#FactCheck: AI Generated audio of CDS admitting that Pakistan Army is superior than Indian Army.
Executive Summary:
A viral social media claim alleges that India’s Chief of Defence Staff (CDS), General Anil Chauhan, praised Pakistan’s Army as superior during “Operation Sindoor.” Fact-checking confirms the claim is false. The original video, available on The Hindu’s official channel, shows General Chauhan inaugurating Ran-Samwad 2025 in Mhow, Madhya Pradesh. At the 1:22:12 mark, the genuine segment appears, proving the viral clip was altered. Additionally, analysis using Hiya AI Audio identified voice manipulation, flagging the segment as a deepfake with an authenticity score of 1/100. The fabricated statement was: “never mess with Pakistan because their army appears to be far more superior.” Thus, the viral video is doctored and misleading.
Claim:
A viral claim is being shared on social media (archived link) falsely claiming that India’s Chief of Defence Staff (CDS), General Anil Chauhan described Pakistan’s Army as superior and more advanced during Operation Sindoor.

Fact Check:
After performing a reverse image search we found a full clip on the official channel of The Hindu in which Chief of Defence Staff Anil Chauhan inaugurated ‘Ran-Samwad’ 2025 in Mhow, Madhya Pradesh.

In the clip on the time stamp of 1:22:12 we can see the actual part of the video segment which was manipulated in the viral video.
Also, by using Hiya AI Audio tool we got to know that the voice was manipulated in the specific segment of the video. The result shows Deepfake with an authenticity score 1/100, the result also shows the statement which is deepfake which was “ was to never mess with Pakistan because their army appears to be far more superior”.
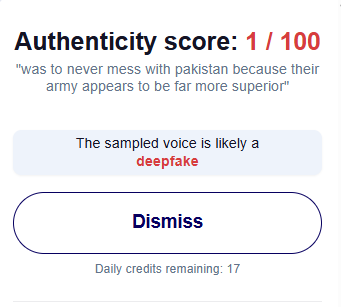
Conclusion:
The viral video attributing remarks to CDS General Anil Chauhan about Pakistan’s Army being “superior” is fabricated. The original footage from The Hindu confirms no such statement was made, while forensic analysis using Hiya AI Audio detected clear voice manipulation, identifying the clip as a deepfake with minimal authenticity. Hence, the claim is baseless, misleading, and an attempt to spread disinformation.
- Claim: AI Generated audio of CDS admitting that the Pakistan Army is superior to the Indian Army.
- Claimed On: Social Media
- Fact Check: False and Misleading
Related Blogs

Introduction
The world has been surfing the wave of technological advancements and innovations for the past decade, and it all pins down to one device – our mobile phone. For all mobile users, the primary choices of operating systems are Android and iOS. Android is an OS created by google in 2008 and is supported by most brands like – One+, Mi, OPPO, VIVO, Motorola, and many more and is one of the most used operating systems. iOS is an OS that was developed by Apple and was introduced in their first phone – The iPhone, in 2007. Both OS came into existence when mobile phone penetration was slow globally, and so the scope of expansion and advancements was always in favor of such operating systems.
The Evolution
iOS
Ever since the advent of the iPhone, iOS has seen many changes since 2007. The current version of iOs is iOS 16. However, in the course of creating new iOS and updating the old ones, Apple has come out with various advancements like the App Store, Touch ID & Face ID, Apple Music, Podcasts, Augmented reality, Contact exposure, and many more, which have later become part of features of Android phone as well. Apple is one of the oldest tech and gadget developers in the world, most of the devices manufactured by Apple have received global recognition, and hence Apple enjoys providing services to a huge global user base.
Android
The OS has been famous for using the software version names on the food items like – Pie, Oreo, Nougat, KitKat, Eclairs, etc. From Android 10 onwards, the new versions were demoted by number. The most recent Android OS is Android 13; this OS is known for its practicality and flexibility. In 2012 Android became the most popular operating system for mobile devices, surpassing Apple’s iOS, and as of 2020, about 75 percent of mobile devices run Android.
Android vs. iOS
1. USER INTERFACE
One of the most noticeable differences between Android and iPhone is their user interface. Android devices have a more customizable interface, with options to change the home screen, app icons, and overall theme. The iPhone, on the other hand, has a more uniform interface with less room for customization. Android allows users to customize their home screen by adding widgets and changing the layout of their app icons. This can be useful for people who want quick access to certain functions or information on their home screen. IOS does not have this feature, but it does allow users to organize their app icons into folders for easier navigation.
2. APP SELECTION
Another factor to consider when choosing between Android and iOS is the app selection. Both platforms have a wide range of apps available, but there are some differences to consider. Android has a larger selection of apps overall, including a larger selection of free apps. However, some popular apps, such as certain music streaming apps and games, may be released first or only available on iPhone. iOS also has a more curated app store, meaning that all apps must go through a review process before being accepted for download. This can result in a higher quality of apps overall, but it can also mean that it takes longer for new apps to become available on the platform. iPhone devices tend to have less processing power and RAM. But they are generally more efficient in their use of resources. This can result in longer battery life, but it may also mean that iPhones are slower at handling multiple tasks or running resource-intensive apps.
3. PERFORMANCE
When it comes to performance, both Android and iPhone have their own strengths and weaknesses. Android devices tend to have more processing power and RAM. This can make them faster and more capable of handling multiple tasks simultaneously. However, this can also lead to Android devices having shorter battery life compared to iPhones.
4. SECURITY
Security is an important consideration for any smartphone user, and Android and iPhone have their own measures to protect user data. Android devices are generally seen as being less secure than iPhones due to their open nature. Android allows users to install apps from sources other than the Google Play Store, which can increase the risk of downloading malicious apps. However, Android has made improvements in recent years to address this issue. Including the introduction of Google Play Protect, which scans apps for malware before they are downloaded. On the other hand, iPhone devices have a more closed ecosystem, with all apps required to go through Apple‘s review process before being available for download. This helps reduce the risk of downloading malicious apps, but it can also limit the platform’s flexibility.
Conclusion
The debate about the better OS has been going on for some time now, and it looks like it will get more comprehensive in the times to come, as netizens go deeper into cyberspace, they will get more aware and critical of their uses and demands, which will allow them to opt for the best OS for their convenience. Although the Andriod OS, due to its integration, stands more vulnerable to security threats as compared to iOS, no software is secure in today’s time, what is secure is its use and application hence the netizen and the platforms need to increase their awareness and knowledge to safeguard themselves and the wholesome cyberspace.

As e-commerce companies expand their base and sell a wide range of products on their platforms, attackers continue to look for newer avenues to exploit and potential loopholes to perpetuate scams. A recent method used by scammers is the brushing scam, which targets online shoppers to drive sales. As per reports, it is already being conducted on popular and trusted e-commerce websites such as Amazon and Alibaba Express, and online shoppers must exercise caution with regard to the packages they receive.
The Brushing Scam
Deriving its name from China’s e-commerce practice, this scam includes sellers creating and sending fake orders to unsuspecting individuals, posing to be from e-commerce websites in order to ‘brush up’ the sales figures of their product. The products received are usually low quality and contain items such as low-cost jewellery, seeds, and random gadgets, among other things. The aim is to manipulate reviews for a particular product and make it seem popular so other buyers online are encouraged to purchase the items marketed. Most online shoppers today check reviews before making a purchase, and popular items and seemingly-trustworthy reviews can go a long way towards influencing customer behaviour. Since many platforms do include labels to authenticate reviews tied to genuine purchases to counter fake reviews, scammers have evolved a step further to develop an MO for fake reviews that holds up against basic levels of scrutiny. Some of the packages received under the brushing scam also have QR codes which once scanned lead the receiver to malicious websites.
CyberPeace Insights
Mysterious deliveries that have no information but your name and address may seem tempting to many, as receivers might assume that it could be a marketing gig and free products to try for the sake of promoting a product. The credibility of such deliveries increases as they are packaged to show that these are delivered through trusted online shopping and e-commerce sites. However, even though receiving products for free might seem harmless, it is advised that unknown items be dealt with carefully, more so when addressed to an individual with personal details. Receiving an order itself is an indication that personal information such as one’s name and address has been compromised, and it is likely that the sellers are involved in procuring personal information through a third party, often using illegal methods.
Registering complaints to the concerned e-commerce websites is encouraged, as the frequency of cases raises questions and encourages platforms to take action to ensure a secure buying and delivery experience from their end. An awareness of such scams being carried out for their customers could encourage caution on the part of these platforms and prove to be helpful in addressing the issue on multiple levels. On the part of the receivers, they can change the passwords of their e-commerce accounts and use a 2FA (2-factor authentication) for better security. They should also exercise caution while receiving such parcels, and avoid scanning QR codes on suspicious items.
References
- https://www.livemint.com/technology/tech-news/brushing-scam-explained-from-fake-orders-to-reviews-how-fraudsters-are-manipulating-online-shopping-platforms-11735824384866.html
- https://www.indiatvnews.com/technology/news/beware-of-amazon-scams-how-fraudsters-use-fake-reviews-to-sell-counterfeit-products-2025-01-02-969115
- https://www.indiatoday.in/technology/news/story/brushing-scam-now-makes-buzz-as-it-targets-online-shoppers-everything-you-need-to-know-2659172-2025-01-03
- https://www.msn.com/en-in/money/news/brushing-scam-now-makes-buzz-as-it-targets-online-shoppers-everything-you-need-to-know/ar-AA1wTvon
Introduction
The information of hundreds of thousands of Indians who received the COVID vaccine was Leaked in a significant data breach and posted on a Telegram channel. Numerous reports claim that sensitive information, including a person’s phone number, gender, ID card details, and date of birth, leaked over Telegram. It could be obtained by typing a person’s name into a Telegram bot.
What really happened?
The records pertaining to the mobile number registered in the CoWin portal are accessible on the Malayalam news website channel. It is also feasible to determine which vaccination was given and where it was given.
According to The Report, the list of individuals whose data was exposed includes BJP Tamil Nadu president K Annamalai, Congress MP Karti Chidambaram, and former BJP union minister for health Harsh Vardhan. Telangana’s minister of information and communication technology, Kalvakuntla Taraka Rama Rao, is also on the list.
MEITY stated in response to the data leak, “It is old data, we are still confirming it. We have requested a report on the matter.
After the media Report, the bot was disabled, but experts said the incident raised severe issues because the information might be used for identity theft, phishing emails, con games, and extortion calls. The Indian Computer Emergency Response Team (CERT-In), the government’s nodal body, has opened an investigation into the situation
The central government declared the data breach reports regarding the repository of beneficiaries against Covid to be “mischievous in nature” on Monday and claimed the ‘bot’ that purportedly accessed the confidential data was not directly accessing the CoWIN database.
According to the first complaint by CERT-In, the government’s cybersecurity division, the government claimed the bot might be displaying information from “previously stolen data.” Reports.
The health ministry refuted the claim, asserting that no bots could access the information without first verifying with a one-time password.
“It is made clear that all of these rumours are false and malicious. The health ministry’s CoWIN interface is entirely secure and has sufficient data privacy protections. The security of the data on the CoWIN portal is being ensured in every way possible, according to a statement from the health ministry.
Meity said the CoWin program or database was not directly compromised, and the shared information appeared to be taken from a previous intrusion. But the hack again highlights the growing danger of cyber assaults, particularly on official websites.

Recent cases of data leak
Dominos India 2021– Dominos India, a division of Jubilant FoodWorks, faced a cyberattack on May 22, 2021, which led to the disclosure of information from 180 million orders. The breach exposed order information, email addresses, phone numbers, and credit card information. Although Jubilant FoodWorks acknowledged a security breach, it refuted any illegal access to financial data.
Air India – A cyberattack that affected Air India in May 2021 exposed the personal information of about 4.5 million customers globally. Personal information recorded between August 26, 2011, and February 3, 2021, including names, dates of birth, contact information, passport information, ticket details, frequent flyer information from Star Alliance and Air India, and credit card information, were exposed in the breach.
Bigbasket – BigBasket, an online supermarket, had a data breach in November 2020, compromising the personal information of approximately 20 million consumers. Email IDs, password hashes, PINs, phone numbers, addresses, dates of birth, localities, and IP addresses were among the information released from an insecure database containing over 15 GB of customer data. BigBasket admitted to the incident and reported it to the Bengaluru Cyber Crime Department.
Unacademy – Unacademy, an online learning platform, experienced a data breach in May 2020, compromising the email addresses of approximately 11 million subscribers. While no sensitive information, such as financial data or passwords, was compromised, user data, including IDs, passwords, date joined, last login date, email IDs, names, and user credentials, was. The breach was detected when user accounts were uncovered for sale on the dark web.
2022 Card Data- Cybersecurity researchers from AI-driven Singapore-based CloudSEK found a threat actor offering a database of 1.2 million cards for free on a Dark Web forum for crimes on October 12, 2022. This came after a second problem involving 7.9 million cardholder records that were reported on the BidenCash website. This comprised information pertaining to State Bank of India (SBI) clients. And other well-known companies were among those targeted in high-profile data breach cases that have surfaced in recent years.

Conclusion
Data breach cases are increasing daily, and attackers are mainly attacking the healthcare sectors and health details as they can easily find personal details. This recent CoWIN case has compromised thousands of people’s data. The All-India Institute of Medical Sciences’ systems were compromised by hackers a few months ago. Over 95% of adults have had their vaccinations, according to the most recent data, even if the precise number of persons impacted by the CoWin privacy breach could not be determined.


