Telemarketers (RTMs) using approved Headers and Message Templates on Distributed Ledger Technologies (DLT) platform, and to stop misuse of Headers and Message Templates,” the regulator said in a statement.
Users can already block telemarketing calls and texts by texting 1909 from their registered mobile number. By dialing 1909, customers can opt out of getting advertising calls by activating the do not disturb (DND) feature.

Telecom providers operate DLT platforms, and businesses involved in sending bulk promotional or transactional SMS must register by providing their company information, including sender IDs and SMS templates.
According to the instructions, telecom companies will send consent-seeking messages using the common short code 127. The goal, extent of consent, and primary entity/brand name must be clearly stated in the consent-seeking message delivered via the shortcode.
TRAI stated that only whitelisted URLs/APKs (Android package kits file format)/OTT links/call back numbers, etc., shall be used in consent-seeking messages.
Telcos must “ensure that promotional messages are not transmitted by unregistered telemarketers or telemarketers using telephone numbers (10 digits numbers).” Telecom providers have been urged to act against all erring telemarketers in accordance with the applicable regulations and legal requirements.
Users can, however, refuse to receive any consent-seeking messages launched by any significant Telcos have been urged to create an SMS/IVR (interactive voice response)/online service for this purpose.
According to TRAI’s timeline, the consent-taking process by primary companies will begin on September 1.According to a nationwide survey conducted by a local circle, 66% of mobile users continue to receive three or more bothersome calls per day, the majority of which originate from personal cell numbers.
There are scams surfacing on the internet with new types of scams, like WhatsApp international call scams. The latest scam is targeting Delhi police, the scammers pretend to be police officials of Delhi and ask for the personal details of the users and the calling them from a 9-digit number.
A recent scam
A Twitter user reported receiving an automated call from +91 96681 9555, stating, “This call is from Delhi Police.” It went on to ask her to stay in the queue since some of her documents needed to be picked up. Then he said he is a sub-inspector at New Delhi’s Kirti Nagar police station. He then questioned if she had lately misplaced her Aadhaar card, PAN card, or ATM card, to which she replied ‘no’. The fraudster then claims to be a cop and asks her to validate the final four digits of her card because they have discovered a card with her name on it. And so many other people tweeted about this.
The scams are constantly increasing as earlier these scammers asked for account details and claimed to be Delhi police and used 9-digit numbers for scamming people.
TRAI’s new guidelines regarding the consent to receive any promotional calls and messages to telecommunication providers will be able to curb the scams.
The e- KYC is an essential requirement as e-KYC offers a more secure identity verification process in an increasingly digital age that uses biometric technologies to provide quick results.

Conclusion
The aim is to prevent unwanted calls and communications sent to customers via digital methods without their permission. Once this platform is implemented, an organization can only send promotional calls or messages with the customer’s explicit approval. Companies use a variety of methods to notify clients about their products, including phone calls, text messages, emails, and social media. Customers, however, are constantly assaulted with the same calls and messages as a result of this practice. With the constant increase in scams, the new guideline of TRAI will also curb the calling of Scams. digital KYC prevents SIM fraud and offers a more secure identity verification method.

Introduction
Online Gaming has gained popularity over the past few years, attracting young players worldwide and global concerns. In response to the growing fame of this industry, the Indian government has recently announced introducing a set of regulations to address various concerns and ensure a safer and more regulated online gaming environment. In this blog post, we will explore the critical aspects of these regulations and their impact on the gaming industry.
Why are Regulations needed?
Recently some games faced a ban in India – games that involve betting, games that can be harmful to the user, and games that involve a factor of addiction. Furthermore, with rising popularity, With the exponential rise of online gaming platforms in India, extensive laws to safeguard players and ensure fair gameplay needs to be implemented. Players’ protection is one of the critical factors addressing the issues which involve online addiction, underage involvement, fraud, and data privacy has become critical for the well-being of Indian gamers.
Regulatory Ambiguity: The previous legislative structure, such as the outmoded Public Gambling Act of 1867, required an update to fit the digital gambling age fully.
Outline of the New Regulations
Implementing new regulations for online gaming in India represents the government’s commitment to addressing different issues and ensuring a safer and more regulated gaming sector. Let’s have a look at these rules in detail:
National-Level Standards: The Indian government is currently working on creating national-level standards to standardise online gaming practices across all states. These rules attempt to create a uniform platform for both operators and participants. The government has also made an announcement to set SRO within 90 days to regulate online gaming.
Licencing and Compliance: To legally operate in the Indian market, online gaming firms must secure licences. The operator’s financial soundness, security measures, and adherence to responsible gaming practices will be scrutinised throughout the licencing process. Operators will need to comply with the regulations in order to maintain operations.
Measures to Promote Ethical Gaming: The new regulations emphasise player protection and ethical gaming practices. This includes steps like age verification to prevent underage involvement, self-exclusion choices for gamers who want to limit their gaming activities, and adopting tools like session limits and reality checks to promote responsible gaming.
Data Privacy: Recognising the importance of data privacy, the laws are intended to contain protections for protecting user data. To safeguard sensitive player information from unauthorised access or exploitation, online gambling operators must comply with data protection regulations and deploy strong security measures.
Restrictions on Advertising and Marketing: The legislation may limit the advertising and marketing of online gaming platforms. The emphasis will be on eliminating aggressive marketing tactics that target vulnerable people, such as kids. Stricter standards for ad content and placement may be implemented.
Anti-Fraud and Anti-Money Laundering Measures: To combat criminal activity within the gaming ecosystem, the new legislation will almost certainly force online gambling companies to employ anti-fraud and anti-money laundering measures. Operators may need to set up mechanisms to detect fraud, report suspicious activity, and work with law enforcement.
Consumer Grievance Redressal: The legislation may emphasise the construction of efficient channels for resolving consumer complaints. Players should be able to report difficulties, seek resolution, and offer feedback on their play experiences through channels. The objective is to create a transparent and accountable conflict resolution mechanism.

Impact on Online Gaming Ecosystem
Adopting new laws for online gambling in India will likely have several consequences for the gaming industry. Let us look at some of these consequences:
Increased Player Trust: Implementing restrictions will increase player confidence in online gaming platforms. Establishing clear rules and procedures and steps to safeguard participants’ interests will develop a sense of trust and transparency. This can lead to increased participation and engagement in the gaming community.
Industry Consolidation: Stricter restrictions may result in industry consolidation. Compliance with the new legislation would need resources and investments, which might favour more prominent and more established gambling firms. Smaller and more non-compliant operators may find it challenging to fulfil regulatory standards, resulting in a more consolidated gaming sector.
Technological Progress: The requirement to comply with rules could lead to technological advancements in the online gambling sector. Operators may invest in modern identity verification systems, fraud detection methods, and responsible gaming solutions to satisfy their regulatory requirements. This can result in technological breakthroughs that improve gamers’ overall gaming experience.
Foreign Investment and Collaboration: Clear laws might entice overseas investors to enter the Indian gaming business. The regulated environment may appeal to international gambling enterprises looking to enter or extend their presence in India. Collaborations between Indian and foreign gaming firms may also expand, resulting in the sharing of experience, resources, and the production of high-quality gaming products.
Legal Clarity: Implementing particular laws would give online gambling operators and users clearer legal standards. This transparency can eliminate ambiguity and possible legal issues, allowing stakeholders to navigate the gaming ecosystem with better confidence and knowledge.
Contribution to the Indian Economy: A well-regulated online gaming business has the potential to contribute to the Indian economy. It has the potential to create jobs, attract investment, and produce tax money for the government. The economic effect of the gaming ecosystem is expected to increase as it grows under the new restrictions.
Challenges and Future Approach
One of the toughest challenges will be the efficient implementation and enforcement of the new regulations. Consistency in applying the legislation across multiple jurisdictions and guaranteeing compliance by all operators would necessitate comprehensive monitoring and regulatory measures. Developing suitable enforcement organisations and transparent standards for reporting and dealing with noncompliance will be critical. Besides this, online gaming is open to more than area-specific and many gaming platforms and operates internationally. Ensuring cross-border operations is a big challenge in addressing jurisdictional challenges will be complex. Collaborative efforts between nations can regulate cross-border online gaming. There may be increased collaboration between Indian and foreign gaming firms, resulting in the exchange of information, skills, and resources. This partnership can help the Indian gaming sector flourish while attracting foreign players and investments.
Esports Development: Esports have grown in popularity worldwide, and India is no exception. The Indian esports business has the potential to thrive with proper regulation and support, drawing both players and viewers. Esports-specific factors like player contracts, tournament integrity, and licencing requirements may be addressed in the regulations.

Conclusion
Despite obstacles, India’s new online gambling legislation can potentially establish a safer and more regulated gaming sector. the future depends on successful implementation, adjusting to a shifting landscape, finding the correct balance between regulation and innovation, and promoting ethical gaming practices. The Indian online gaming business can develop sustainably with the appropriate strategy, benefiting gamers and the broader economy.

Introduction
Ministry of Electronics and Information Technology (MeitY) Announces to Centre Government to Plan to Certify Permissible Online Games.
In a recent update to the notification released by the Ministry of Electronics and Information Technology (MeitY) on April 6, MeitY has requested gaming entities to establish self-regulatory organisations (SROs) within a timeframe of 30 days or a maximum of 90 days from the date of the notification, which is April 6, 2023. The Ministry of Electronics and Information Technology (MeitY) has further announced that the central government will certify which online games are permissible until the SROs are officially established. The intention behind establishing SROs is to assist intermediaries, such as Apple or Google, in determining what constitutes a permitted online game, but the SRO will take 2-3 months to complete. In the meanwhile, the Central government will step in and determine what is a permissible online game.
Information Technology (Intermediary Guidelines and Digital Media Ethics Code) Rules, 2021 & Intermediary Guidelines and Digital Media Ethics Code Amendment Rules, 2023
By enacting these rules, the Indian government has taken decisive action to protect Indian gamers and their financial resources against scams and fraud. The rules also serve to promote responsible gaming while preventing young and vulnerable users from being exposed to indecent or abusive content.
Amendment Rules developed the concept of a “Permissible online real money game.” This designation is reserved for games that have passed a review process conducted by a self-regulatory body (SRB). Amendment rules indicate that Online Gaming Intermediaries must ensure that they do not permit any third party to host non-permissible online real money games on their platforms. This development is important because it empowers us to distinguish between legitimate and illicit real money games.
The Amendment Rules define an online gaming provider as an “intermediary” under the Information Technology Act of 2000, creating a separate classification called ‘Online Gaming Intermediary’.

Central government to certify what is an ‘Online Permissible Game’
The industry has been wondering what games come under wagering and will be banned. So, until the SROs are officially established, the government, in the interim, will certify what is a permissible game, what is wagering, and what is not wagering. Games that involve elements of wagering are going to be barred. The new regulations prohibit wagering on any outcome, whether in skill-based or chance-based games. Hence gaming applications involving wagering and betting apps will be barred.
Self-Regulatory Organizations (SROs)
According to the new regulations by the Ministry of Electronics and Information Technology (MeitY), online gaming intermediaries must establish a Self-Regulatory Body (SRO) to approve games offered to users over the Internet. The SRO must be registered with the Ministry and develop a framework to ensure compliance with the IT Rules 2021 objectives. An ‘online game’ can be registered by the SRO if it meets specific criteria, which include that the game is offered by an online gaming intermediary that is a member of the self-regulatory body, the game is not containing any content harmful to India’s interests, and complying with all relevant Indian regulations. If these requirements are met, the intermediary can display a visible registration mark indicating its registration with the self-regulatory authority.
Conclusion
MeitY found that with the rapid growth of the gaming industry, the real money gaming (RMG) sector had to be regulated properly. Rules framed must be properly implemented to stop gambling, betting, and wagering apps.
The IT Rules 2021, along with the Amendment Rules 2023, are created to take concrete action to curb the proliferation of gambling, betting, and wagering apps in India. These rules empower to issue of directives to ban specific apps that facilitate or promote such activities. The app ban directive allows the government to take decisive action by blocking access to these apps, making them unavailable for download or use within the country. This measure is aimed at curbing the negative impact of gambling, betting, and wagering on individuals and society, including issues related to addiction, financial loss, and illegal activities. Rules aim to actively combat the spread and influence of such apps and provide a safer online environment for gaming users.
The self-regulatory body in the context of online gaming will have the authority to grant membership to gaming intermediaries, register online games, develop a framework for regulation, interact with the Central Government, address user complaints, report instances of non-compliance, and take necessary actions to safeguard online gaming users.

Introduction
India has been a nation where technology penetration has been a little slower in the previous decades; however, that has changed now. Cyberspace has influenced and touched every country and has significantly diminished the gap between developing nations, developed nations, and underdeveloped nations. This has also been substantiated and strengthened during the Covid-19 pandemic as the world went into lockdown and the cyberspace was the only medium of communication and information. India witnessed a rise of 61% in terms of internet users, and a significant part of this number represented rural India.
New Standards
These standards have been released in threefold aspects covering – Digital Television Receivers, USB Type-C chargers, and Video Surveillance Systems, thus streamlining the use of gadgets and reduction of e-waste for the country.
1. Digital Television Receivers
The Indian standard IS 18112:2022 specification for digital television, and this standard would enable reception of free-to-air TV and radio channels just by connecting a dish antenna with LNB mounted on a suitable area with good signal reception. This will help in the transmission of knowledge about government initiatives and schemes, the educational content of Doordarshan, and the repository of Indian cultural programs. Doordarshan is in the process of phasing out analog transmission, and free-to-air channels will continue to be broadcast using digital satellite transmission. The keen aspects of educational and awareness programs run by the Govt and CSOs will impact more Indians than before as the Ministry of Information and Broadcast intends to increase their free channels of Doordarshan from 55 to 200 by the end of this year, which shows the importance of developments in the mass media industry.
2. USB Type C
Standard (IS/IEC 62680-1-3:2022) for USB Type-C receptacles, plugs, and cables adopting the existing global standard IEC 62680-1-3:2022. This standard provides for the requirements for USB type C ports and cables for use in various electronic devices like laptops, mobile phones, and other gadgets. This standard is similar to the new European standard, which is also aimed at the reduction of carbon emissions and e-waste; this move will result in ease for the industry and the end users. This will also contribute towards the strengthening of the cyber security aspects and prevent threats like ‘Juice Jacking’ to a massive extent.
3. Video Surveillance System
IS 16190, this standard provides a detailed outline of the aspects of a video surveillance system, such as requirements for its components like camera devices, interfaces, system requirements, and tests to ascertain the camera’s image quality on different devices. This series of standards would assist customers, installers, and users in establishing their requirements and determining the appropriate equipment required for their intended application and also provide means of evaluating the performance of the VSS objectively. This will also help in the improvement of surveillance by the individuals, and this will also help in the better investigation by Law enforcement agencies and faster apprehension of criminals, thus contributing to an overall safe society.

The Advantages
These standards are in power with the Internationally prevalent standards, thus taking the safety factors to the global aspect. This will also allow the Indian industry to create world-class products which can be shared all across the globe. This will open India to various opportunities and job avenues, thus opening the world to invest in India. The aspect of Atma Nirbhar Bharat and Digital India will be strengthened to a new level as the nation will be able to deliver products in power with quality in developed countries. The end Indian consumer will benefit the most from these upgraded standards in terms of Digital Televisions, Type ‘C’ USB chargers, and Video surveillance systems, as these impacts the consumers’ daily activities in terms of security and access to information.
- Reduction in Carbon Emission
- Production of World Class components and devices
- Boost to the economy and Atmanirbhar Bharat
- New avenues and opportunities for startups and MSMEs
- Better transmission of Knowledge
- Boosting FDI
- Improved quality of products for the end consumer
- New innovation hubs and exposure to global talents
This government move simply shows how India is working toward securing the Sustainable development Goals (SDG) by United Nations. This clearly shares the message to the world that India is ready for the future and will also be a helping hand to various developing and underdeveloped nations in the times to come.
Conclusion
These standards will significantly contribute towards the reduction of E-Waste and unnecessary accessories for daily use gadgets. This strengthens the reduction in carbon emissions and thus contributes towards the perseverance of the environment and working towards sustainable development goals. Such standards will lead the future towards securing the netizens and their new and evolving digital habits. In the current phase of cyberspace, the most essential aspect of establishing Critical Infrastructure as the same will act as a shield against the threats of cyberspace.


