#FactCheck: Old clip of Greenland tsunami depicts as tsunami in Japan
Executive Summary:
A viral video depicting a powerful tsunami wave destroying coastal infrastructure is being falsely associated with the recent tsunami warning in Japan following an earthquake in Russia. Fact-checking through reverse image search reveals that the footage is from a 2017 tsunami in Greenland, triggered by a massive landslide in the Karrat Fjord.

Claim:
A viral video circulating on social media shows a massive tsunami wave crashing into the coastline, destroying boats and surrounding infrastructure. The footage is being falsely linked to the recent tsunami warning issued in Japan following an earthquake in Russia. However, initial verification suggests that the video is unrelated to the current event and may be from a previous incident.
Fact Check:
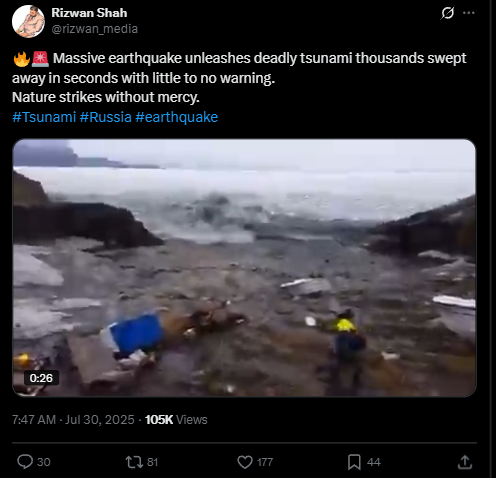
The video, which shows water forcefully inundating a coastal area, is neither recent nor related to the current tsunami event in Japan. A reverse image search conducted using keyframes extracted from the viral footage confirms that it is being misrepresented. The video actually originates from a tsunami that struck Greenland in 2017. The original footage is available on YouTube and has no connection to the recent earthquake-induced tsunami warning in Japan
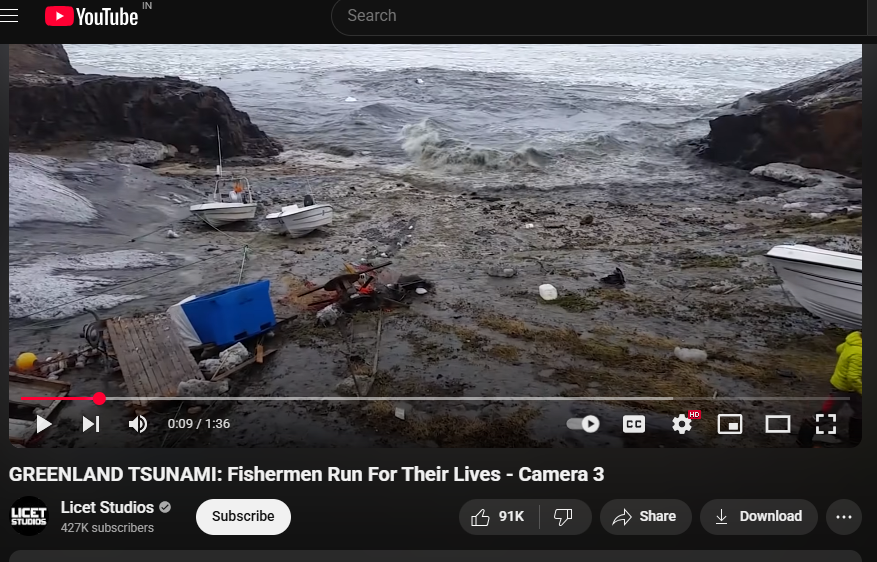
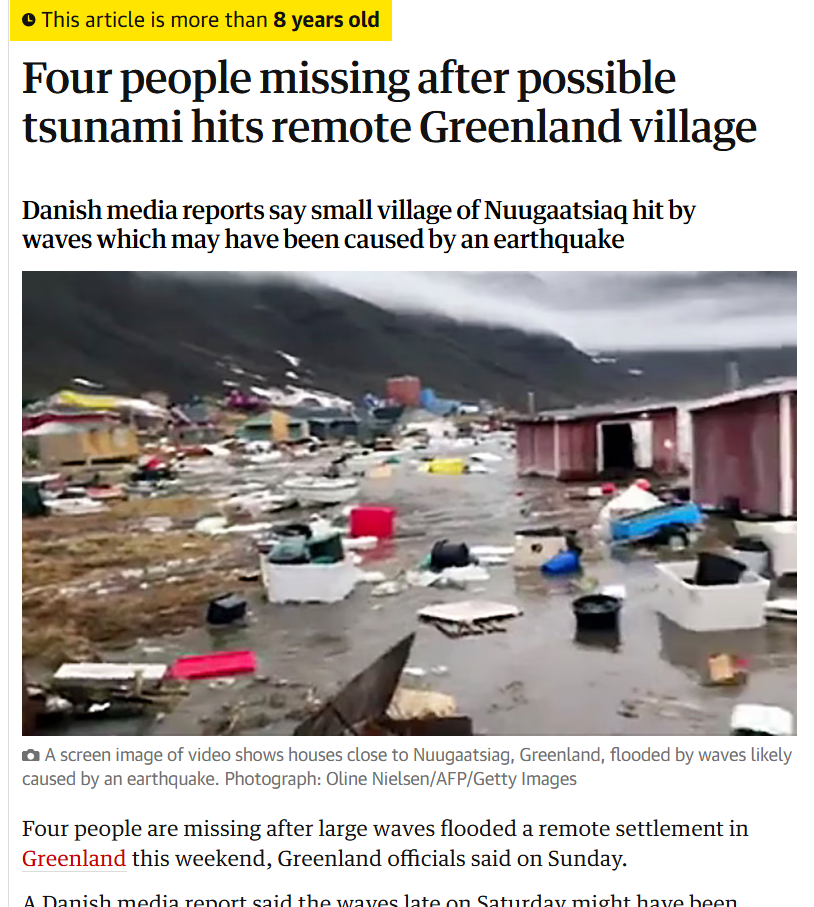
The American Geophysical Union (AGU) confirmed in a blog post on June 19, 2017, that the deadly Greenland tsunami on June 17, 2017, was caused by a massive landslide. Millions of cubic meters of rock were dumped into the Karrat Fjord by the landslide, creating a wave that was more than 90 meters high and destroying the village of Nuugaatsiaq. A similar news article from The Guardian can be found.
Conclusion:
Videos purporting to depict the effects of a recent tsunami in Japan are deceptive and repurposed from unrelated incidents. Users of social media are urged to confirm the legitimacy of such content before sharing it, particularly during natural disasters when false information can exacerbate public anxiety and confusion.
- Claim: Recent natural disasters in Russia are being censored
- Claimed On: Social Media
- Fact Check: False and Misleading
Related Blogs

Technology has revolutionized our lives, offering countless benefits and conveniences that make our daily lives more accessible and connected. However, with these benefits come potential challenges and risks that can impact our digital experiences. In this article, we have gathered expert advice on the impact of technology use in our daily lives, including the importance of warranties and tech protection in safeguarding our technology investments. Our experts offer invaluable insights and guidance on using technology safely and effectively while protecting us from unexpected costs or problems. Whether you’re a casual user or a technology enthusiast, our experts’ insights will help you navigate the world of technology with confidence and peace of mind.
How to protect kids from online abuse in the modern era of technology?
“As parents, it’s important to acknowledge that online child abuse is a widespread problem that we need to address. But does this mean we should ban technology from our children’s lives? Absolutely not! Technology is an integral part of our children’s lives, providing numerous benefits. Instead, we should think of practical ways to minimize the risks of online abuse. Many parents today depend on parental control apps like Mobicip to safeguard their children’s online activities and build healthy digital habits. These apps allow parents to supervise their child’s online behavior, restrict screen time, prevent access to certain websites and applications, filter inappropriate content, and get instant notifications about dangerous interactions or inappropriate content. Parents feel reassured and free of worry, knowing that their children’s online surroundings are secure and protected. In addition to using a parental control app, we must also focus on building a strong connection with our kids. By initiating conversations about their digital lives, we can understand their digital world, educate them about the potential risks and dangers of the internet, and teach them how to stay safe. By being proactive and engaged in our children’s digital lives, we can protect them from online abuse while still allowing them to benefit from technology.”
How to increase engagement in online classes via technology?
“Online classes have gained immense popularity in recent years due to their many advantages. However, online educators face several challenges that can impede the effectiveness of their classes, one of which is the lack of engagement from students. To address this challenge, it is crucial to adopt certain strategies that can increase student engagement and create a more meaningful learning environment.
One effective strategy is to limit the number of chokepoints that students may face while enrolling in a class. This can be achieved by using booking and scheduling technology that provides students with a hassle-free experience. The system sends regular reminders and notifications to learners about upcoming classes and assignments, helping them stay organized and committed to their learning.
Technology plays a vital role in improving communication between students and teachers and in increasing student engagement and participation during a session. Utilizing technology such as polling, chat boxes, and breakout rooms enables learners to actively participate in the class and share their perspectives, leading to more effective learning.
Personalization is also essential in creating a meaningful learning environment. A scheduling system can help create customized learning paths for each student, where they can progress at their own pace and focus on topics that interest them. This ensures that each student receives individual attention and is able to learn in a way that suits their learning style.
Moreover, gamification techniques can be used to make the learning process more fun and engaging. This includes using badges, points, and leaderboards to motivate learners to achieve their goals while competing with each other.”
Dr. Sukanya Kakoty, Omnify
How to choose the best due diligence software for your business?
“With a variety of solutions on the market, finding the best due diligence software for your business can be a tedious task. In addition to the software’s capabilities meeting your needs, there are other factors to consider when picking the right solution for your business. As due diligence involves the sharing of sensitive information, security is a key factor to consider. When browsing solutions, it is important to consider if their security features are up to industry standards. User-friendliness is another factor to consider when adopting a new due diligence software. Introducing a new tool should increase team efficiency, not disrupt your existing workflow. When searching for the perfect due diligence solution, pick one that meets the above criteria and more. DealRoom is a lifecycle deal management solution, providing pipeline, diligence, integration, and document management all under one platform. DealRoom’s user-friendly and intuitive features allow for customizable workflows to fit the specific needs of each user. DealRoom also offers industry-leading security features, including data encryption, granular permissions, and detailed audit logs, guaranteeing that your information is always protected. When choosing the best due diligence software for your business, consider a user-friendly, flexible, and secure solution.”
Why are backups important, and what is the safest way of doing them?
“Backups are important for several reasons. They help to protect against data loss, which can be caused by a variety of reasons, such as hardware failure, software corruption, natural disasters, or cyber-attacks. Backups also help to ensure that important data is available when needed, such as in the case of an emergency or system failure. Additionally, backups provide a way to recover deleted or corrupted files. This is also important because the loss of data can result in consequences such as financial loss, damage to reputation, and even legal issues. If not these, then loss of data may also lead to emotional effects in certain cases. A backup, however, can restore data quickly and avoid any significant disruption, emotional or otherwise. The safest way of doing backups is by following the 3-2-1 backup rule. This rule states that you should have at least three copies of your data, stored on at least two different storage media, with one copy stored offsite. This provides redundancy in case of a failure of one storage medium or location.
There are several methods of backing up data, including:
- External hard drives or USB drives: These are inexpensive and portable, making them a popular choice for personal backups. However, they can be lost or damaged, so it is important to keep them in a safe location and make regular backups.
- Cloud backups: These store data on remote servers, which can be accessed from anywhere with an internet connection. This provides an offsite backup solution, but it is important to choose a reputable provider and to ensure that the data is encrypted and secure.
- Network-attached storage (NAS): These are devices that connect to a network and provide centralized storage for multiple devices. They can be configured to automatically back up data from multiple devices on the network.
- Tape backups: These are less common but are still used by some businesses for the long-term storage of large amounts of data.
Regardless of the backup method chosen, it is important to regularly test backups regularly to ensure that they can be successfully restored in case of an emergency.”
What are the best trending electric toys for kids in 2023?
“Augmented Reality (AR) Toys: These toys blend the physical and digital world, providing an immersive experience. Popular examples include AR-enabled building sets and interactive storybooks that come to life through an app.
Educational Robotics: Robotics toys like the LEGO Mindstorms Robot Inventor and Sphero’s programmable robots have gained popularity for teaching coding, engineering, and problem-solving skills through hands-on play.”
Aside from security, what are some of the features of a VPN?
“Accessing geo-restricted content: One of the main benefits of using a VPN is its ability to bypass geographical restrictions in the world of flight prices, content, gaming, and more. Many websites and online services are only available in certain countries or regions. With a VPN, you can change your virtual location and access content that is otherwise blocked or unavailable in your country. Imagine you’re playing a game with friends; by using a VPN, you can improve your gaming experience by connecting to a server closer to the game’s host location and bypassing regional restrictions to access features unavailable in your region.
Increased privacy and anonymity: While security and privacy go hand in hand, VPNs offer more than just encryption. They also provide a level of anonymity by masking your IP address and making it difficult for websites and online services to track your online activity. This can be particularly useful for users who are concerned about their online privacy or who want to avoid targeted ads.
Faster internet speeds: Believe it or not, using a VPN can actually improve your internet speed in certain situations. If your internet service provider (ISP) is throttling your internet speed, a VPN can help you bypass this by encrypting your traffic and hiding it from your ISP. Additionally, some VPN providers offer dedicated servers that are optimized for faster speeds, reducing buffering and improving download and upload speeds.”
How does creating a website can help a home business?
“As a digital marketing consultant, I once worked with a client who had a home-based bakery business. She struggled to reach new customers beyond her local community and wanted to expand her reach and grow her business. After assessing her needs, I recommended that she create a website for her business. With the website, she could showcase her unique baked goods, provide a platform for online ordering, and expand her reach to customers beyond her local community. The website was designed to be visually appealing and user-friendly while effectively showcasing the brand and products in an attractive way. Additionally, the website was optimized for search engines and integrated with social media platforms to increase visibility and drive traffic to the site. Within a few months of launching the website, she saw an increase in orders. Customers could easily place orders through the website and leave reviews, which provided social proof and helped build trust with potential customers. Also used data analytics to track customer behavior and make data-driven decisions to improve the website and marketing strategy. The website became a valuable asset for her business, helping her to expand her reach, increase sales, and gather valuable customer data. Overall, creating a website helped her home-based business to grow and thrive in a competitive marketplace.”
Lito James, MassivePeak.com
How can technology be utilized to enhance productivity for remote teams working from home?
“Our team facilitates strategic planning sessions and we’re frequently working with teams that are working remotely. Here are a few of our best tips for productivity:
- Clear strategy: As teams have fewer touch points, it’s critical they are aligned and bought into the direction of the organization.
- Clear big rocks for the week. Make sure you’re not just busy but doing things that will move the needle on your strategic goals
- Clear accountability: Basecamp or other project management tools to help make sure nothing falls through the cracks
- Clear communication: Schedule the right meetings, so you are connecting at the right times to deliver important work and align on important topics.
- Clear agendas: When you do meet, make sure you’re coming together, staying focused, and getting the most important information across
Creating the right strategy and the right structure to keep it moving forward will help your team drive your most important outcomes, regardless of if you’re working in an office or remotely.
Anthony Taylor, SME Strategy Consulting
How to monitor your kids’ activities online?
“As a father of two kids and the founder of TheSweetBits.com, a website dedicated to providing guides on software and apps, I have extensive experience in monitoring my children’s online activities. Over the years, I have tested and reviewed numerous parental control apps and software to ensure my children’s online safety. When it comes to monitoring your kids’ activity online, it’s crucial to find a balance between keeping them safe and respecting their privacy. One of the most effective ways to achieve this balance is by using parental control software that allows you to set limits on their device usage, restrict access to inappropriate content, and monitor their online activity. However, it’s important to note that parental control software is not a substitute for good communication with your kids. You should have regular conversations with them about online safety and the potential dangers of the internet. By establishing trust and open communication, you can work together to create a safe and responsible online environment for your family. As I always say, ‘Parental control software is just one tool in the toolbox of responsible parenting’.”
How to plan the best online date with the help of technology?
“To plan a date online with the help of technology, we recommend using a reservation app like OpenTable to make dinner reservations. Not only will this let her know you thought ahead with the smaller details, but it will also ensure a smooth date by eliminating a long waiting time for a table to open up.”
What are the benefits of teaching kids to code and how to make it fun?
“The ability to code has become increasingly important in the modern world due to the rapid advancement of technology and its integration into nearly every aspect of our lives. This is something that will only continue as our children grow up and enter the world at large as the demand for workers with coding skills continues to grow rapidly. Teaching kids to code offers numerous benefits beyond just developing technical skills and getting them future-ready. It promotes problem-solving abilities, critical thinking, and logical reasoning, all of which are essential in today’s digital age. Additionally, coding can increase creativity and encourage children to think outside the box. However, it’s important to make coding fun and engaging for kids rather than a dull and tedious task. One way to make it exciting is to introduce gamification elements, such as incorporating fun characters or adding game-like challenges, and there are loads of great apps to get them started with. We love CodeSpark Academy, Lego Boost, and Tynker. Another approach is to encourage group work or peer learning, where children can work together to solve problems and learn from each other. Ultimately, making coding fun and enjoyable can ignite children’s interest in technology and set them on a path to explore new and exciting opportunities in the future.”
Are dating apps useful in the modern dating era and how to find the correct one?
“Dating apps have become a popular tool for modern daters to find potential partners. However, they also come with their own set of problems. One of the biggest issues with current dating apps is that they focus too much on superficial factors such as sexual attraction, rather than deeper compatibility and true attraction. This can lead to frustration and disappointment for users who are seeking more meaningful connections. Fortunately, AI technology is starting to offer solutions to these problems. By using machine learning algorithms and data analysis, apps like Iris Dating are able to help users find potential matches based on more than just superficial qualities. Iris uses a process called “iris training” to learn each user’s unique preferences and suggest compatible matches accordingly. This approach allows users to connect with people to whom they are really attracted, leading to more meaningful and lasting relationships. When it comes to finding the right dating app, it’s important to do your research and choose one that aligns with your values and preferences. Look for apps that prioritize true attraction and use AI technology to help you find meaningful matches. Don’t be afraid to try out multiple apps until you find one that feels right for you. Overall, while dating apps have their flaws, AI-powered apps like Iris offer hope for a more personalized and meaningful dating experience. By leveraging the power of technology, we can make the search for love a little bit easier and a lot more enjoyable.”
What are some IT risk management tips for home businesses?
“As more and more people turn to home-based businesses, IT security for these operations is becoming an increasingly important concern. From data breaches to cyberattacks, the risks you face as a home business owner are the same as those faced by larger enterprises. So, what are some IT risk management tips for home businesses? First, consider using a virtual private network or VPN to enhance the security of your online communications. Additionally, enable two-factor authentication for all of your accounts, including any cloud services you use. Practice good password hygiene, regularly updating passwords and avoiding easily guessable or common passwords. Finally, consider investing in cybersecurity insurance to protect your business in the event of a cyberattack or data breach. By taking these steps to mitigate IT risks, you can help ensure your home business stays secure and successful. Below are some additional suggestions to help you stay vigilant and set up your home business for longevity.
-Keep Your Software Up to Date: One of the best ways to reduce your risk of being hacked is to keep your software up to date. This includes both your operating system and any applications you have installed.
-Use a Firewall: A firewall is a piece of software that helps to block incoming connections from untrusted sources. By blocking these connections, you can help to prevent hackers from gaining access to your system.
-Use Anti-Virus Software: In addition to using a firewall, you should also use anti-virus software. Anti-virus software helps to protect your system from viruses and other malware. These programs work by scanning your system for known threats and then quarantining or deleting any files that are found to be infected.
-Back Up Your Data Regularly: Finally, it is important to back up your data regularly. This way, if your system is ever compromised, you will not lose any important files or data.
-Encrypt Your Data: If you are storing sensitive data on your computer, it is important to encrypt it to protect it from being accessed by unauthorized individuals. Encryption is a process of transforming data into a format that cannot be read without a decryption key. There are many different encryption algorithms that you can use, so make sure to choose one that is appropriate for the type of data you are encrypting.”
What are the benefits of giving your child a smartphone?
“If you’re teetering back and forth on getting your child a smartphone, consider these benefits as you make your decision:
• Connection. Smartphones keep kids in contact with friends and family—for fun and function! From school to extracurricular activities, kids can easily let their parents and caregivers know about late pickups, ride requests, and other changes of plans.
• Safety. If your child or someone they’re with gets hurt, their smartphone could save a life! And with built-in GPS, their location is always accessible. Plus, parental controls and other smartphone safeguards offer even more protection.
• Convenience. Life is a little easier when your child has a smartphone, plain and simple! You can call each other, send texts, and always know where they are.
• Acceptance. These days, it’s uncommon for kids to not have smartphones. With a smartphone, your child feels belonging and inclusion among their peers.
• Development. Having something as valuable as a smartphone teaches children responsibility and accountability. And with a smartphone of their own, your child will learn how to use technology in an appropriate, safe, and disciplined way.
• Education. Smartphones are incredible teaching tools! Educational apps, videos, and games can keep kids sharp. Plus, smartphones can introduce them to new hobbies and interests!”
How is technology promoting health and wellness?
“Technology has revolutionized the healthcare industry and is playing an increasingly important role in promoting health and wellness. Here are some ways in which technology has helped:
Wearable technology: Wearable devices, such as fitness trackers and smartwatches, are becoming increasingly popular. These devices can track a person’s physical activity, sleep patterns, heart rate, and more. They provide valuable insights into a person’s health and wellness and can help motivate them to make positive lifestyle changes.
Telehealth: Telemedicine allows patients to receive medical care remotely through video conferencing, phone calls, or other digital means. It has also allowed fitness professionals to work with more people who aren’t in a local market via video conferencing, webinars, etc.
Mobile Apps: There are a plethora of mobile apps available that promote health and wellness. These apps can help users track their diet and exercise, manage chronic conditions, and access medical information.
Virtual Reality: Virtual reality (VR) is being used in healthcare to treat conditions such as anxiety, phobias, and PTSD. VR can also be used for physical therapy and rehabilitation.
Overall, technology is playing an increasingly important role in promoting health and wellness, and it is likely that we will see even more innovative uses of technology in the healthcare industry in the future.”

Executive Summary:
The viral video circulating on social media about the Indian men’s 4x400m relay team recently broke the Asian record and qualified for the finals of the world Athletics championship. The fact check reveals that this is not a recent event but it is from the World World Athletics Championships, August 2023 that happened in Budapest, Hungary. The Indian team comprising Muhammed Anas Yahiya, Amoj Jacob, Muhammed Ajmal Variyathodi, and Rajesh Ramesh, clocked a time of 2 minutes 59.05 seconds, finishing second behind the USA and breaking the Asian record. Although they performed very well in the heats, they only got fifth place in the finals. The video is being reuploaded with false claims stating its a recent record.

Claims:
A recent claim that the Indian men’s 4x400m relay team set the Asian record and qualified to the world finals.




Fact Check:
In the recent past, a video of the Indian Men’s 4x400m relay team which set a new Asian record is viral on different Social Media. Many believe that this is a video of the recent achievement of the Indian team. Upon receiving the posts, we did keyword searches based on the input and we found related posts from various social media. We found an article published by ‘The Hindu’ on August 27, 2023.

According to the article, the Indian team competed in the World Athletics Championship held in Budapest, Hungary. During that time, the team had a very good performance. The Indian team, which consisted of Muhammed Anas Yahiya, Amoj Jacob, Muhammed Ajmal Variyathodi, and Rajesh Ramesh, completed the race in 2:58.47 seconds, coming second after the USA in the event.
The earlier record was 3.00.25 which was set in 2021.

This was a new record in Asia, so it was a historic moment for India. Despite their great success, this video is being reshared with captions that implies this is a recent event, which has raised confusion. We also found various social media posts posted on Aug 26, 2023. We also found the same video posted on the official X account of Prime Minister Narendra Modi, the caption of the post reads, “Incredible teamwork at the World Athletics Championships!
Anas, Amoj, Rajesh Ramesh, and Muhammed Ajmal sprinted into the finals, setting a new Asian Record in the M 4X400m Relay.
This will be remembered as a triumphant comeback, truly historical for Indian athletics.”

This reveals that this is not a recent event but it is from the World World Athletics Championships, August 2023 that happened in Budapest, Hungary.
Conclusion:
The viral video of the recent news about the Indian men’s 4x400m relay team breaking the Asian record is not true. The video was from August 2023 that happened at the World Athletics Championships, Budapest. The Indian team broke the Asian record with 2 minutes 59.05 seconds in second position while the US team obtained first position with a timing of 2 minutes 58.47 seconds. However, the video circulated projecting as a recent event is misleading and false.
- Claim: Recent achievement of the Indian men's 4x400m relay team broke the Asian record and qualified for the World finals.
- Claimed on: X, LinkedIn, Instagram
- Fact Check: Fake & Misleading
.webp)
Introduction
The rise of misinformation, disinformation, and synthetic media content on the internet and social media platforms has raised serious concerns, emphasizing the need for responsible use of social media to maintain information accuracy and combat misinformation incidents. With online misinformation rampant all over the world, the World Economic Forum's 2024 Global Risk Report, notably ranks India amongst the highest in terms of risk of mis/disinformation.
The widespread online misinformation on social media platforms necessitates a joint effort between tech/social media platforms and the government to counter such incidents. The Indian government is actively seeking to collaborate with tech/social media platforms to foster a safe and trustworthy digital environment and to also ensure compliance with intermediary rules and regulations. The Ministry of Information and Broadcasting has used ‘extraordinary powers’ to block certain YouTube channels, X (Twitter) & Facebook accounts, allegedly used to spread harmful misinformation. The government has issued advisories regulating deepfake and misinformation, and social media platforms initiated efforts to implement algorithmic and technical improvements to counter misinformation and secure the information landscape.
Efforts by the Government and Social Media Platforms to Combat Misinformation
- Advisory regulating AI, deepfake and misinformation
The Ministry of Electronics and Information Technology (MeitY) issued a modified advisory on 15th March 2024, in suppression of the advisory issued on 1st March 2024. The latest advisory specifies that the platforms should inform all users about the consequences of dealing with unlawful information on platforms, including disabling access, removing non-compliant information, suspension or termination of access or usage rights of the user to their user account and imposing punishment under applicable law. The advisory necessitates identifying synthetically created content across various formats, and instructs platforms to employ labels, unique identifiers, or metadata to ensure transparency.
- Rules related to content regulation
The Information Technology (Intermediary Guidelines and Digital Media Ethics Code) Rules, 2021 (Updated as on 6.4.2023) have been enacted under the IT Act, 2000. These rules assign specific obligations on intermediaries as to what kind of information is to be hosted, displayed, uploaded, published, transmitted, stored or shared. The rules also specify provisions to establish a grievance redressal mechanism by platforms and remove unlawful content within stipulated time frames.
- Counteracting misinformation during Indian elections 2024
To counter misinformation during the Indian elections the government and social media platforms made their best efforts to ensure the electoral integrity was saved from any threat of mis/disinformation. The Election Commission of India (ECI) further launched the 'Myth vs Reality Register' to combat misinformation and to ensure the integrity of the electoral process during the general elections in 2024. The ECI collaborated with Google to empower the citizenry by making it easy to find critical voting information on Google Search and YouTube. In this way, Google has supported the 2024 Indian General Election by providing high-quality information to voters and helping people navigate AI-generated content. Google connected voters to helpful information through product features that show data from trusted institutions across its portfolio. YouTube showcased election information panels, featuring content from authoritative sources.
- YouTube and X (Twitter) new ‘Notes Feature’
- Notes Feature on YouTube: YouTube is testing an experimental feature that allows users to add notes to provide relevant, timely, and easy-to-understand context for videos. This initiative builds on previous products that display helpful information alongside videos, such as information panels and disclosure requirements when content is altered or synthetic. YouTube clarified that the pilot will be available on mobiles in the U.S. and in the English language, to start with. During this test phase, viewers, participants, and creators are invited to give feedback on the quality of the notes.
- Community Notes feature on X: Community Notes on X aims to enhance the understanding of potentially misleading posts by allowing users to add context to them. Contributors can leave notes on any post, and if enough people rate the note as helpful, it will be publicly displayed. The algorithm is open source and publicly available on GitHub, allowing anyone to audit, analyze, or suggest improvements. However, Community Notes do not represent X's viewpoint and cannot be edited or modified by their teams. A post with a Community Note will not be labelled, removed, or addressed by X unless it violates the X Rules, Terms of Service, or Privacy Policy. Failure to abide by these rules can result in removal from accessing Community Notes and/or other remediations. Users can report notes that do not comply with the rules by selecting the menu on a note and selecting ‘Report’ or using the provided form.
CyberPeace Policy Recommendations
Countering widespread online misinformation on social media platforms requires a multipronged approach that involves joint efforts from different stakeholders. Platforms should invest in state-of-the-art algorithms and technology to detect and flag suspected misleading information. They should also establish trustworthy fact-checking protocols and collaborate with expert fact-checking groups. Campaigns, seminars, and other educational materials must be encouraged by the government to increase public awareness and digital literacy about the mis/disinformation risks and impacts. Netizens should be empowered with the necessary skills and ability to discern fact and misleading information to successfully browse true information in the digital information age. The joint efforts by Government authorities, tech companies, and expert cyber security organisations are vital in promoting a secure and honest online information landscape and countering the spread of mis/disinformation. Platforms must encourage netizens/users to foster appropriate online conduct while using platforms and abiding by the terms & conditions and community guidelines of the platforms. Encouraging a culture of truth and integrity on the internet, honouring differing points of view, and confirming facts all help to create a more reliable and information-resilient environment.
References:
- https://www.meity.gov.in/writereaddata/files/Advisory%2015March%202024.pdf
- https://blog.google/intl/en-in/company-news/outreach-initiatives/supporting-the-2024-indian-general-election/
- https://blog.youtube/news-and-events/new-ways-to-offer-viewers-more-context/
- https://help.x.com/en/using-x/community-notes


