#FactCheck: No, PM Modi Did Not Appear in Royal Attire,Image Is AI-Generated
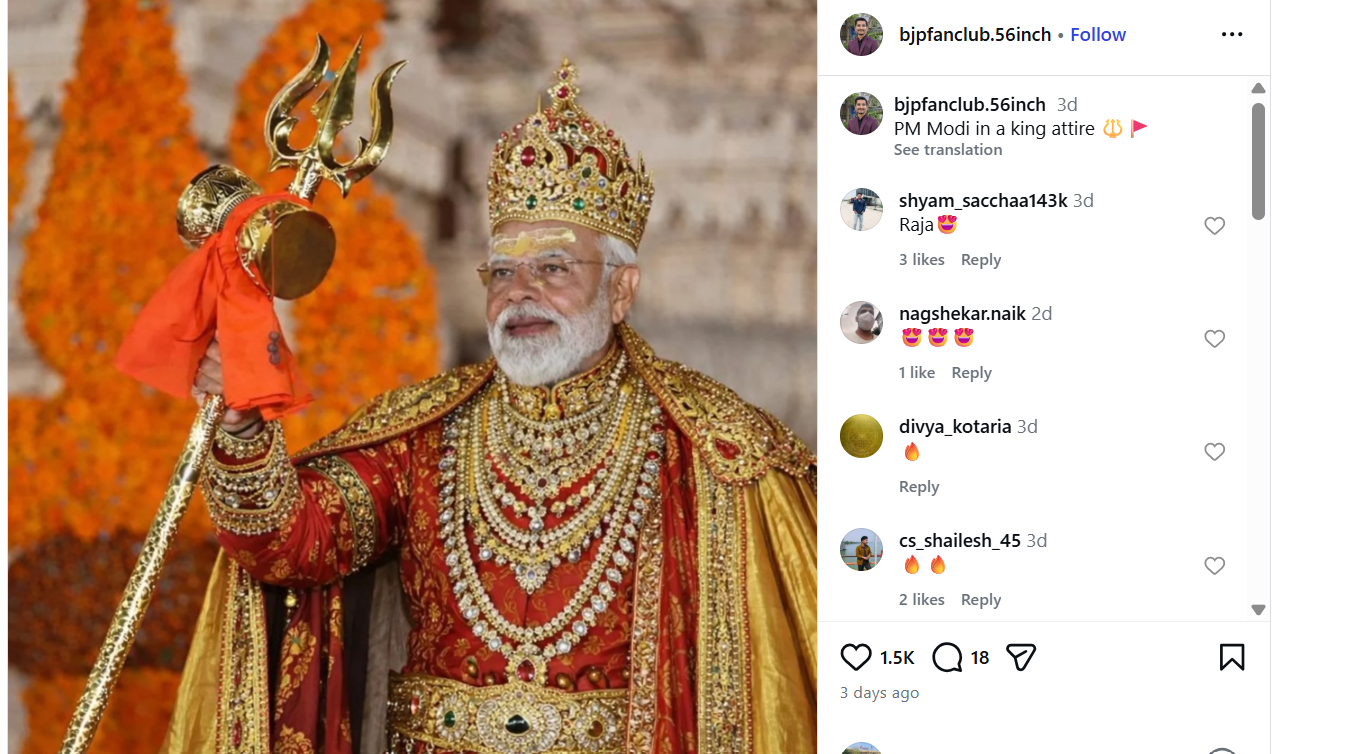
A photograph showing Prime Minister Narendra Modi holding a trident and dressed in royal attire is being widely shared on social media. Users circulating the image are claiming that it shows PM Modi in a regal outfit.
However, a verification by the Cyber Peace Foundation’s Research Desk has found that the claim is false. The investigation established that the viral image is not authentic and has been generated using Artificial Intelligence (AI).
Claim:
On January 11, 2026, several Instagram users shared the image with captions describing it as a photograph of Prime Minister Modi in royal attire.
Links and archived versions of the posts, along with screenshots, are provided below.
Fact Check:
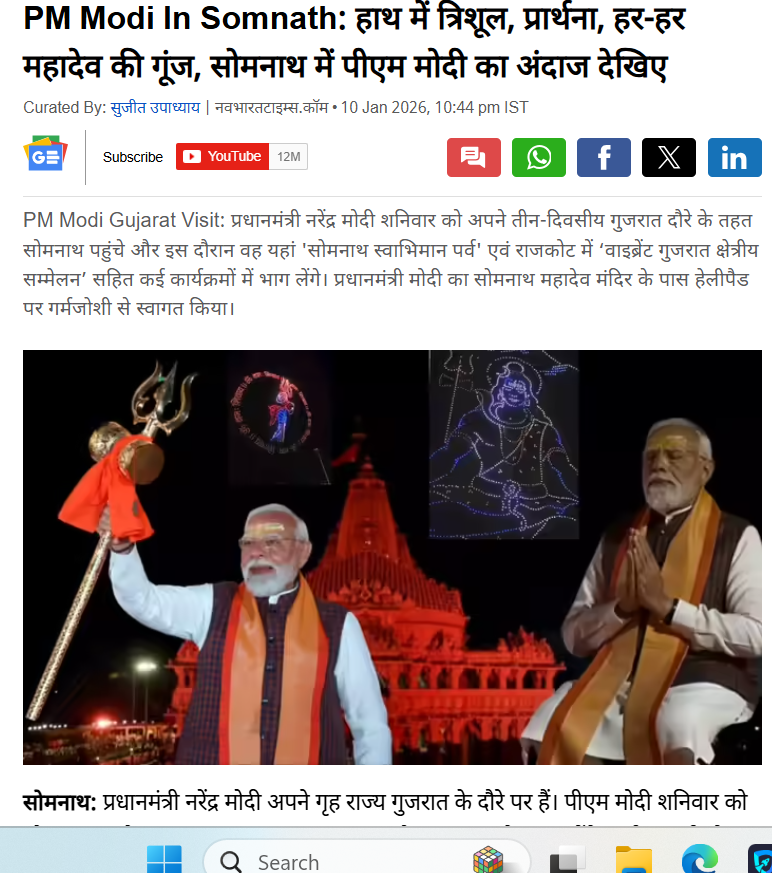
To verify the claim, relevant keywords such as “PM Modi holding trishul” were searched on Google. This led to a report published by Navbharat Times on January 10, 2025. The report features photographs of Prime Minister Modi holding a trident during his visit to the Somnath Temple. However, in the original images, he is seen wearing normal attire, not royal clothing as shown in the viral image. Link and screenshot
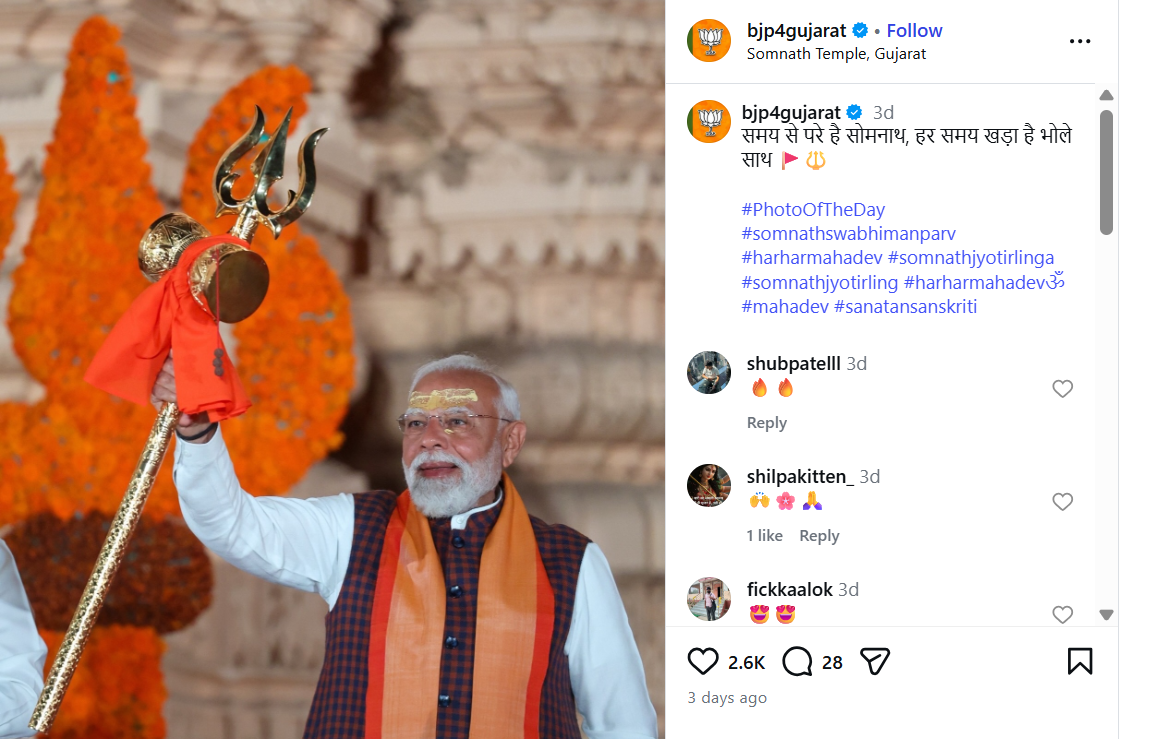
In the next step of the investigation, the original photograph was traced to the official Instagram account of BJP Gujarat, where it was posted on January 11, 2026. The post clearly identifies the image as being from Somnath Temple. Link and screenshot: https://www.instagram.com/p/DTVlb-9Da1V
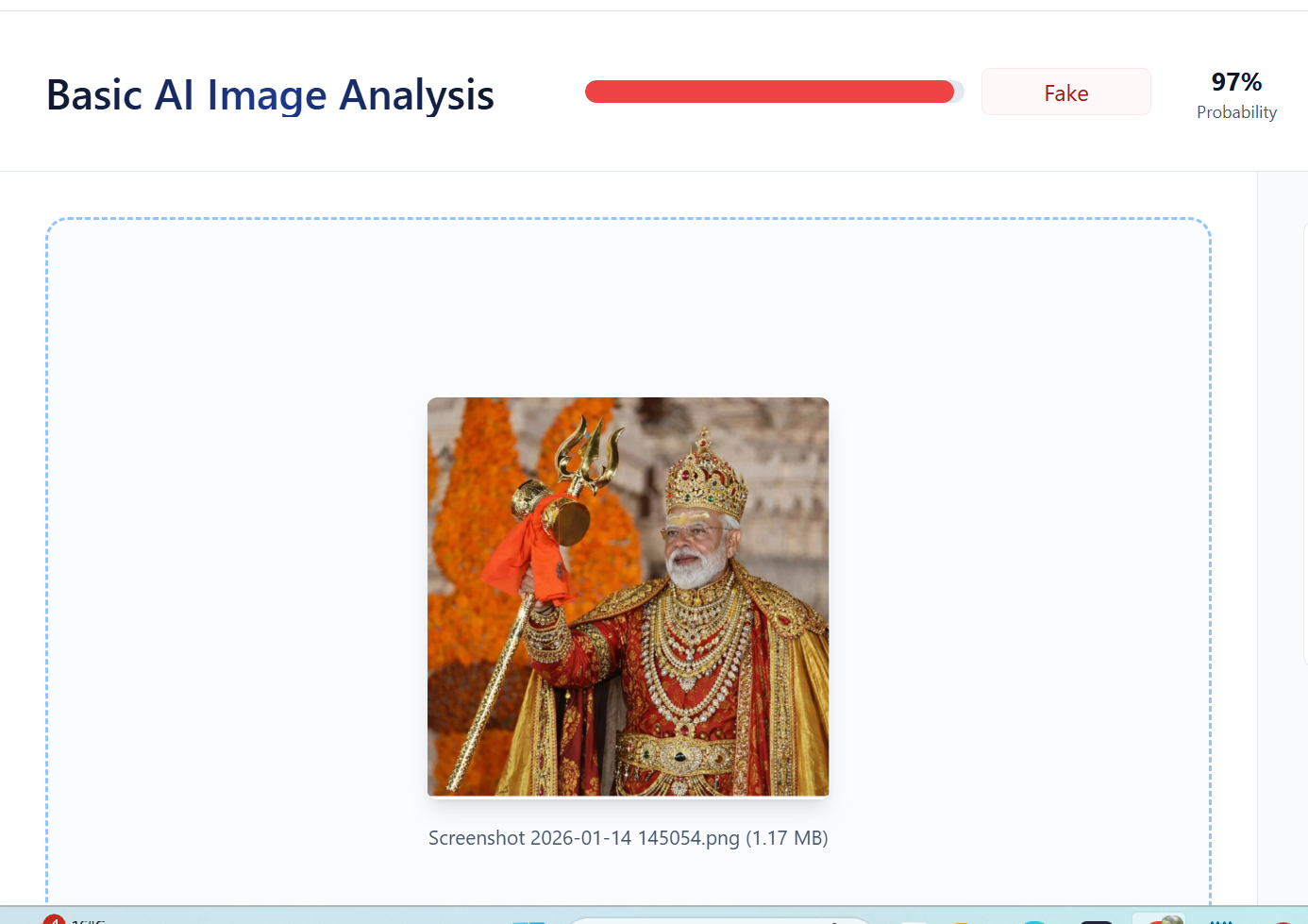
A close examination of the viral image raised suspicion about digital manipulation. The image was then analysed using the AI detection tool TruthScan. The tool’s assessment indicated a 97 percent likelihood that the image was AI-generated.
Further comparison between the viral image and the original photograph revealed that all visual elements match except the clothing, confirming that the attire was digitally altered using AI tools.
Conclusion
The claim that Prime Minister Narendra Modi appeared in royal attire is false. The Cyber Peace Foundation’s research confirms that the viral image was created using AI by altering the clothing in an original photograph taken during PM Modi’s visit to Somnath Temple. The manipulated image was shared online to mislead users.
Related Blogs
.jpeg)
Introduction
Quantum mechanics is not a new field. It finds its roots in the works of physicists such as Niels Bohr in the 1920s, and has informed the development of technologies like nuclear power in the past. But with developments in science and engineering, we are at the cusp of harnessing quantum mechanics for a new wave of real-world uses in sensing and metrology, computing, networking, security, and more. While at different stages of development, quantum technologies have the potential to revolutionise global security, economic systems, and digital infrastructure. The science is dazzling, but it is equally urgent to start preparing for its broader impact on society, especially regarding privacy and digital security. This article explores quantum computing, its threat to information integrity, and global interdependencies as they exist today, and discusses policy areas that should be addressed.
What Is Quantum Computing?
Classical computers use binary bits (0 or 1) to represent and process information. This binary system forms the base of modern computing. But quantum computers use qubits (quantum bits) as a basic unit, which can exist in multiple states ( 0, 1, both, or with other qubits) simultaneously due to quantum principles like superposition and entanglement. This creates an infinite range of possibilities in information processing and allows quantum machines to perform complex computations at speeds impossible for traditional computers. While still in their early stages, large-scale quantum computers could eventually:
- Break modern encryption systems
- Model complex molecules for drug discovery
- Optimise global logistics and financial systems
- Accelerate AI and machine learning
While this could eventually present significant opportunities in fields such as health innovation, material sciences, climate modelling, and cybersecurity, challenges will continue to arise even before the technology is ready for commercial application. Policymakers must start anticipating their impact.
Threats
Policy solutions surrounding quantum technologies will depend on the pace of development of the elements of the quantum ecosystem. However, the most urgent concerns regarding quantum computing applications are the risk to encryption and the impact on market competition.
1. Cybersecurity Threat: Digital infrastructure today (e.g., cloud services, networks, servers, etc.) across sectors such as government, banking and finance, healthcare, energy, etc., depends on encryption for secure data handling and communications. Threat actors can utilise quantum computers to break this encryption. Widely used asymmetric encryption keys, such as RSA or ECC, are particularly susceptible to being broken. Threat actors could "harvest now, decrypt later”- steal encrypted data now and decrypt it later when quantum capabilities mature. Although AES-256, a symmetric encryption standard, is currently considered resistant to quantum decryption, it only protects data after a secure connection is established through a process that today relies on RSA or ECC. This is why governments and companies are racing to adopt Post- Quantum Cryptography (PQC) and quantum key distribution (QKD) to protect security and privacy in digital infrastructure.
2. Market Monopoly: Quantum computing demands significant investments in infrastructure, talent, and research, which only a handful of countries and companies currently possess. As a result, firms that develop early quantum advantage may gain unprecedented competitive leverage through offerings such as quantum-as-a-service, disrupting encryption-dependent industries, or accelerating innovation in pharmaceuticals, finance, and logistics. This could reinforce the existing power asymmetries in the global digital economy. Given these challenges, proactive and forward-looking policy frameworks are critical.
What Should Quantum Computing Policy Cover?
Commercial quantum computing will transform many industries. Policy will have to be flexible and be developed in iterations to account for fast-paced developments in the field. It will also require enduring international collaboration to effectively address a broad range of concerns, including ethics, security, privacy, competition, and workforce implications.
1. Cybersecurity and Encryption: Quantum policy should prioritise the development and standardisation of quantum-resistant encryption methods. This includes ongoing research into Post-Quantum Cryptography (PQC) algorithms and their integration into digital infrastructure. Global policy will need to align national efforts with international standards to create unified quantum-safe encryption protocols.
2. Market Competition and Access: Given the high barriers to entry, regulatory frameworks should promote fair competition, enabling smaller players like startups and developing economies to participate meaningfully in the quantum economy. Frameworks to ensure equitable access, interoperability, and fair competition will become imperative as the quantum ecosystem matures so that society can reap its benefits as a whole.
4. Ethical Considerations: Policymakers will have to consider the impact on privacy and security, and push for the responsible use of quantum capabilities. This includes ensuring that quantum advances do not contribute to cybercrime, disproportionate surveillance, or human rights violations.
5. International Standard-Setting: Setting benchmarks, shared terminologies, and measurement standards will ensure interoperability and security across diverse stakeholders and facilitate global collaboration in quantum research and infrastructure.
6. Military and Defence Implications: Militarisation of quantum technologies is a growing concern, and national security affairs related to quantum espionage are being urgently explored. Nations will have to develop regulations to protect sensitive data and intellectual property from quantum-enabled attacks.
7. Workforce Development and Education: Policies should encourage quantum computing education at various levels to ensure a steady pipeline of talent and foster cross-disciplinary programs that blend quantum computing with fields like machine learning, AI, and engineering.
8. Environmental and Societal Impact: Quantum computing hardware requires specialised conditions such as extreme cooling. Policy will have to address the environmental footprint of the infrastructure and energy consumption of large-scale quantum systems. Broader societal impacts of quantum computing, including potential job displacement, accessibility issues, and the equitable distribution of quantum computing benefits, will have to be explored.
Conclusion
Like nuclear power and AI, the new wave of quantum technologies is expected to be an exciting paradigm shift for society. While they can bring numerous benefits to commercial operations and address societal challenges, they also pose significant risks to global information security. Quantum policy will require regulatory, strategic, and ethical frameworks to govern the rise of these technologies, especially as they intersect with national security, global competition, and privacy. Policymakers must act in collaboration to mitigate unethical use of these technologies and the entrenchment of digital divides across countries. The OECD’s Anticipatory Governance of Emerging Technologies provides a framework of essential values like respect for human rights, privacy, and sustainable development, which can be used to set a baseline, so that quantum computing and related technologies benefit society as a whole.
References
- https://www.weforum.org/stories/2024/07/explainer-what-is-quantum-technology/
- https://www.paconsulting.com/insights/what-is-quantum-technology
- https://delinea.com/blog/quantum-safe-encryption#:~:text=This%20can%20result%20in%20AES,%2D128%20to%20AES%2D256.
- https://www.oecd.org/en/publications/a-quantum-technologies-policy-primer_fd1153c3-en.html

A war in the twenty-first century does not start when the first bullet or missile is fired. It begins much earlier, covertly, and without any official announcement. Cyberspace is this new battlefield. States now use a variety of ransomware, malicious codes, and disinformation campaigns to undermine their enemies' capabilities before launching an offensive. These pre-conflict cyber operations are now the primary frontline of contemporary hybrid warfare, which is changing how conflicts are fought and conducted.
The Birth of a Digital Battlefield
Hybrid Warfare is a blend of conventional military force with nonmilitary tactics like economic coercion, disinformation, and cyberattacks that have evolved rapidly in recent decades. Hybrid methods of warfare are nothing new, as the scale and sophistication of cyber operations in modern conflicts are unprecedented. Russia’s actions in Ukraine demonstrated the capability of digital tools to paralyse the critical systems before its heavy munitions could be deployed for combat operations. Within days of the 2022 invasions, Ukraine faced massive Distributed Denial of Service (DDoS) attacks targeting banks, government websites, and energy infrastructures. The digital frontlines have softened the physical defences long before the conventional warfare began.
According to the FP Analytics’ “Digital Front Lines” Project, cyber operations are no longer an auxiliary tactic but a core component of hybrid warfare, blurring the boundary between peace and war. They enable states to exert pressure, gather intelligence, and disrupt adversaries, often without being attributed or held accountable.
Cyber Operations: The modern Prelude to War
The use of digital technologies for surveillance, information network disruption, or critical infrastructure destruction is known as cyber operations. They are especially useful instruments for pre-conflict manipulation because of their ambiguity and stealth. Cyberattacks, in contrast to conventional military strikes, can accomplish strategic goals while providing plausible deniability.
Coordinated cyberattacks that spread misinformation and damaged public confidence disrupted government communication systems prior to Russia's invasion of Ukraine. These sorts of incidents highlight the integrated nature of cyber and kinetic operations, where digital assaults often serve as the initial phases of modern wars.
The Expanding Spectrum of Actors or Threat
Cyberspace has democratized warfare, which once required an army, can now be initiated by a handful of skilled programmers with access to the right tools. The cyber landscape of the present times features a wide spectrum of threat actors, which can be understood as;
- State actors like intelligence or military agencies conduct cyber operations as part of official foreign policy.
- Cybercriminals pursue financial gains, often overlapping with political motives.
- Terrorist groups use cyberspace to spread propaganda for coordinated attacks.
- Cyber mercenaries being hired by both the state and nonstate clients can blur the ethical and legal boundaries.
This diversity can complicate the attribution by determining that anyone who is actively working behind conducting cyberattacks can be notoriously difficult, allowing the states to hide behind “plausible deniability.” This ‘Gray Zone’ of conflict below the threshold of a declared war, above mere diplomacy, has become the preferred arena for modern power struggles.
Civilian Involvement and Ethical Dilemmas
Unlike traditional warfare, where the cyber domain entangles civilians as both participants and targets. Much of the nation’s critical infrastructure, which includes energy grids, hospitals, transportation, and communication systems, is owned and operated by private entities. As a result, the civilian industries and experts are becoming central to both cyber defence and offence.
During the Russia–Ukraine War, the volunteer hackers from around the world were many of whom are being coordinated through the app Telegram, which is termed as ‘IT Army of Ukraine’, are known for conducting digital strikes on Russian networks. Conversely, the Russia-affiliated hacker groups like Conti had vowed to retaliate against any nations that supported Ukraine.
This civilian participation raises profound legal and moral questions, over a private company’s role in defending their networks of becoming a combatant, or the impact of retaliatory cyberattacks on civilian infrastructure war crimes. International law has yet to provide a clear answer, which can leave dangerous gaps in the governance to counter cybercrimes.
Susceptibility of Contemporary Society to Cyber Warfare
Cyberwarfare can impact an entire global digital ecosystem due to its interconnectedness. Power grids, hospitals, air traffic systems, and even automation devices can be compromised. While the NotPetya ransomware, which was cloaked as ransomware, caused billions of losses and caused worldwide economic damage from shipping companies to pharmaceutical companies, the WannaCry ransomware attacks in 2017 paralysed hospitals throughout the UK's National Health Service.
When taken as a whole, these incidents have also shown that cyberattacks are no longer limited to espionage situations and can have real-world consequences comparable to those of conventional warfare. The consequences of cyberattacks could increase dramatically as our dependence on technology increases. Because these effects are profoundly psychological in nature and seek to sow fear, mistrust, and social disintegration, they are not merely technical or economic in nature.
The Future: Permanent Cyber Frontlines
Technological developments have made cyberspace a permanent theatre of conflict, joining the land, sea, air, and space. Countries are currently making significant investments in cyber capabilities for deterrence as well as defence. According to security experts like Eriksson and Giacomello, societies are now inherently fragile due to our increasing reliance on information technologies.
Cyber operations in this context are about strategic dominance in a globalised world, not just digital espionage. Who controls the networks and algorithms that run contemporary civilisation will determine the future of war, not just who controls the skies or the seas. As per the new reality, before the drop of the first bomb, a silent war in cyberspace will already be underway.
References
- https://digitalfrontlines.io/2023/05/25/the-evolution-of-cyber-operations-in-armed-conflict/
- https://theses.ubn.ru.nl/server/api/core/bitstreams/9d74149e-fb9a-402f-aa65-a90445ad7603/content
- https://cybersecurityguide.org/resources/cyberwarfare/
- https://re.public.polimi.it/retrieve/e0c31c0b-ce6c-4599-e053-1705fe0aef77/21%20Century%20Cyber%20Warfare.pdf

The more ease and dependency the internet slithers into our lives, the more obscure parasites linger on with it, menacing our privacy and data. Among these digital parasites, cyber espionage, hacking, and ransom have never failed to grab the headlines. These hostilities carried out by cyber criminals, corporate juggernauts and several state and non-state actors lend them unlimited access to the customers’ data damaging the digital fabric and wellbeing of netizens.
As technology continues to evolve, so does the need for robust safety measures. To tackle these emerging challenges, Korea based Samsung Electronics has introduced a cutting-edge security tool called Auto Blocker. Introduced in the One UI 6 Update, Auto Blocker boasts an array of additional security features, granting users the ability to customize their device's security as per their requirements Also known as ‘advanced sandbox’ or ‘Virtual Quarantine’. Sandboxing is a safety measure for separating running programs to prevent spread of digital vulnerabilities. It prohibits automatic execution of malicious code embedded in images. This shield now extends to third-party apps like WhatsApp and Facebook messenger, providing better resilience against cyber-attacks in all Samsung devices.
Matter of Choice
Dr. Seungwon Shin, EVP & Head of Security Team, Mobile eXperience Business at Samsung Electronics, emphasizes the significance of user safety. He stated “At Samsung, we constantly strive to keep our users safe from security attacks, and with the introduction of Auto Blocker, users can continue to enjoy the benefits of our open ecosystem, knowing that their mobile experience is secured.”
Auto Blocker is a matter of choice. It's not a cookie cutter solution; instead, its USP is the ability to customize security measures of your device. The Auto Blocker can be accessed through device’s setting, and is activated via toggle.
Your personal Digital Armor
One of Auto Blocker's salient features is its ability to prevent bloatware (unnecessary apps) from installing in the devices from unknown sources which is called sideloading. While sideloading provides greater scope of control and better customization, it also exposes users to potential threats, such as malicious file downloads. The proactive approach of Auto Blocker disables sideloading by default. Auto Blocker serves as an extra line of defense, especially against gruesome social engineering attacks such as voice Phishing (Vhishing). The app has an essential tool called ‘Message Guard’, engineered to combat Zero Click attacks. These complicated attacks are executed when a message containing an image is viewed.
The Auto Blocker also offers a wide variety of new controls to enhance device’s safety, including security scans to detect malwares. Additionally, Auto Blocker prevents the installation of malwares via USB cable. This ensures the device's security even when someone gains physical access to it, such as when the device is being charged in a public place.
Raising the Bar for Cyber Security
Auto Blocker testifies Samsung's unwavering commitment to the safety and privacy of its users. It acts an essential part of Samsung's security suite and privacy innovations, improving overall mobile experience within the Galaxy’s ecosystem. It provides a safer mobile experience while allowing user superior control over their device's protection. In comparison. Apple offers a more standardized approach to privacy and security with emphasis on user friendly design and closed ecosystem. Samsung disables sideloading to combat threats, while Apple is more flexible in this regard on macOS.
In this dynamic digital space, the Auto Blocker offers a tool to maintain cyber peace and resilience. It protects from a broad spectrum of digital hostilities while allowing us to embrace the new digital ecosystem crafted by Galaxy. It's a security feature that puts you in control, allowing you to determine how you fortify your digital fort to safeguard your device against digital specters like zero clicks, voice phishing (Vishing) and malware downloads
Samsung’s new product emerges as impenetrable armor shielding users against cyber hostilities. With its new customizable security feature with Galaxy Ecosystem, it allows users to exercise greater control over their digital space, promoting more secure and peaceful cyberspace.
Reference:
HT News Desk. (2023, November 1). Samsung unveils new Auto Blocker feature to protect devices. How does it work? Hindustan Times. https://www.hindustantimes.com/technology/samsung-unveils-new auto-blocker-feature to-protect-devices-how-does-it-work 101698805574773.html


