#FactCheck - Viral video attributed to the Australian Prime Minister is AI-generated; claim of cancelling Pakistani visas is false
A video is being shared on social media, falsely attributing it to Australian Prime Minister Anthony Albanese. The video claims that following the Bondi Beach attack, he decided to cancel the visas of Pakistani citizens.
An investigation by the Cyber Peace Foundation revealed that the viral video was created using AI. In the original video, Anthony Albanese was answering questions related to the Climate Change Bill during a press conference. It is important to note that in the attack that took place last Sunday (14 December) at Bondi Beach in Sydney, New South Wales, Australia, 15 people were killed. According to Australian police, the attack targeted the Jewish community. New South Wales Police Commissioner Mal Lanyon stated that the two accused involved in the attack were father and son—one aged 50 and the other 24. Media reports identified them as Sajid and Naved Akram.
Claim:
On 14 December 2025, a user on the social media platform X shared a video claiming, “After the attack by a Pakistani Islamic terrorist, the Australian Prime Minister has decided to cancel the visas of all Pakistanis. The whole world is troubled by this community, and in India it is said that Abdul cannot buy a house in a Hindu neighbourhood.”
The link to the related post, its archived version, and screenshots can be seen below:
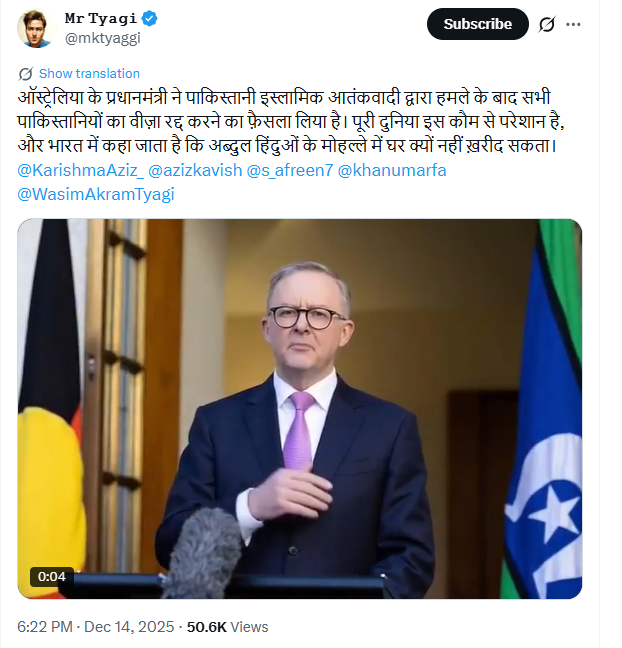
Investigation:Upon closely examining the viral video, we suspected it to be AI-generated. Subsequently, we scanned the video using the AI detection tool aurigin.ai. According to the results provided by the tool, the video was found to be AI-generated.
Related Blogs
.webp)
Introduction
The AI Action Summit is a global forum that brings together world leaders, policymakers, technology experts, and industry representatives to discuss AI governance, ethics, and its role in society. This year, the week-long Paris AI Action Summit officially culminated on the 11th of February, 2025. It brought together experts from the industry, policymakers, and other dignitaries to discuss Artificial Intelligence and its challenges. The event was co-chaired by Indian Prime Minister Narendra Modi and French President Emmanuel Macron. In line with the summit, the Indian delegation actively engaged in the 2nd India-France AI Policy Roundtable, an official side event of the summit, and the 14th India-France CEOs Forum. These discussions were on diverse sectors including defense, aerospace, technology, etc. among other things.
Prime Minister Modi’s Address
During the AI Action Summit in Paris, Prime Minister Narendra Modi drew attention to the revolutionary effect of AI in politics, the economy, security, and society. Stressing the requirement of international cooperation, he promoted strong frameworks of governance to combat AI-based risks and consequently, build public confidence in new technologies. Needed efforts with respect to cybersecurity issues such as deepfakes and disinformation were also acknowledged.
Democratising AI, and sharing its benefits, particularly with the Global South not only aligned with Sustainable Development Goals (SDGs) but also affirmed India’s resolve towards sharing expertise and best practices. India’s remarkable feat of creating a Digital Public Infrastructure, that caters to a population of 1.4 billion through open and accessible technology was highlighted as well.
Among the key announcements, India revealed its plans to create its own Large Language Model (LLM) that reflects the country's linguistic diversity, strengthening its AI aspirations. Further, India will be hosting the next AI Action Summit, reaffirming its position in international AI leadership. The Prime Minister also welcomed France's initiatives, such as the launch of the "AI Foundation" and the "Council for Sustainable AI", initiated by President Emmanuel Macron. He emphasized the necessity to extend the Global Partnership for AI and to get it more representative and inclusive so that Global South voices are actually incorporated into AI innovation and governance.
Other Perspectives
Though there were 58 countries that signed the international agreement on a more open, inclusive, sustainable, and ethical approach to AI development (including India, France, and China), the UK and the US have refused to sign the international agreement at the AI Summit stating their issues with global governance and national security. While the former raised concerns about the lack of sufficient details regarding the establishment of global AI governance and AI’s effect on national security as their reason, the latter showcased its reservations about the overly wide AI regulations which had the potential to hamper a transformative industry. Meanwhile, the US is also looking forward to ‘Stargate’, its $500 billion AI infrastructure project alongside the companies- OpenAI, Softbank, and Oracle.
CyberPeace Insights
The Summit has garnered greater significance with the backdrop of the release of platforms such as DeepSeek R1, China’s AI assistant system similar to that of OpenAI’s ChatGPT. On its release, it was the top-rated free application on Apple’s app store and sent the technology stocks tumbling. Moreover, investors world over appreciated the creation of the model which was made roughly in about $5 million while other AI companies spent more in comparison (keeping in mind the restrictions caused by the chip export controls in China). This breakthrough challenges the conventional notion that massive funding is a prerequisite for innovation, offering hope for India’s burgeoning AI ecosystem. With the IndiaAI mission and fewer geopolitical restrictions, India stands at a pivotal moment to drive responsible AI advancements.
References:
- https://www.mea.gov.in/press-releases.htm?dtl/39023/Prime_Minister_cochairs_AI_Action_Summit_in_Paris_February_11_2025
- https://indianexpress.com/article/explained/explained-sci-tech/what-is-stargate-trumps-500-billion-ai-project-9793165/
- https://pib.gov.in/PressReleasePage.aspx?PRID=2102056
- https://pib.gov.in/PressReleasePage.aspx?PRID=2101947
- https://pib.gov.in/PressReleasePage.aspx?PRID=2101896
- https://www.timesnownews.com/technology-science/uk-and-us-decline-to-sign-global-ai-agreement-at-paris-ai-action-summit-here-is-why-article-118164497
- https://www.thehindu.com/sci-tech/technology/india-57-others-sign-paris-joint-statement-on-inclusive-sustainable-ai/article69207937.ece

Executive Summary:
Apple has quickly responded to two severe zero-day threats, CVE-2024-44308 and CVE-2024-44309 in iOS, macOS, visionOS, and Safari. These defects, actively used in more focused attacks presumably by state actors, allow for code execution and cross-site scripting (XSS). In a report shared by Google’s Threat Analysis Group, the existing gaps prove that modern attacks are highly developed. Apple’s mitigation comprises memory management, especially state management to strengthen device security. Users are encouraged to update their devices as soon as possible, turn on automatic updates and be careful in the internet space to avoid these new threats.
Introduction
Apple has proved its devotion to the security issue releasing the updates fixing two zero-day bugs actively exploited by hackers. The bugs, with the IDs CVE-2024-44308 and CVE-2024-44309, are dangerous and can lead to code execution and cross-site scripting attacks. The vulnerabilities have been employed in attack and the significance of quick patch release for the safety of the users.
Vulnerabilities in Detail
The discovery of vulnerabilities (CVE-2024-44308, CVE-2024-44309) is credited to Clément Lecigne and Benoît Sevens of Google's Threat Analysis Group (TAG). These vulnerabilities were found in JavaScriptCore and WebKit, integral components of Apple’s web rendering framework. The details of these vulnerabilities are mentioned below:
CVE-2024-44308
- Severity: High (CVSS score: 8.8)
- Description: A flaw in the JavaScriptCore component of WebKit. Malicious web content could cause code to be executed on the target system and make the system vulnerable to the full control of the attacker.
- Technical Finding: This vulnerability involves bad handling of memory in the course of executing JavaScript, allowing the use of injected payloads remotely by the attackers.
CVE-2024-44309
- Severity: Moderate (CVSS score: 6.1)
- Description: A cookie management flaw in WebKit which might result in cross site scripting (XSS). This vulnerability enables the attackers to embed unauthorized scripts into genuine websites and endanger the privacy of users as well as their identities.
- Technical Finding: This issue arises because of wrong handling of cookies at the state level while processing the maliciously crafted web content and provides an unauthorized route to session data.
Affected Systems
These vulnerabilities impact a wide range of Apple devices and software versions:
- iOS 18.1.1 and iPadOS 18.1.1: For devices including iPhone XS and later, iPad Pro (13-inch), and iPad mini 5th generation onwards.
- iOS 17.7.2 and iPadOS 17.7.2: Supports earlier models such as iPad Pro (10.5-inch) and iPad Air 3rd generation.
- macOS Sequoia 15.1.1: Specifically targets systems running macOS Sequoia.
- visionOS 2.1.1: Exclusively for Apple Vision Pro.
- Safari 18.1.1: For Macs running macOS Ventura and Sonoma.
Apple's Mitigation Approach
Apple has implemented the following fixes:
- CVE-2024-44308: Enhanced input validation and robust memory checks to prevent arbitrary code execution.
- CVE-2024-44309: Improved state management to eliminate cookie mismanagement vulnerabilities.
These measures ensure stronger protection against exploitation and bolster the underlying security architecture of affected components.
Broader Implications
The exploitation of these zero-days highlights the evolving nature of threat landscapes:
- Increasing Sophistication: Attackers are refining techniques to target niche vulnerabilities, bypassing traditional defenses.
- Spyware Concerns: These flaws align with the modus operandi of spyware tools, potentially impacting privacy and national security.
- Call for Timely Updates: Users delaying updates inadvertently increase their risk exposure
Technical Recommendations for Users
To mitigate potential risks:
- Update Devices Promptly: Install the latest patches for iOS, macOS, visionOS, and Safari.
- Enable Automatic Updates: Ensures timely application of future patches.
- Restrict WebKit Access: Avoid visiting untrusted websites until updates are installed.
- Monitor System Behavior: Look for anomalies that could indicate exploitation.
Conclusion
The exploitation of CVE-2024-44308 and CVE-2024-44309 targeting Apple devices highlight the importance of timely software updates to protect users from potential exploitation. The swift action of Apple by providing immediate improved checks, state management and security patches. Users are therefore encouraged to install updates as soon as possible to guard against these zero day flaws.
References:
- https://support.apple.com/en-us/121752
- https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2024-44308
- https://securityonline.info/cve-2024-44308-and-cve-2024-44309-apple-addresses-zero-day-vulnerabilities/

Introduction
In the hyper-connected era, something as mundane as charging your phone can become a gateway to cyberattacks. A recent experience of Assam Chief Minister Himanta Biswa Sarma has reignited fears of an emerging digital menace called juice jacking. Sarma, who was taking an Emirates flight from Delhi to Dubai, used an international charger and cable provided by another passenger on board. As he afterwards reported on X (formerly Twitter), the passenger got off while he slept and so could not return the borrowed items. Though most people admired the CM's humility and openness, cybersecurity experts and citizens were quick to point out a possible red flag, that it could be a juice-jacking attempt. Whether by design or not, the scene calls out to the concealed risks of using unfamiliar charging equipment, particularly for those who hold sensitive roles.
What Is Juice Jacking?
Juice jacking takes advantage of the multi-purpose nature of USB connectors, which can carry both electrical energy and information. Attackers hack USB ports or cables to either:
- Insert harmful payloads (malware, spyware, ransomware) during power transfer, or
- Create unauthorised data pathways for silent information exfiltration.
Types of Juice Jacking Attacks
- Data Theft (Exfiltration Attack): The USB cable or port is rigged to silently extract files, media, contacts, keystrokes, or login information from the attached phone.
- Malware Injection (Payload Attack): The USB device is set to impersonate a Human Interface Device (HID), such as a keyboard. It sends pre-defined commands (shell scripts, command-line inputs) to the host, loading backdoors or spying tools.
- Firmware Tampering: In more sophisticated cases, attackers implement persistent malware at the bootloader or firmware level, bypassing antivirus protection and living through factory resets.
- Remote Command-and-Control Installation: Certain strains of malware initiate backdoors to enable remote access to the device over the internet upon reconnection to a live network.
Why the Assam CM’s Incident Raised Flags
Whereas CM Sarma's experience was one of thanks, the digital repercussions of this scenario are immense:
- High-value targets like government officials, diplomats, and corporate executives tend to have sensitive information.
- A hacked cable can be used as a spy tool, sending information or providing remote access.
- With the USB On-The-Go (OTG) feature in contemporary Android and iOS devices, an attacker can run autorun scripts and deploy payloads at device connect/disconnect.
- If device encryption is poor or security settings are incorrectly configured, attackers may gain access to location, communication history, and app credentials.
Technical Juice Jacking Indicators
The following are indications that a device could have been attacked:
- Unsolicited request for USB file access or data syncing on attaching.
- Faster battery consumption (from background activities).
- The device is acting strangely, launching apps or entering commands without user control.
- Installation of new apps without authorisation.
- Data consumption increases even if no browsing is ongoing.
CyberPeace Tech-Policy Advisory: Preventing Juice Jacking
- Hardware-Level Mitigation
- Utilise USB Data Blockers: Commonly referred to as "USB condoms," such devices plug the data pins (D+ and D-), letting only power (Vcc and GND) pass through. This blocks all data communication over USB.
- Charge-Only Cables: Make use of cables that physically do not have data lines. These are specifically meant to provide power only.
- Carry a Power Bank: Use your own power source, if possible, for charging, particularly in airports, conferences, or flights.
- Operating System(OS) Level Protections
- iOS Devices:
Enable USB Restricted Mode:
Keep USB accessories from being able to connect when your iPhone is locked.
Settings → Face ID & Passcode → USB Accessories → Off
- Android Devices:
Disable USB Debugging:
Debugging makes device access available for development, but it can be taken advantage of. If USB Debugging is turned on, and someone connects your phone to a computer, they might be able to access your data, install apps, or even control your phone, especially if your phone is unlocked. Hence, it should be kept off.
Settings → Developer Options → USB Debugging → Off
- Set USB Default to 'Charge Only'
Settings → Connected Devices → USB Preferences → Default USB Configuration → Charge Only
3) Behavioural Recommendations
- Never take chargers or USB cables from strangers.
- Don't use public USB charging points, particularly at airports or coffee shops.
- Turn full-disk encryption on on your device. It is supported by most Android and all iOS devices.
- Deploy endpoint security software that can identify rogue USB commands and report suspicious behaviour.
- Check cables or ports physically, many attack cables are indistinguishable from legitimate ones (e.g., O.MG cables).
Conclusion
"Juice jacking is no longer just a theoretical or obscure threat. In the age of highly mobile, USB-charged devices, physical-layer attacks are becoming increasingly common, and their targets are growing more strategic. The recent case involving the Assam Chief Minister was perhaps harmless, but it did serve to underscore a fundamental vulnerability in daily digital life. As mobile security becomes more relevant to individuals and organisations worldwide, knowing about hardware-based attacks like juice jacking is essential. Security never needs to be sacrificed for convenience, particularly when an entire digital identity might be at risk with just a single USB cable.
References
- https://www.indiatoday.in/trending-news/story/assam-chief-minister-himanta-biswa-sarma-x-post-on-emirates-passenger-sparks-juice-jacking-concerns-2706349-2025-04-09
- https://www.cert-in.org.in/s2cMainServlet?pageid=PUBVLNOTES02&VLCODE=CIAD-2016-0085
- https://www.fcc.gov/juice-jacking-tips-to-avoid-it
- https://www.cyberpeace.org/resources/blogs/juice-jacking
- https://support.apple.com/en-in/HT208857
- https://developer.android.com/studio/debug/dev-options


