#FactCheck - Viral Graphic Falsely Attributes Statement on UGC to CM Yogi Adityanath
Executive Summary
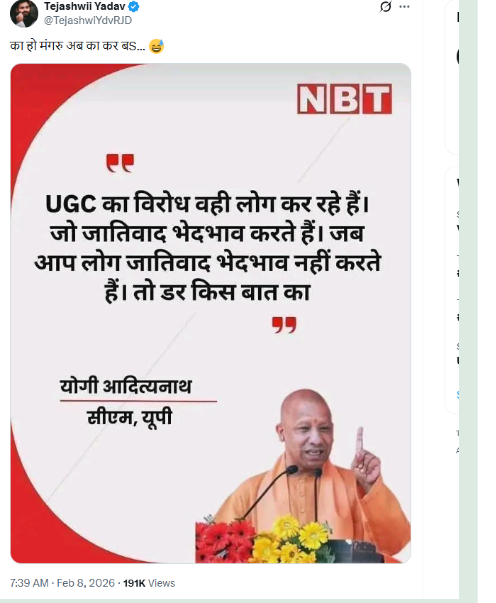
A news graphic is being shared on social media claiming that Uttar Pradesh Chief Minister Yogi Adityanath said,“Those who practice casteism and discrimination are the ones opposing UGC. If you do not indulge in caste-based discrimination, what is there to fear?” The CyberPeace’s research found the viral claim circulating on social media to be false. Our research revealed that Chief Minister Yogi Adityanath never made such a statement. It was also established that the viral news graphic has been digitally edited.
Claim
On February 8, a user on social media platform X (formerly Twitter) shared a news graphic bearing the logo of Navbharat Times, attributing the above statement to CM Yogi Adityanath. The post and its archived version can be seen below, along with screenshots. (Links and screenshots provided)
Fact Check:
To verify the authenticity of the claim, we conducted a keyword-based search on Google. However, we did not find any credible or reliable media report supporting the viral statement. We further examined the official social media accounts of Chief Minister Yogi Adityanath, including his Facebook and Instagram handles. Our review found no post, speech, or statement resembling the claim made in the viral graphic.
Continuing the research , we examined the official social media accounts of Navbharat Times. During this process, we found the original graphic published on the Navbharat Times Facebook page on January 26, 2026. The caption of the original graphic read: “On the occasion of Republic Day 2026, Uttar Pradesh Chief Minister Yogi Adityanath said, ‘No one is above the Constitution.’”
This clearly differs from the claim made in the viral graphic, indicating that the latter was altered.

Conclusion
Our research confirms that Uttar Pradesh Chief Minister Yogi Adityanath did not make the statement being attributed to him on social media. The viral news graphic is digitally edited and misleading. The claim, therefore, is false.
Related Blogs

Executive Summary:
A viral social media video falsely claims that Meta AI reads all WhatsApp group and individual chats by default, and that enabling “Advanced Chat Privacy” can stop this. On performing reverse image search we found a blog post of WhatsApp which was posted in the month of April 2025 which claims that all personal and group chats remain protected with end to end (E2E) encryption, accessible only to the sender and recipient. Meta AI can interact only with messages explicitly sent to it or tagged with @MetaAI. The “Advanced Chat Privacy” feature is designed to prevent external sharing of chats, not to restrict Meta AI access. Therefore, the viral claim is misleading and factually incorrect, aimed at creating unnecessary fear among users.
Claim:
A viral social media video [archived link] alleges that Meta AI is actively accessing private conversations on WhatsApp, including both group and individual chats, due to the current default settings. The video further claims that users can safeguard their privacy by enabling the “Advanced Chat Privacy” feature, which purportedly prevents such access.

Fact Check:
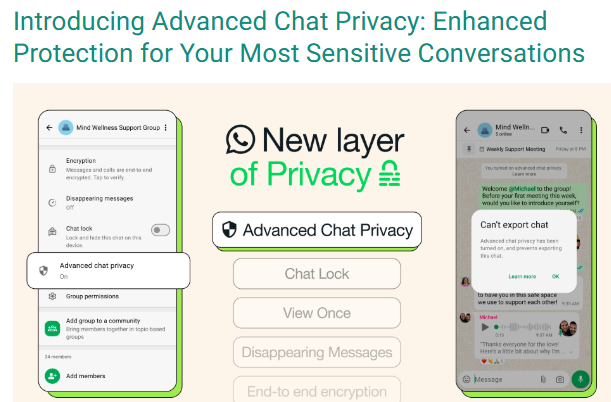
Upon doing reverse image search from the keyframe of the viral video, we found a WhatsApp blog post from April 2025 that explains new privacy features to help users control their chats and data. It states that Meta AI can only see messages directly sent to it or tagged with @Meta AI. All personal and group chats are secured with end-to-end encryption, so only the sender and receiver can read them. The "Advanced Chat Privacy" setting helps stop chats from being shared outside WhatsApp, like blocking exports or auto-downloads, but it doesn’t affect Meta AI since it’s already blocked from reading chats. This shows the viral claim is false and meant to confuse people.
Conclusion:
The claim that Meta AI is reading WhatsApp Group Chats and that enabling the "Advance Chat Privacy" setting can prevent this is false and misleading. WhatsApp has officially confirmed that Meta AI only accesses messages explicitly shared with it, and all chats remain protected by end-to-end encryption, ensuring privacy. The "Advanced Chat Privacy" setting does not relate to Meta AI access, as it is already restricted by default.
- Claim: Viral social media video claims that WhatsApp Group Chats are being read by Meta AI due to current settings, and enabling the "Advance Chat Privacy" setting can prevent this.
- Claimed On: Social Media
- Fact Check: False and Misleading
Introduction
The information of hundreds of thousands of Indians who received the COVID vaccine was Leaked in a significant data breach and posted on a Telegram channel. Numerous reports claim that sensitive information, including a person’s phone number, gender, ID card details, and date of birth, leaked over Telegram. It could be obtained by typing a person’s name into a Telegram bot.
What really happened?
The records pertaining to the mobile number registered in the CoWin portal are accessible on the Malayalam news website channel. It is also feasible to determine which vaccination was given and where it was given.
According to The Report, the list of individuals whose data was exposed includes BJP Tamil Nadu president K Annamalai, Congress MP Karti Chidambaram, and former BJP union minister for health Harsh Vardhan. Telangana’s minister of information and communication technology, Kalvakuntla Taraka Rama Rao, is also on the list.
MEITY stated in response to the data leak, “It is old data, we are still confirming it. We have requested a report on the matter.
After the media Report, the bot was disabled, but experts said the incident raised severe issues because the information might be used for identity theft, phishing emails, con games, and extortion calls. The Indian Computer Emergency Response Team (CERT-In), the government’s nodal body, has opened an investigation into the situation
The central government declared the data breach reports regarding the repository of beneficiaries against Covid to be “mischievous in nature” on Monday and claimed the ‘bot’ that purportedly accessed the confidential data was not directly accessing the CoWIN database.
According to the first complaint by CERT-In, the government’s cybersecurity division, the government claimed the bot might be displaying information from “previously stolen data.” Reports.
The health ministry refuted the claim, asserting that no bots could access the information without first verifying with a one-time password.
“It is made clear that all of these rumours are false and malicious. The health ministry’s CoWIN interface is entirely secure and has sufficient data privacy protections. The security of the data on the CoWIN portal is being ensured in every way possible, according to a statement from the health ministry.
Meity said the CoWin program or database was not directly compromised, and the shared information appeared to be taken from a previous intrusion. But the hack again highlights the growing danger of cyber assaults, particularly on official websites.

Recent cases of data leak
Dominos India 2021– Dominos India, a division of Jubilant FoodWorks, faced a cyberattack on May 22, 2021, which led to the disclosure of information from 180 million orders. The breach exposed order information, email addresses, phone numbers, and credit card information. Although Jubilant FoodWorks acknowledged a security breach, it refuted any illegal access to financial data.
Air India – A cyberattack that affected Air India in May 2021 exposed the personal information of about 4.5 million customers globally. Personal information recorded between August 26, 2011, and February 3, 2021, including names, dates of birth, contact information, passport information, ticket details, frequent flyer information from Star Alliance and Air India, and credit card information, were exposed in the breach.
Bigbasket – BigBasket, an online supermarket, had a data breach in November 2020, compromising the personal information of approximately 20 million consumers. Email IDs, password hashes, PINs, phone numbers, addresses, dates of birth, localities, and IP addresses were among the information released from an insecure database containing over 15 GB of customer data. BigBasket admitted to the incident and reported it to the Bengaluru Cyber Crime Department.
Unacademy – Unacademy, an online learning platform, experienced a data breach in May 2020, compromising the email addresses of approximately 11 million subscribers. While no sensitive information, such as financial data or passwords, was compromised, user data, including IDs, passwords, date joined, last login date, email IDs, names, and user credentials, was. The breach was detected when user accounts were uncovered for sale on the dark web.
2022 Card Data- Cybersecurity researchers from AI-driven Singapore-based CloudSEK found a threat actor offering a database of 1.2 million cards for free on a Dark Web forum for crimes on October 12, 2022. This came after a second problem involving 7.9 million cardholder records that were reported on the BidenCash website. This comprised information pertaining to State Bank of India (SBI) clients. And other well-known companies were among those targeted in high-profile data breach cases that have surfaced in recent years.

Conclusion
Data breach cases are increasing daily, and attackers are mainly attacking the healthcare sectors and health details as they can easily find personal details. This recent CoWIN case has compromised thousands of people’s data. The All-India Institute of Medical Sciences’ systems were compromised by hackers a few months ago. Over 95% of adults have had their vaccinations, according to the most recent data, even if the precise number of persons impacted by the CoWin privacy breach could not be determined.

Introduction
The Ministry of Electronics and Information Technology recently released the IT Intermediary Guidelines 2023 Amendment for social media and online gaming. The notification is crucial when the Digital India Bill’s drafting is underway. There is no denying that this bill, part of a series of bills focused on amendments and adding new provisions, will significantly improve the dynamics of Cyberspace in India in terms of reporting, grievance redressal, accountability and protection of digital rights and duties.
What is the Amendment?
The amendment comes as a key feature of cyberspace as the bill introduces fact-checking, a crucial aspect of relating information on various platforms prevailing in cyberspace. Misformation and disinformation were seen rising significantly during the Covid-19 pandemic, and fact-checking was more important than ever. This has been taken into consideration by the policymakers and hence has been incorporated as part of the Intermediary guidelines. The key features of the guidelines are as follows –
- The phrase “online game,” which is now defined as “a game that is offered on the Internet and is accessible by a user through a computer resource or an intermediary,” has been added.
- A clause has been added that emphasises that if an online game poses a risk of harm to the user, intermediaries and complaint-handling systems must advise the user not to host, display, upload, modify, publish, transmit, store, update, or share any data related to that risky online game.
- A proviso to Rule 3(1)(f) has been added, which states that if an online gaming intermediary has provided users access to any legal online real money game, it must promptly notify its users of the change, within 24 hours.
- Sub-rules have been added to Rule 4 that focus on any legal online real money game and require large social media intermediaries to exercise further due diligence. In certain situations, online gaming intermediaries:
- Are required to display a demonstrable and obvious mark of verification of such online game by an online gaming self-regulatory organisation on such permitted online real money game
- Will not offer to finance themselves or allow financing to be provided by a third party.
- Verification of real money online gaming has been added to Rule 4-A.
- The Ministry may name as many self-regulatory organisations for online gaming as it deems necessary for confirming an online real-money game.
- Each online gaming self-regulatory body will prominently publish on its website/mobile application the procedure for filing complaints and the appropriate contact information.
- After reviewing an application, the self-regulatory authority may declare a real money online game to be a legal game if it is satisfied that:
- There is no wagering on the outcome of the game.
- Complies with the regulations governing the legal age at which a person can engage into a contract.
- The Information Technology (Intermediary Guidelines and Digital Media Ethics Code) Rules, 2021 have a new rule 4-B (Applicability of certain obligations after an initial period) that states that the obligations of the rule under rules 3 and 4 will only apply to online games after a three-month period has passed.
- According to Rule 4-C (Obligations in Relation to Online Games Other Than Online Real Money Games), the Central Government may direct the intermediary to make necessary modifications without affecting the main idea if it deems it necessary in the interest of India’s sovereignty and integrity, the security of the State, or friendship with foreign States.
- Intermediaries, such as social media companies or internet service providers, will have to take action against such content identified by this unit or risk losing their “safe harbour” protections under Section 79 of the IT Act, which let intermediaries escape liability for what third parties post on their websites. This is problematic and unacceptable. Additionally, these notified revisions can circumvent the takedown order process described in Section 69A of the IT Act, 2000. They also violated the ruling in Shreya Singhal v. Union of India (2015), which established precise rules for content banning.
- The government cannot decide if any material is “fake” or “false” without a right of appeal or the ability for judicial monitoring since the power to do so could be abused to thwart examination or investigation by media groups. Government takedown orders have been issued for critical remarks or opinions posted on social media sites; most of the platforms have to abide by them, and just a few, like Twitter, have challenged them in court.
Conclusion
The new rules briefly cover the aspects of fact-checking, content takedown by Govt, and the relevance and scope of sections 69A and 79 of the Information Technology Act, 2000. Hence, it is pertinent that the intermediaries maintain compliance with rules to ensure that the regulations are sustainable and efficient for the future. Despite these rules, the responsibility of the netizens cannot be neglected, and hence active civic participation coupled with such efficient regulations will go a long way in safeguarding the Indian cyber ecosystem.


