#FactCheck - Deepfake Video Falsely Links Shah Rukh Khan to Rajpal Yadav Case
Executive Summary
A video featuring popular comedian Rajpal Yadav has recently gone viral on social media, claiming that he is currently lodged in Tihar Jail in connection with a loan default and cheque bounce case. In connection with this, another video showing Bollywood superstar Shah Rukh Khan is being widely shared online. In the viral clip, Khan is purportedly seen saying that he would help Rajpal Yadav get out of jail and also offer him a role in his upcoming film. However, research by the CyberPeace found the viral video to be fake. The clip is a deepfake, in which the audio has been manipulated using artificial intelligence. In the original video, Shah Rukh Khan is speaking about his life and personal experiences. Although several prominent Bollywood personalities have expressed support for Rajpal Yadav, the claims made in the viral video are misleading.
Claim
An Instagram user named “ayubeditz” shared the viral video on February 11, 2026, with the caption: “Rajpal Yadav bhai, stay strong, we are all with you — Shah Rukh Khan.” The link to the post and its archived version are provided below.
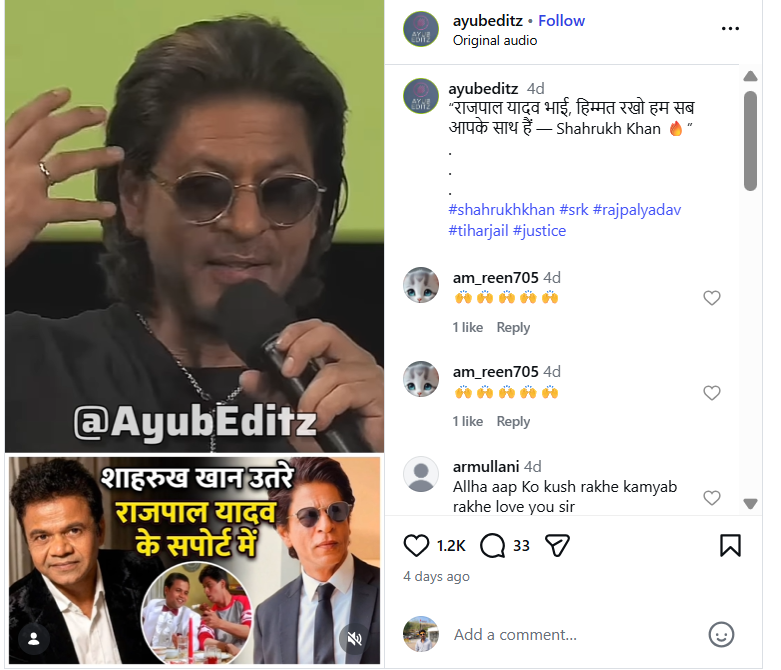
Fact Check
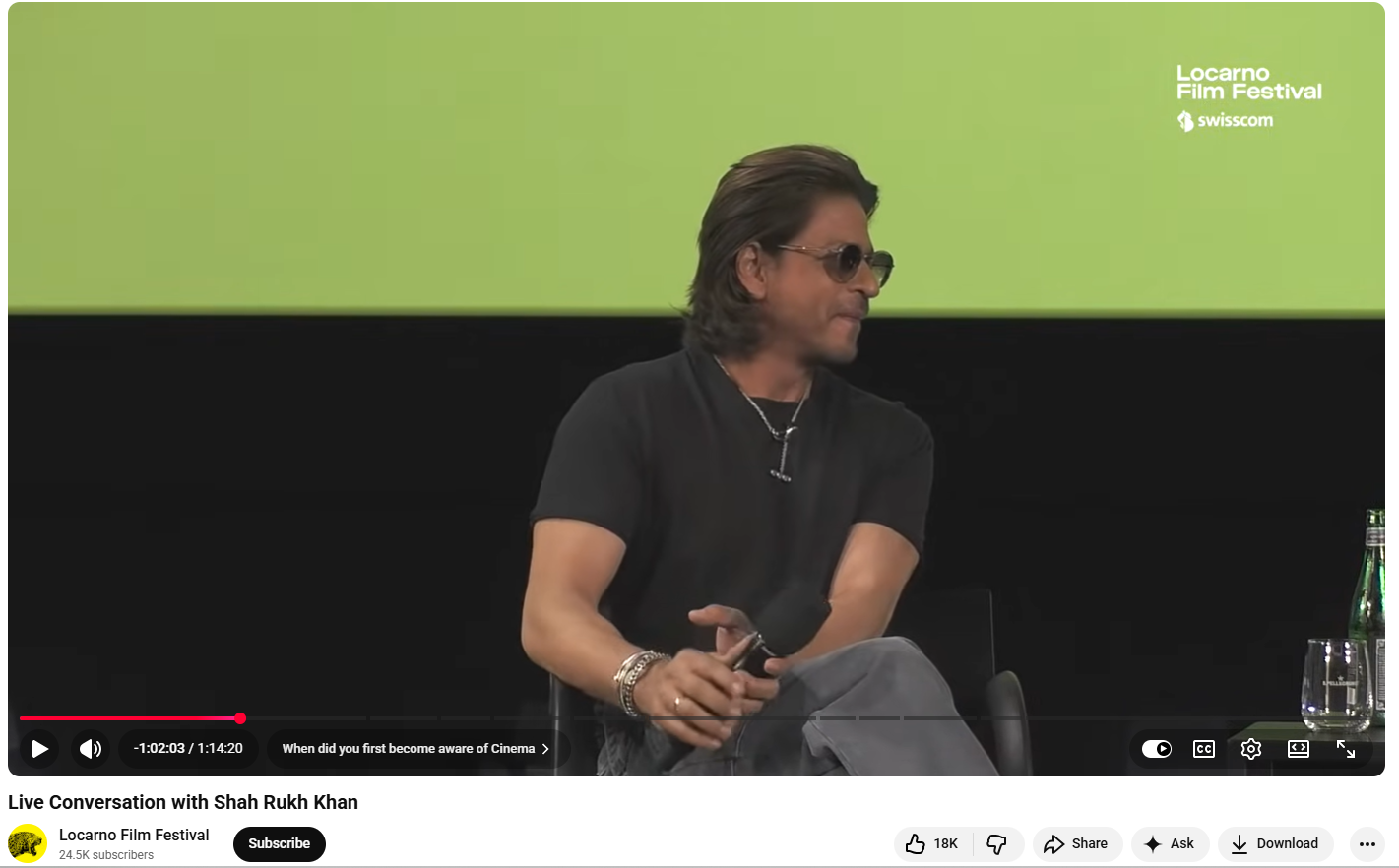
To verify the claim, we extracted key frames from the viral video and conducted a Google reverse image search. This led us to the original video uploaded on a YouTube channel titled “Locarno Film Festival” on August 11, 2024. According to the available information, Shah Rukh Khan was sharing insights about his life and career during a conversation with the festival’s Artistic Director, Giona A. Nazzaro. This raised strong suspicion that the viral video had been edited using AI.
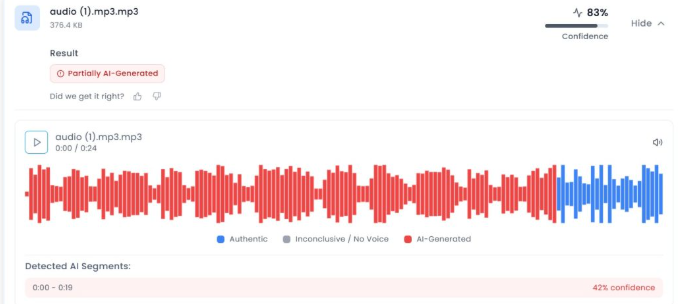
To further examine the authenticity of the audio, we analysed it using AI detection tools. The audio was first checked using Aurigin.ai, which indicated an 83 percent probability that the voice in the viral clip was AI-generated.
Conclusion
The CyberPeace’s research confirmed that the claim associated with Shah Rukh Khan’s viral video is false. The video is a deepfake in which the audio has been altered using artificial intelligence. In the original footage, Khan was discussing his life and experiences, and he did not make any statement about helping Rajpal Yadav.
Related Blogs

Introduction
The world has been riding the wave of technological advancements, and the fruits it has born have impacted our lives. Technology, by its virtue, cannot be quantified as safe or unsafe it is the application and use of technology which creates the threats. Its times like this, the importance and significance of policy framework are seen in cyberspace. Any technology can be governed by means of policies and laws only. In this blog, we explore the issues raised by the EU for the tech giants and why the Indian Govt is looking into probing Whatsapp.
EU on Big Techs
Eu has always been seen to be a strong policy maker for cyberspace, and the same can be seen from the scope, extent and compliance of GDPR. This data protection bill is the holy grail for worldwide data protection bills. Apart from the GDPR, the EU has always maintained strong compliance demographics for the big tech as most of them have originated outside of Europe, and the rights of EU citizens come into priority above anything else.
New Draft Notification
According to the draft of the new notification, Amazon, Google, Microsoft and other non-European Union cloud service providers looking to secure an EU cybersecurity label to handle sensitive data can only do so via a joint venture with an EU-based company. The document adds that the cloud service must be operated and maintained from the EU, all customer data must be stored and processed in the EU, and EU laws take precedence over non-EU laws regarding the cloud service provider. Certified cloud services are operated only by companies based in the EU, with no entity from outside the EU having effective control over the CSP (cloud service provider) to mitigate the risk of non-EU interfering powers undermining EU regulations, norms and values.
This move from the EU is still in the draft phase however, it is expected to come into action soon as issues related to data breaches of EU citizens have been reported on numerous occasions. The document said the tougher rules would apply to personal and non-personal data of particular sensitivity where a breach may have a negative impact on public order, public safety, human life or health, or the protection of intellectual property.
How will it secure the netizens?
Since the EU has been the leading policy maker in cyberspace, it is often seen that the rules and policies of the EU are often replicated around the world. Hence this move comes at a critical time as the EU is looking towards safeguarding the EU netizens and the Cyber security industry in the EU by allowing them to collaborate with big tech while maintaining compliance. Cloud services can be protected by this mechanism, thus ensuring fewer instances of data breaches, thus contributing to a dip in cyber crimes and attacks.
The Indian Govt on WhatsApp
The Indian Govt has decided to probe Whatsapp and its privacy settings. One of the Indian Whatsapp users tweeted a screenshot of WhatsApp accessing the phone’s mic even when the phone was not in use, and the app was not open even in the background. The meta-owned Social messaging platform enjoys nearly 487 million users in India, making it their biggest market. The 2018 judgement on Whatsapp and its privacy issues was a landmark judgement, but the platform is in violation of the same.
The MoS, Ministry of Electronics and Information Technology, Rajeev Chandrashekhar, has already tweeted that the issue will be looked into and that they will be punished if the platform is seen violating the guidelines. The Digital Personal Data Protection Bill is yet to be tabled at the parliament. Still, despite the draft bill being public, big platforms must maintain the code of conduct to maintain compliance when the bill turns into an Act.
Threats for Indian Users
The Indian Whatsapp user contributes to the biggest user base un the world, and still, they are vulnerable to attacks on WhatsApp and now WhatsApp itself. The netizens are under the following potential threats –
- Data breaches
- Identity theft
- Phishing scams
- Unconsented data utilisation
- Violation of Right to Privacy
- Unauthorised flow of data outside India
- Selling of data to a third party without consent
The Indian netizen needs to stay vary of such issues and many more by practising basic cyber safety and security protocols and keeping a check on the permissions granted to apps, to keep track of one’s digital footprint.
Conclusion
Whether it’s the EU or Indian Government, it is pertinent to understand that the world powers are all working towards creating a safe and secured cyberspace for its netizens. The move made by the EU will act as a catalyst for change at a global level, as once the EU enforces the policy, the world will soon replicate it to safeguard their cyber interests, assets and netizens. The proactive stance of the Indian Government is a crucial sign that the things will not remain the same in the Indian Cyber ecosystem, and its upon the platforms and companies to ensure compliance, even in the absence of a strong legislation for cyberspace. The government is taking all steps to safeguard the Indian netizen, as the same lies in the souls and spirit of the new Digital India Bill, which will govern cyberspace in the near future. Still, till then, in order to maintain the synergy and equilibrium, it is pertinent for the platforms to be in compliance with the laws of natural justice.

Introduction
We are living in the digital age, where from ordering food to floating into a relationship everything is preferred to be digitized. It has been quite evident that in the past few years, online dating has become immensely popular due to its potential success stories. Since it has become a medium to find potential partners. Among the string of successes and pros of online dating, there seems to be a corner which is curtained that contains scams and treachery. A very recent case in Delhi puts light into the dark side of online dating where a 25-year-old journalist was trapped in an online dating scam. It portrays the threat of meeting an unknown person through an online dating app and how a person gets involved in the vicious cycle. Since the concept of online dating is all about meeting a new person and getting indulged. This incident talks about a man who met a woman through a dating app Bumble and got scammed for Rs 15000.
Unveiling the scam
It started like a fairy tale where a 25-year-old Delhi resident met with a girl on a dating app Bumble, where they spoke and found each other compatible. Followed by it the girl approaches the boy to meet at a specific restaurant situated in Delhi. The boy was away from the idea that the first meetup would turn into a nightmare which horrifying experience he would share on social media. It is not only about the financial loss but also about the emotional distress one goes through. Every coin has two sides and when surfing in the digital world one needs to keep in mind that along with the pros, there are certain cons. In the eagerness to meet someone, we should not lose our presence of mind. Continuing the incident once both reached the specified restaurant the girl made an order of various food items including beverages, shots of vodka, glasses of wine, different cuisines and hookah. Which not so surprisingly culminated in an inflated bill of Rs 15,886. After paying the hefty amount the boy went to the washroom once he came back the bill vanished followed by the girl being eager to leave the place. Till that very moment, the victim was in his dreamland where he did not get the hint that he had been scammed. Once he reached home and tried contacting the lady her account was deleted from the platform and was not reachable through calls. This incident shook the victim and pushed him to melancholy. Since he did not expect this to happen. Devastated by the fraud and treachery the man wrote about his disappointing experience on his Twitter handle addressing Delhi police to look into this.
It has been brought to the notice that similar incidents have been reported in the past as well. The trend remains the same in which the culprit insists the victim meet at a specific location decided by them, it is done with such conviction that it becomes difficult for the victim to deny. Once they accept to meet in the decided location it is followed by making the victim order expensive food and alcohol and at the time of payment giving excuses or pretending to pay. Once the payment is done the culprit rushes to leave the location or disappears without any head up. Not to be perplexed once they leave they will not leave any trace of them.
How to stay safe in the online dating world?
Online dating can bring butterflies in the stomach, and indeed it is a beautiful experience to meet someone new and fall in love but with this beauty, there comes the baggage of falling into the trap of cyber scams. While surfing online dating sites one needs to be very careful and vigilant since the highlighted incidents are relevant enough to showcase the negative impact on it.
Best practices
- Use reliable platforms: With the growing digitalization, there are infinite platforms available for online dating. But here is the catch one needs to be very finicky in choosing an appropriate platform among the countless options. It is best to use authentic platforms or apps and read reviews and ratings before installing any such applications or platforms.
- Cross-verify the profiles: Once you receive a profile compatible enough to talk about it is recommended to have elaborative conversations. It is not about doubting someone but being calculative and cross-checking all the information given. Before meeting the person it is best to have a detailed conversation but not reveal much about you.
- Have control in your pocket: When it comes to paying the bill be proactive in dividing the bill. It is advisable to do so that the liability of paying a hefty bill does not come from one party. This will make sure that even if one of the people has the intention to exploit the other person they will become alarmed.
- Go with the flow: Since meeting an unknown person is all flowery and spontaneous, it is also good to follow your instinct and go with the flow if you find anything weird during the conversation or while in person. It is advisable to back off or to leave the place as soon as possible.
- Be cautious in sharing your personal information with strangers: While conversing with an unknown person online, it is very important to keep a hold on our emotions and not share any personal information which can be misused by cyber crooks. Also, it is very important that we do not discuss anything about our financial capabilities and transactions. It is imperative to note that cyber crooks exploit the many new ways to commit online fraud by targeting innocent individuals.
- Catching up in public places: When meeting for the first time it is advisable to meet a person in a public place such as a park, museums etc. It is the best way to avoid going to a place decided or being insisted. Since meeting in a public place gives a sense of security that people are around you.
- Keep your near people in Loop: No matter how private you are while meeting an unknown person keep your friends and near one aware of it.
What to do if you fall into such dating scams
- While one can be emotionally drained, it is very important to keep track of all the information shared, save all your messages, take pictures of the scammer's profile and document every small detail which can be relevant.
- Report on the platform: There would be a section called “Contact us” or “Report” on the platform where you can report against the scammer. Most dating apps have this section where you can mention your issue so that they can take action against such profiles.
- National Cyber Crime Reporting Portal, 1930 Helpline: The Cybercrime reporting portal http://www.cybercrime.gov.in/ equipped with 24x7 helpline 1930 is a powerful resource available to the victims of cybercrimes to report their cases.
Conclusion
Online dating can become the gush of winds for someone but it is very important to keep in mind that with the potential of falling in love, there comes a threat of being trapped and getting into cyber frauds or scams. So many cases are being reported, and the recent case also highlights that not everyone on online sites is genuine. So be aware of such scams and stay informed and safe in the evolving digital environment.
References
- https://www.moneycontrol.com/news/trends/delhi-cafes-hiring-girls-to-scam-customers-says-bumble-user-conned-out-of-rs-15000-11724701.html
- https://www.ndtv.com/delhi-news/delhi-man-falls-victim-to-scam-as-bumble-date-costs-him-15-000-4566680/amp/1
- https://services.india.gov.in/service/detail/national-cyber-crime-reporting-portal#:~:text=This%20portal%20is%20an%20initiative,crimes%20against%20women%20and%20children.

Introduction
The unprecedented cyber espionage attempt on the Indian Air Force has shocked the military fraternity in the age of the internet where innovation is vital to national security. The attackers have shown a high degree of expertise in their techniques, using a variant of the infamous Go Stealer and current military acquisition pronouncements as a cover to obtain sensitive information belonging to the Indian Air Force. In this recent cyber espionage revelation, the Indian Air Force faces a sophisticated attack leveraging the infamous Go Stealer malware. The timing, coinciding with the Su-30 MKI fighter jets' procurement announcement, raises serious questions about possible national security espionage actions.
A sophisticated attack using the Go Stealer malware exploits defense procurement details, notably the approval of 12 Su-30 MKI fighter jets. Attackers employ a cunningly named ZIP file, "SU-30_Aircraft_Procurement," distributed through an anonymous platform, Oshi, taking advantage of heightened tension surrounding defense procurement.
Advanced Go Stealer Variant:
The malware, coded in Go language, introduces enhancements, including expanded browser targeting and a unique data exfiltration method using Slack, showcasing a higher level of sophistication.
Strategic Targeting of Indian Air Force Professionals:
The attack strategically focuses on extracting login credentials and cookies from specific browsers, revealing the threat actor's intent to gather precise and sensitive information.
Timing Raises Espionage Concerns:
The cyber attack coincides with the Indian Government's Su-30 MKI fighter jets procurement announcement, raising suspicions of targeted attacks or espionage activities.
The Deceitful ZIP ArchiveSU-30 Aircraft Acquisition
The cyberattack materialised as a sequence of painstakingly planned actions. Using the cleverly disguised ZIP file "SU-30_Aircraft_Procurement," the perpetrators took benefit of the authorisation of 12 Su-30 MKI fighter jets by the Indian Defense Ministry in September 2023. Distributed via the anonymous file storage network Oshi, the fraudulent file most certainly made its way around via spam emails or other forms of correspondence.
The Spread of Infection and Go Stealer Payload:
The infiltration procedure progressed through a ZIP file to an ISO file, then to a.lnk file, which finally resulted in the Go Stealer payload being released. This Go Stealer version, written in the programming language Go, adds sophisticated capabilities, such as a wider range of browsing focussed on and a cutting-edge technique for collecting information using the popular chat app Slack.
Superior Characteristics of the Go Stealer Version
Different from its GitHub equivalent, this Go Stealer version exhibits a higher degree of complexity. It creates a log file in the machine owned by the victim when it is executed and makes use of GoLang utilities like GoReSym for in-depth investigation. The malware focuses on cookies and usernames and passwords from web browsers, with a particular emphasis on Edge, Brave, and Google Chrome.
This kind is unique in that it is more sophisticated. Its deployment's cyber enemies have honed its strengths, increasing its potency and detection resistance. Using GoLang tools like GoReSym for comprehensive evaluation demonstrates the threat actors' careful planning and calculated technique.
Go Stealer: Evolution of Threat
The Go Stealer first appeared as a free software project on GitHub and quickly became well-known for its capacity to stealthily obtain private data from consumers who aren't paying attention. Its effectiveness and stealthy design rapidly attracted the attention of cyber attackers looking for a sophisticated tool for clandestine data exfiltration. It was written in the Go programming language.
Several cutting-edge characteristics distinguish the Go Stealer from other conventional data thieves. From the beginning, it showed a strong emphasis on browser focusing on, seeking to obtain passwords and login information from particular websites including Edge, Brave, and Google Chrome.The malware's initial iteration was nurtured on the GitHub database, which has the Go Stealer initial edition. Threat actors have improved and altered the code to serve their evil goals, even if the basic structure is freely accessible.
The Go Stealer version that has been discovered as the cause of the current internet spying by the Indian Air Force is not limited to its GitHub roots. It adds features that make it more dangerous, like a wider range of browsers that may be targeted and a brand-new way to exfiltrate data via Slack, a popular messaging app.
Secret Communications and Information Expulsion
This variation is distinguished by its deliberate usage of the Slack API for secret chats. Slack was chosen because it is widely used in company networks and allows harmful activity to blend in with normal business traffic. The purpose of the function "main_Vulpx" is specifically to upload compromised information to the attacker's Slack route, allowing for covert data theft and communication.
The Time and Strategic Objective
There are worries about targeted assaults or espionage activities due to the precise moment of the cyberattack, which coincides with the Indian government's declaration of its acquisition of Su-30 MKI fighter fighters. The deliberate emphasis on gathering cookies and login passwords from web browsers highlights the threat actor's goal of obtaining accurate and private data from Indian Air Force personnel.
Using Caution: Preventing Possible Cyber Espionage
- Alertness Against Misleading Techniques: Current events highlight the necessity of being on the lookout for files that appear harmless but actually have dangerous intent. The Su-30 Acquisition ZIP file is a stark illustration of how these kinds of data might be included in larger-scale cyberespionage campaigns.
- Potentially Wider Impact: Cybercriminals frequently plan coordinated operations to target not just individuals but potentially many users and government officials. Compromised files increase the likelihood of a serious cyber-attack by opening the door for larger attack vectors.
- Important Position in National Security: Recognize the crucial role people play in the backdrop of national security in the age of digitalisation. Organised assaults carry the risk of jeopardising vital systems and compromising private data.
- Establish Strict Download Guidelines: Implement a strict rule requiring file downloads to only come from reputable and confirmed providers. Be sceptical, particularly when you come across unusual files, and make sure the sender is legitimate before downloading any attachments.
- Literacy among Government Employees: Acknowledge that government employees are prime targets as they have possession of private data. Enable people by providing them with extensive cybersecurity training and awareness that will increase their cognition and fortitude.
Conclusion
Indian Air Force cyber surveillance attack highlights how sophisticated online dangers have become in the digital era. Threat actors' deliberate and focused approach is demonstrated by the deceptive usage of a ZIP archive that is camouflaged and paired with a sophisticated instance of the Go Stealer virus. An additional level of complication is introduced by integrating Slack for covert communication. Increased awareness, strict installation guidelines, and thorough cybersecurity education for government employees are necessary to reduce these threats. In the digital age, protecting national security necessitates ongoing adaptation as well as safeguards toward ever-more potent and cunning cyber threats.
References
- https://www.overtoperator.com/p/indianairforcemalwaretargetpotential
- https://cyberunfolded.in/blog/indian-air-force-targeted-in-sophisticated-cyber-attack-with-su-30-procurement-zip-file#go-stealer-a-closer-look-at-its-malicious-history
- https://thecyberexpress.com/cyberattack-on-the-indian-air-force/https://therecord.media/indian-air-force-infostealing-malware


