#FactCheck - Viral Image of AIMIM President Asaduddin Owaisi Holding Lord Rama Portrait Proven Fake
Executive Summary:
In recent times an image showing the President of AIMIM, Asaduddin Owaisi holding a portrait of Hindu deity Lord Rama, has gone viral on different social media platforms. After conducting a reverse image search, CyberPeace Research Team then found that the picture was fake. The screenshot of the Facebook post made by Asaduddin Owaisi in 2018 reveals him holding Ambedkar’s picture. But the photo which has been morphed shows Asaduddin Owaisi holding a picture of Lord Rama with a distorted message gives totally different connotations in the political realm because in the 2024 Lok Sabha elections, Asaduddin Owaisi is a candidate from Hyderabad. This means there is a need to ensure that before sharing any information one must check it is original in order to eliminate fake news.

Claims:
AIMIM Party leader Asaduddin Owaisi standing with the painting of Hindu god Rama and the caption that reads his interest towards Hindu religion.



Fact Check:
In order to investigate the posts, we ran a reverse search of the image. We identified a photo that was shared on the official Facebook wall of the AIMIM President Asaduddin Owaisi on 7th April 2018.

Comparing the two photos we found that the painting Asaduddin Owaisi is holding is of B.R Ambedkar whereas the viral image is of Lord Rama, and the original photo was posted in the year 2018.


Hence, it was concluded that the viral image was digitally modified to spread false propaganda.
Conclusion:
The photograph of AIMIM President Asaduddin Owaisi holding up one painting of Lord Rama is fake as it has been morphed. The photo that Asaduddin Owaisi uploaded on a Facebook page on 7 Apr 2018 depicted him holding a picture of Bhimrao Ramji Ambedkar. This photograph was digitally altered and the false captions were written to give an altogether different message of Asaduddin Owaisi. It has even highlighted the necessity of fighting fake news that has spread widely through social media platforms especially during the political realm.
- Claim: AIMIM President Asaduddin Owaisi was holding a painting of the Hindu god Lord Rama in his hand.
- Claimed on: X (Formerly known as Twitter)
- Fact Check: Fake & Misleading
Related Blogs

THREE CENTRES OF EXCELLENCE IN ARTIFICIAL INTELLIGENCE:
India’s Finance Minister, Mrs. Nirmala Sitharaman, with a vision of ‘Make AI for India’ and ‘Make AI work for India, ’ announced during the presentation of Union Budget 2023 that the Indian Government is planning to set up three ‘Centre of Excellence’ for Artificial Intelligence in top Educational Institutions to revolutionise fields such as health, agriculture, etc.
Under the ‘Amirt Kaal,’ i.e., the budget of 2023 is a stepping stone by the government to have a technology-driven knowledge-based economy and the seven priorities that have been set up by the government called ‘Saptarishi’ such as inclusive development, reaching the last mile, infrastructure investment, unleashing potential, green growth, youth power, and financial sector will guide the nation in this endeavor along with leading industry players that will partner in conducting interdisciplinary research, developing cutting edge applications and scalable problem solutions in such areas.
The government has already formed the roadmap for AI in the nation through MeitY, NASSCOM, and DRDO, indicating that the government has already started this AI revolution. For AI-related research and development, the Centre for Artificial Intelligence and Robotics (CAIR) has already been formed, and biometric identification, facial recognition, criminal investigation, crowd and traffic management, agriculture, healthcare, education, and other applications of AI are currently being used.
Even a task force on artificial intelligence (AI) was established on August 24, 2017. The government had promised to set up Centers of Excellence (CoEs) for research, education, and skill development in robotics, artificial intelligence (AI), digital manufacturing, big data analytics, quantum communication, and the Internet of Things (IoT) and by announcing the same in the current Union budget has planned to fulfill the same.
The government has also announced the development of 100 labs in engineering institutions for developing applications using 5G services that will collaborate with various authorities, regulators, banks, and other businesses.
Developing such labs aims to create new business models and employment opportunities. Among others, it will also create smart classrooms, precision farming, intelligent transport systems, and healthcare applications, as well as new pedagogy, curriculum, continual professional development dipstick survey, and ICT implementation will be introduced for training the teachers.
POSSIBLE ROLES OF AI:
The use of AI in top educational institutions will help students to learn at their own pace, using AI algorithms providing customised feedback and recommendations based on their performance, as it can also help students identify their strengths and weaknesses, allowing them to focus their study efforts more effectively and efficiently and will help train students in AI and make the country future-ready.
The main area of AI in healthcare, agriculture, and sustainable cities would be researching and developing practical AI applications in these sectors. In healthcare, AI can be effective by helping medical professionals diagnose diseases faster and more accurately by analysing medical images and patient data. It can also be used to identify the most effective treatments for specific patients based on their genetic and medical history.
Artificial Intelligence (AI) has the potential to revolutionise the agriculture industry by improving yields, reducing costs, and increasing efficiency. AI algorithms can collect and analyse data on soil moisture, crop health, and weather patterns to optimise crop management practices, improve yields and the health and well-being of livestock, predict potential health issues, and increase productivity. These algorithms can identify and target weeds and pests, reducing the need for harmful chemicals and increasing sustainability.
ROLE OF AI IN CYBERSPACE:
Artificial Intelligence (AI) plays a crucial role in cyberspace. AI technology can enhance security in cyberspace, prevent cyber-attacks, detect and respond to security threats, and improve overall cybersecurity. Some of the specific applications of AI in cyberspace include:
- Intrusion Detection: AI-powered systems can analyse large amounts of data and detect signs of potential cyber-attacks.
- Threat Analysis: AI algorithms can help identify patterns of behaviour that may indicate a potential threat and then take appropriate action.
- Fraud Detection: AI can identify and prevent fraudulent activities, such as identity theft and phishing, by analysing large amounts of data and detecting unusual behaviour patterns.
- Network Security: AI can monitor and secure networks against potential cyber-attacks by detecting and blocking malicious traffic.
- Data Security: AI can be used to protect sensitive data and ensure that it is only accessible to authorised personnel.
CONCLUSION:
Introducing AI in top educational institutions and partnering it with leading industries will prove to be a stepping stone to revolutionise the development of the country, as Artificial Intelligence (AI) has the potential to play a significant role in the development of a country by improving various sectors and addressing societal challenges. Overall, we hope to see an increase in efficiency and productivity across various industries, leading to increased economic growth and job creation, improved delivery of healthcare services by increasing access to care and, improving patient outcomes, making education more accessible and effective as AI has the potential to improve various sectors of a country and contribute to its overall development and progress. However, it’s important to ensure that AI is developed and used ethically, considering its potential consequences and impact on society.
References:

A video circulating widely on social media claims to show former US President Donald Trump issuing a threat to India over its relationship with Russia. In the clip, Trump is allegedly heard warning New Delhi that if it does not cut bilateral ties with Moscow, the United States would “treat India the same way Pakistan did during the May war.”
The reference to the “May war” appears to point to the India-Pakistan military escalation in May 2025, which followed the Pahalgam terror attack and India’s retaliatory strikes under Operation Sindoor targeting terror infrastructure.
However, research done by the Cyber Peace Foundation has found that the video is misleading and digitally manipulated.
The visuals used in the viral clip are genuine and were taken from a press briefing addressed by Donald Trump on January 3, 2026. However, the audio track accompanying the video has been fabricated and falsely superimposed to
misrepresent his remarks. In the original address, Trump was speaking about a US-led military operation in Caracas that reportedly resulted in the capture of Venezuelan President Nicolás Maduro and his wife. He made no reference to India, Russia, or any geopolitical warning involving New Delhi.
Claim:
On January 10, an X (formerly Twitter) user, Niki Chiri (@cutehunmee), shared a video claiming it showed Donald Trump threatening India over its ties with Russia.
In the clip, Trump is purportedly heard stating that unless India severed its relationship with Moscow, the United States would respond in a manner similar to Pakistan’s actions during the May conflict.
The post quickly gained traction, with several users amplifying the claim. Iink,archive link and screenshot
Research:
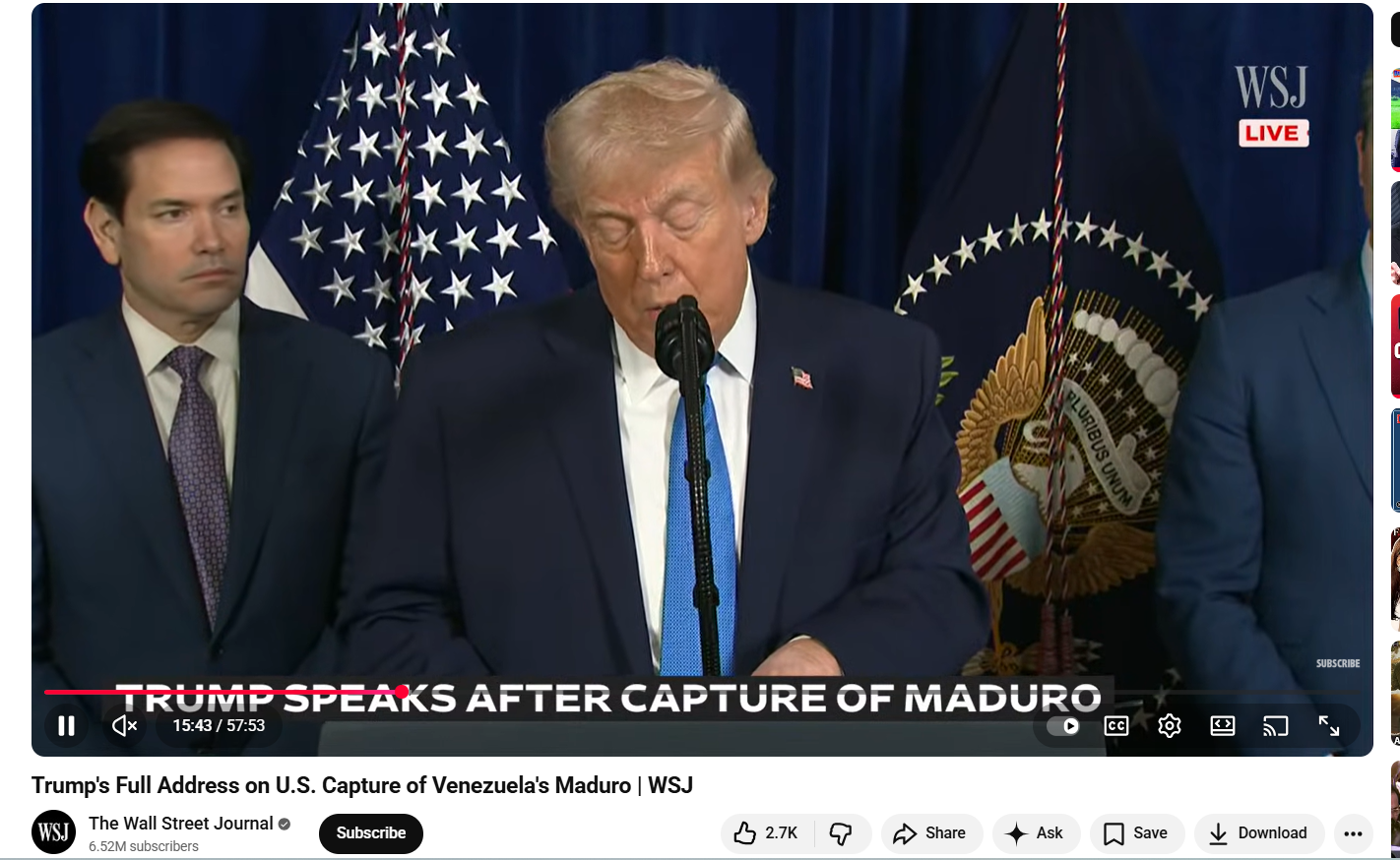
To verify the authenticity of the video, the Cyber Peace Foundation conducted a reverse image and video analysis. A Google Lens search led investigators to a longer version of the same footage uploaded on the official YouTube channel of The Wall Street Journal, a prominent US-based news outlet.
A comparison confirmed that both videos shared identical visuals, background elements, and camera angles, establishing that the viral clip was sourced from the same press address.
A review of the full speech, however, showed that Trump did not issue any warning to India, nor did he mention Russia or the May conflict. His remarks were strictly focused on developments in Venezuela.
This confirmed that the viral video had been digitally altered. Here is the link to the original video, along with a screenshot:
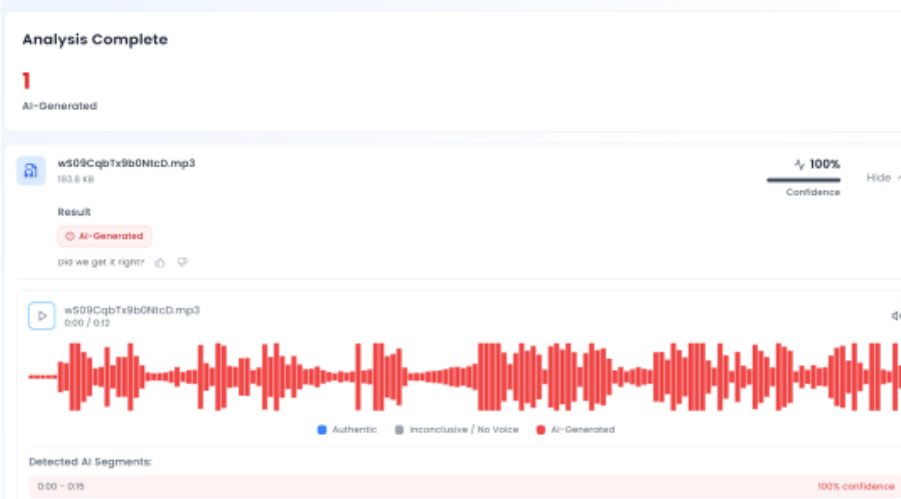
In the next phase of the research, the audio track from the viral clip was extracted and analysed using the AI-based voice detection tool Aurigin. The results indicated a high likelihood that the voice in the video was artificially generated, further confirming that the audio did not originate from Trump’s original speech. A screenshot of the result is provided below.
Conclusion
The claim that a video shows Donald Trump threatening India over its ties with Russia is false. The Cyber Peace Foundation found that while the visuals were taken from a real press address, the audio was fabricated and overlaid to falsely attribute threatening statements to Trump. The manipulated video was circulated online to mislead viewers and spread disinformation.
.webp)
Executive Summary:
Cyber incidents are evolving along with time, they are designed to attract and lure people through social networking sites and/or messaging services. In the recent past a spate of messages alleging that TRAI is offering ‘3 months free recharge with free voice calls and internet for 4g/5g with 200 GB free data’. These messages display the TRAI logo with attractive offers to trick the users into revealing their personal details. This blog discusses the functioning of this free mobile recharge scheme, its methods and guidelines on how to avoid such fake schemes. This blog explains the importance of vigilance and verification when receiving any links, emphasizing the need to report suspicious activities and educate others to prevent identity theft and protect personal information.
Claim:
The message circulated an enticing offer: free mobile recharge for 3 months which provides unlimited free voice calls with 200GB 4G/5G data with TRAI logo. The key characteristics of the false claims are
- Official Branding: The logo of TRAI has been viewed as a deceptive facade of credibility.
- Unrealistic Offers: It is accompanied by a free recharge , which is intended for an extended period indefinite period, like most fraudsters’ bait.
- Urgency and Exclusivity: The offer is for a limited time to make urgency forcing the receiver to take the offer without confirmation.
The Deceptive Scheme:
Organized systematically, the fraudulent campaign usually proceeds in several steps, all of which aim at extracting the victim’s personal data. Here’s a breakdown of the scheme:
1. Initial Contact: Such messages or calls reach the users’ inboxes or phone numbers through social media applications such as WhatsApp or through text messages. These messages further implies that the user was chosen for the special offer from TRAI, which elicits the interest of the user.
2. Information Request: To claim the purported offer, users are directed to a website or asked to reply with personal details, including:
- Phone number
- State of residence
- SIM provider details
This is useful for the scammers as they harvest information which can be used to conduct identity theft or sold to others on the shady part of the internet known as the ‘Dark Web’.
3. Fake Confirmation: After providing all the information, a congratulatory message appears on the screen showing that their phone number is eligible for the offer. The user is compelled to forward the message to many phone numbers through whatsapp to get the offer.
4. Pressure Tactics: The message often implies a sense of time constraint or fear which psychologically produces pressure to provide all the user information. For example, users are given messages such as that if they do not ‘act now’, they will lose their mobile service.
Analyzing the Fraudulent Campaign
The TRAI fraudulent recharge scheme case depicts that social engineering is used in cyber crimes. Here are some key aspects that characterize this campaign:
- Sophisticated Social Engineering
Scammers take advantage of the holders’ confidence in official bodies such as TRAI. By using official TRAI logos, official language they try to deceive even cautious people.
- Viral Spread
The user is compelled to share the given message to friends and groups; this is an excellent strategy to spread the scam. It not only spreads the fraudulent message but also tries to extract the details of other people.
- Technical Analysis

- Domain Name: SGOFF[.]CYOU
- Registry Domain ID: D472308342-CNIC
- Registrar WHOIS Server: whois.hkdns.hk
- Registrar URL: http://www.hkdns.hk
- Updated Date: 2024-07-24T18:50:48.0Z
- Creation Date: 2024-07-19T18:48:44.0Z
- Registry Expiry Date: 2025-07-19T23:59:59.0Z
- Registrar: West263 International Limited
- Registrar IANA ID: 1915
- Registrant State/Province: Anhui
- Registrant Country: CN
- Name Server: NORMAN.NS.CLOUDFLARE.COM
- Name Server: PAM.NS.CLOUDFLARE.COM
- DNSSEC: unsigned
Cloudflare Inc. is used to cover the scam. The real website always uses the older domain while this url has been registered recently which indicates that this link is a scam.

The graph indicates that some of the communicated files and websites are malicious.
CyberPeace Advisory and Best Practice:
In light of the growing threat posed by such scams, the Research Wing of CyberPeace recommend the following best practices to help users protect themselves:
1. Verify Communications: It is always advisable to visit the official site of the organization or call the official contact numbers of the company to speak to their customer care and clarify about the offers.
2. Do not share personal information: No genuine organization will call the people for personal information. Step carefully and do not provide personal information that will lead to identity theft when dealing with such offers.
3. Report Fraudulent Activity: If one receives any calls or messages that seem to be suspicious, then the user can report cyber crimes to the National Cyber Crime Reporting Portal on www. cybercrime. gov. in or call on 1930. Such scams are reportable and assist the authorities in tracking and fighting the vice.
4. Educate Others : Always raise awareness among friends by sharing these kinds of scams. Educating people helps to avoid them falling prey to such fraudulent schemes.
5. Use Reliable Resources : Always refer to official sources or websites for any kind of offers or promotions.
Conclusion:
The free recharge scheme for 3 months with the logo of TRAI is a fraudulent scam. There is no official information from TRAI or in their official website about this free recharge scheme. Though the scheme looks attractive, it is deceptive. Through this, the scammers are trying to collect personal details of the individual. Before clicking any links, it is necessary to check the authenticity of the information, report these kinds of incidents to spread awareness among people. Always be safe and be vigilant.


