#FactCheck - Viral Video Distorts Rahul Gandhi’s Speech to Push False Religious Claim
Executive Summary
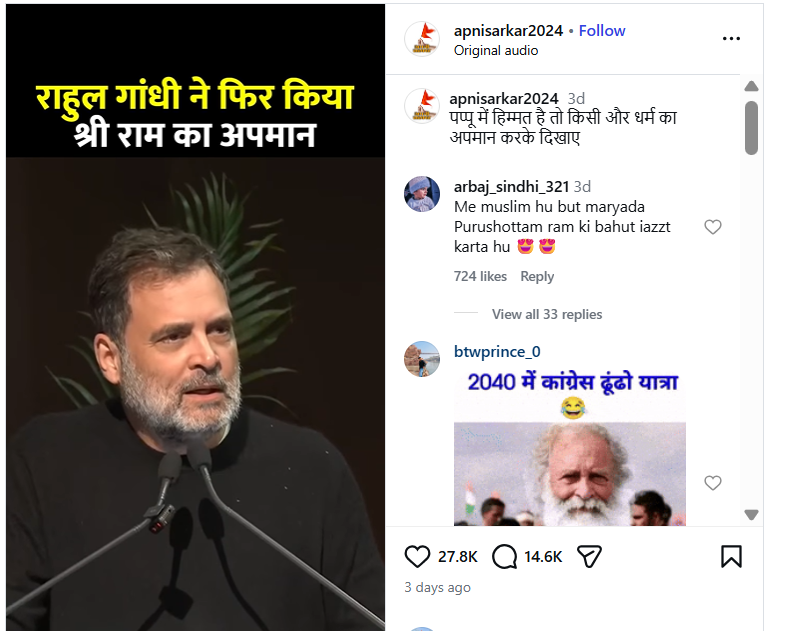
A video of the Leader of the Opposition in the Lok Sabha and Congress MP Rahul Gandhi is being widely shared on social media. In the clip, Gandhi is seen saying that he does not know what “G Gram G” is. Several users are sharing the video with the claim that Rahul Gandhi insulted Lord Ram. However, CyberPeace research found that the claim is misleading. Rahul Gandhi was not referring to Lord Ram in the video. Instead, he was speaking about a newly introduced law titled Viksit Bharat–G RAM G (VB–G RAM G), which has been brought in to replace the Mahatma Gandhi National Rural Employment Guarantee Act (MGNREGA). The viral clip has been shared with a false narrative.
Claim
On January 22, 2026, an Instagram user apnisarkar2024 shared the video claiming, “Rahul Gandhi once again insulted Shri Ram.” (Link, archive link, and screenshot available above)
- https://www.instagram.com/reel/DTzeiy0k3l5
- https://perma.cc/J3A3-NGBM?type=standard
Research
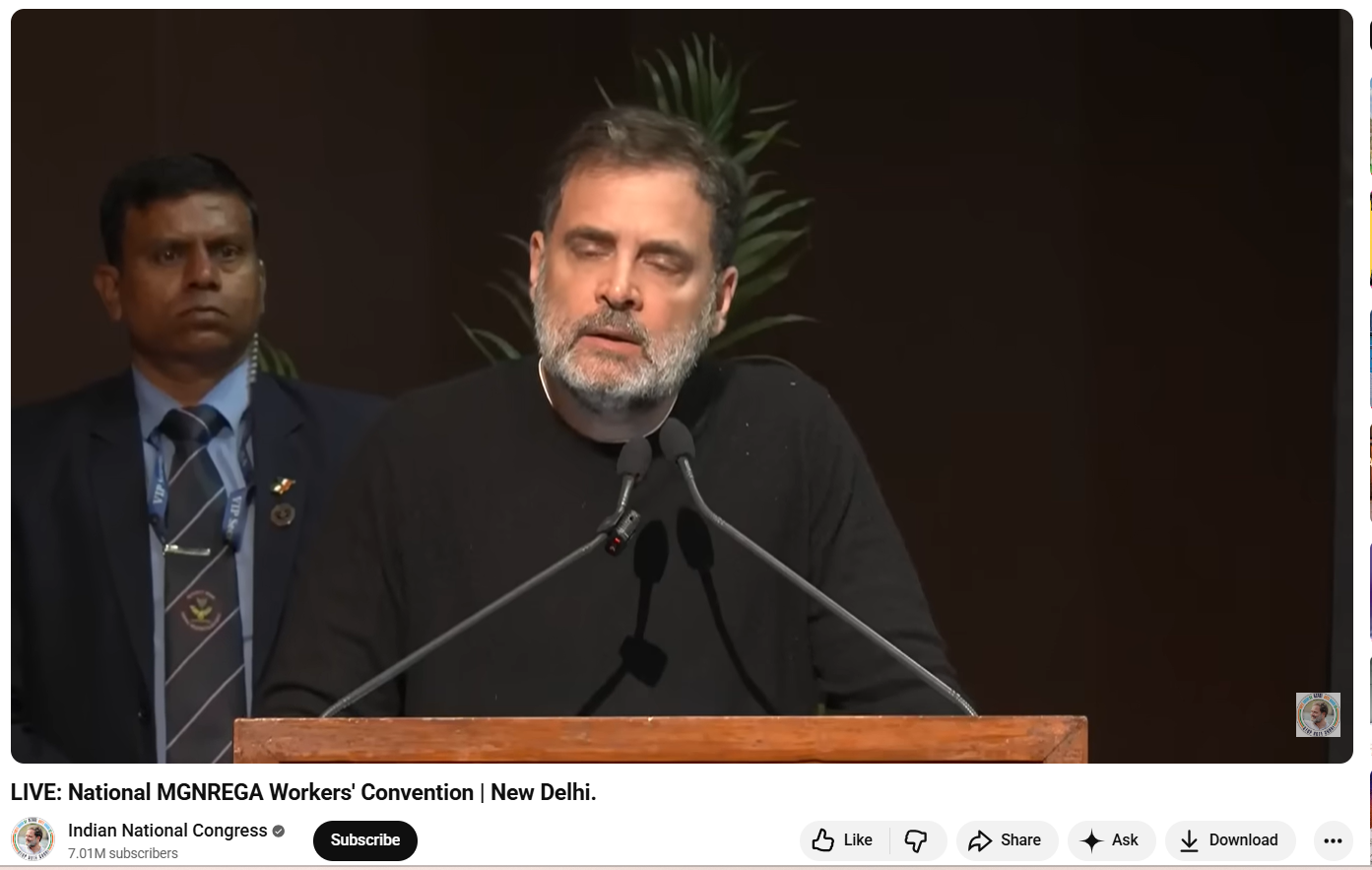
As part of the Research, we first closely examined the viral video. In the clip, Rahul Gandhi is heard saying: “I don’t know what Gram G is. I don’t even know the name of this new law… what is G Gram G…” At no point in the video does Rahul Gandhi mention Lord Ram or make any comment related to religion. To verify the context, we extracted keyframes from the viral clip and conducted a Google Lens search. This led us to a longer version of the same speech uploaded on the official YouTube channel of the Indian National Congress on January 22, 2026. The viral segment appears after the 39:50-minute mark.
The video is from the National MGNREGA Convention held in New Delhi, where Rahul Gandhi criticised the central government over the replacement of MGNREGA with the new VB–G RAM G law. During his speech, he expressed his opposition to the new legislation and stated that he was unfamiliar with its details. Throughout the address, he did not mention or refer to Lord Ram in any manner.
Conclusion
Rahul Gandhi’s remarks in the viral video were related to the newly introduced VB–G RAM G law and were part of his criticism of the central government’s policy decisions. He did not insult Lord Ram. The video is being shared on social media with a misleading and false claim.
Related Blogs

Executive Summary:
A dramatic image circulating online, showing a Boeing 787 of Air India engulfed in flames after crashing into a building in Ahmedabad, is not a genuine photograph from the incident. Our research has confirmed it was created using artificial intelligence.

Claim:
Social media posts and forwarded messages allege that the image shows the actual crash of Air India Flight AI‑171 near Ahmedabad airport on June 12, 2025.

Fact Check:
In our research to validate the authenticity of the viral image, we conducted a reverse image search and analyzed it using AI-detection tools like Hive Moderation. The image showed clear signs of manipulation, distorted details, and inconsistent lighting. Hive Moderation flagged it as “Likely AI-generated”, confirming it was synthetically created and not a real photograph.

In contrast, verified visuals and information about the Air India Flight AI-171 crash have been published by credible news agencies like The Indian Express and Hindustan Times, confirmed by the aviation authorities. Authentic reports include on-ground video footage and official statements, none of which feature the viral image. This confirms that the circulating photo is unrelated to the actual incident.

Conclusion:
The viral photograph is a fabrication, created by AI, not a real depiction of the Ahmedabad crash. It does not represent factual visuals from the tragedy. It’s essential to rely on verified images from credible news agencies and official investigation reports when discussing such sensitive events.
- Claim: An Air India Boeing aircraft crashed into a building near Ahmedabad airport
- Claimed On: Social Media
- Fact Check: False and Misleading

Introduction
A hacking operation has corrupted data on Madhya Pradesh's e-Nagarpalika portal, a vital online platform for paying civic taxes that serves 413 towns and cities in the state. Due to this serious security violation, the portal has been shut down. The incident occurred in December 2023. This affects citizens' access to vital online services like possessions, water, and municipal tax payments, as well as the issuing of obituaries and certain documents offered via online portal. Ransomware which is a type of malware encodes and conceals a victim's files, and data making it inaccessible and unreachable unless the attacker is paid a ransom. When ransomware initially appeared, encryption was the main method of preventing individuals' data from such threats.
The Intrusion and Database Corruption: Exposing the Breach's Scope
The extent of the assault on the e-Nagarpalika portal was revealed by the Principal Secretary of the Urban Administration and Housing Department of Madhya Pradesh, in a startling revelation. Cybercriminals carried out a highly skilled assault that led to the total destruction of the data infrastructure covering all 413 of the towns for which the website was responsible.
This significant breach represents a thorough infiltration into the core of the electronic civic taxation system, not just an arrangement. Because of the attackers' nefarious intent, the data integrity was compromised, raising questions about the safeguarding of private citizen data. The extent of the penetration reaches vital city services, causing a reassessment of the current cybersecurity safeguards in place.
In addition to raising concerns about the privacy of personal information, the hacked information system casts doubt on the availability of crucial municipal services. Among the vital services affected by this cyberattack are marriage licenses, birth and death documents, and the efficient handling of possessions, water, and municipal taxes.
The weaknesses of electronic systems, which are the foundation of contemporary civic services, are highlighted by this incident. Beyond the attack's immediate interruption, citizens now have to deal with concerns about the security of their information and the availability of essential services. This tragedy is a clear reminder of the urgent need for robust safety safeguards as authorities work hard to control the consequences and begin the process of restoration.
Offline Protections in Place
The concerned authority informed the general population that the offsite data, which has been stored up on recordings every three days, is secure despite the online attack. This preventive action emphasises how crucial offline restores are to lessening the effects of these kinds of cyberattacks. The choice to keep the e-Nagarpalika platform offline until a certain time highlights how serious the matter is and how urgently extensive reconstruction must be done to restore the online services offer
Effect on Civic Services
The e-Nagarpalika website is crucial to providing online municipal services, serving as an invaluable resource for citizens to obtain necessary paperwork and carry out diverse transactions. Civic organisations have been told to function offline while the portal remains unavailable until the infrastructure is fully operational. This interruption prompts worries about possible delays and obstacles citizens face when getting basic amenities during this time.
Examination and Quality Control
Information technology specialists are working diligently to look into the computer virus and recover the website, in coordination with the Madhya Pradesh State Electronic Development Corporation Limited, the state's cyber police, and the Indian Computer Emergency Response Team (CERT-In). Reassuringly for impacted citizens, authorities note that there is currently no proof of data leaks arising from the hack.
Conclusion
The computerised attack on the e-Nagarpalika portal in Madhya Pradesh exposes the weakness of computer networks. It has affected the essential services to public services offered via online portal. The hack, which exposed citizen data and interfered with vital services, emphasises how urgently strong safety precautions are needed. The tragedy is a clear reminder of the need to strengthen technology as authorities investigate and attempt to restore the system. One bright spot is that the offline defenses in place highlight the significance of backup plans in reducing the impact of cyberattacks. The ongoing reconstruction activities demonstrate the commitment to protecting public data and maintaining the confidentiality of essential city operations.
References
- https://government.economictimes.indiatimes.com/tag/cyber+attack
- https://www.techtarget.com/searchsecurity/definition/ransomware#:~:text=Ransomware%20is%20a%20type%20of,accessing%20their%20files%20and%20systems.
- https://www.business-standard.com/india-news/mp-s-e-nagarpalika-portal-suffers-cyber-attack-data-corrupted-officials-123122300519_1.html
- https://www.freepressjournal.in/bhopal/mp-govts-e-nagar-palika-portal-hacked-data-of-over-400-cities-leaked

Introduction
Since users are now constantly retrieving critical data on their mobile devices, fraudsters are now focusing on these devices. App-based, network-based, and device-based vulnerabilities are the three main ways of attacking that Mobile Endpoint Security names as mobile threats. Composed of the following features: program monitoring and risk, connection privacy and safety, psychological anomaly and reconfiguration recognition, and evaluation of vulnerabilities and management, this is how Gartner describes Mobile Threat Defense (MTD).
The widespread adoption and prevalence of cell phones among consumers worldwide have significantly increased in recent years. Users of these operating system-specific devices can install a wide range of software, or "apps," from online marketplaces like Google Play and the Apple App Store. The applications described above are the lifeblood of cell phones; they improve users' daily lives and augment the devices' performance. The app marketplaces let users quickly search for and install new programs, but certain malicious apps/links/websites can also be the origin of malware hidden among legitimate apps. These days, there are many different security issues and malevolent attacks that might affect mobile devices.
Unveiling Malware Landscape
The word "malware" refers to a comprehensive category of spyware intended to infiltrate networks, steal confidential data, cause disruptions, or grant illegal access. Malware can take many forms, such as Trojan horses, worms, ransomware, infections, spyware, and adware. Because each type has distinct goals and features, security specialists face a complex problem. Malware is a serious risk to both people and businesses. Security incidents, monetary losses, harm to one's credibility, and legal repercussions are possible outcomes. Understanding malware's inner workings is essential to defend against it effectively. Malware analysis is helpful in this situation. The practice of deconstructing and analysing dangerous software to comprehend its behaviour, operation, and consequences is known as malware analysis.Major threats targeting mobile phones
Viruses: Viruses are self-renewing programs that can steal data, launch denial of service assaults, or enact ransomware strikes. They spread by altering other software applications, adding malicious code, and running it on the target's device. Computer systems all over the world are still infected with viruses, which attack different operating systems like Mac and Microsoft Windows, even though there is a wealth of antiviral programs obtainable to mitigate their impacts.
Worms: Infections are independent apps that propagate quickly and carry out payloads—such as file deletion or the creation of botnets—to harm computers. Worms, in contrast to viruses, usually harm a computer system, even if it's just through bandwidth use. By taking advantage of holes in security or other vulnerabilities on the target computer, they spread throughout computer networks.
Ransomware: It causes serious commercial and organisational harm to people and businesses by encrypting data and demanding payment to unlock it. The daily operations of the victim organisation are somewhat disrupted, and they need to pay a ransom to get them back. It is not certain, though, that the financial transaction will be successful or that they will receive a working translation key.
Adware: It can be controlled via notification restrictions or ad-blockers, tracks user activities and delivers unsolicited advertisements. Adware poses concerns to users' privacy even though it's not always malevolent since the information it collects is frequently combined with information gathered from other places and used to build user profiles without their permission or knowledge.
Spyware: It can proliferate via malicious software or authentic software downloads, taking advantage of confidential data. This kind of spyware gathers data on users' actions without their authorisation or agreement, including:Internet activityBanking login credentialsPasswordsPersonally Identifiable Information (PII)
Navigating the Mobile Security Landscape
App-Centric Development: Regarding mobile security, app-centric protections are a crucial area of focus. Application authorisations should be regularly reviewed and adjusted to guarantee that applications only access the knowledge that is essential and to lower the probability of data misuse. Users can limit hazards and have greater oversight over their confidentiality by closely monitoring these settings. Installing trustworthy mobile security apps also adds another line of protection. With capabilities like app analysis, real-time protection, and antivirus scanning, these speciality apps strengthen your gadget's protection against malware and other harmful activity.
Network Security: Setting priorities for secure communication procedures is crucial for safeguarding confidential data and thwarting conceivable dangers in mobile security. Avoiding unprotected public Wi-Fi networks is essential since they may be vulnerable to cyberattacks. To lessen the chance of unwelcome entry and data surveillance, promote the usage of reliable, password-protected networks instead. Furthermore, by encrypting data transfer, Virtual Private Networks (VPNs) provide additional protection and make it more difficult for malevolent actors to corrupt information. To further improve security, avoid using public Wi-Fi for essential transactions and hold off until a secure network is available. Users can strengthen their handheld gadgets against possible privacy breaches by implementing these practices, which can dramatically lower the risk of data eavesdropping and illegal access.
Constant development: Maintaining a robust mobile security approach requires a dedication to constant development. Adopt a proactive stance by continuously improving and modifying your security protocols. By following up on recurring outreach and awareness campaigns, you can stay updated about new hazards. Because cybersecurity is a dynamic field, maintaining one step ahead and utilising emerging technologies is essential. Stay updated with security changes, implement the newest safeguards, and incorporate new industry standard procedures into your plan. This dedication to ongoing development creates a flexible barrier, strengthening your resistance to constantly evolving mobile security threats.
Threat emergency preparedness: To start, familiarise yourself with the ever-changing terrain associated with mobile dangers to security. Keep updated on new threats including malware, phishing, and illegal access.
Sturdy Device Management: Put in place a thorough approach to device management. This includes frequent upgrades, safe locking systems, and additional safeguarding capabilities like remote surveillance and erasing.
Customer Alertness: Emphasise proper online conduct and acquaint yourself and your team with potential hazards, such as phishing efforts.
Dynamic Measures for a Robust Wireless Safety Plan
In the dynamic field of mobile assurances, taking a proactive strategy is critical. To strengthen safeguards, thoroughly research common risks like malware, phishing, and illegal access. Establish a strong device management strategy that includes frequent upgrades, safe locking mechanisms, and remote monitoring and deletion capabilities for added security.
Promoting user awareness by educating people so they can identify and block any hazards, especially regarding phishing attempts. Reduce the dangers of data eavesdropping and illegal access by emphasising safe communication practices, using Virtual Private Networks (VPNs), and avoiding public Wi-Fi for essential transactions.
Pay close attention to app-centric integrity by periodically checking and modifying entitlements. Downloading trustworthy mobile security apps skilled at thwarting malware and other unwanted activity will enhance your smartphone's defenses. Lastly, create an atmosphere of continuous development by keeping up with new threats and utilising developing technology to make your handheld security plan more resilient overall.
Conclusion
Mobile privacy threats grow as portable electronics become increasingly integrated into daily activities. Effective defense requires knowledge of the various types of malware, such as worms, ransomware, adware, and spyware. Tools for Mobile Threat Defense, which prioritise vulnerability assessment, management, anomaly detection, connection privacy, and program monitoring, are essential. App-centric development, secure networking procedures, ongoing enhancement, threat readiness, strong device control, and user comprehension are all components of a complete mobile security strategy. People, as well as organisations, can strengthen their defenses against changing mobile security threats by implementing dynamic measures and maintaining vigilance, thereby guaranteeing safe and resilient mobile surrounding.
References
https://www.titanfile.com/blog/types-of-computer-malware/
https://www.simplilearn.com/what-is-a-trojan-malware-article
https://www.linkedin.com/pulse/latest-anti-analysis-tactics-guloader-malware-revealed-ukhxc/?trk=article-ssr-frontend-pulse_more-articles_related-content-card


