#FactCheck - Viral Clip and Newspaper Article Claiming 18% GST on 'Good Morning' Messages Debunked
Executive Summary
A recent viral message on social media such as X and Facebook, claims that the Indian Government will start charging an 18% GST on "good morning" texts from April 1, 2024. This news is misinformation. The message includes a newspaper clipping and a video that was actually part of a fake news report from 2018. The newspaper article from Navbharat Times, published on March 2, 2018, was clearly intended as a joke. In addition to this, we also found a video of ABP News, originally aired on March 20, 2018, was part of a fact-checking segment that debunked the rumor of a GST on greetings.

Claims:
The claim circulating online suggests that the Government will start applying a 18% of GST on all "Good Morning" texts sent through mobile phones from 1st of April, this year. This tax would be added to the monthly mobile bills.




Fact Check:
When we received the news, we first did some relevant keyword searches regarding the news. We found a Facebook Video by ABP News titled Viral Sach: ‘Govt to impose 18% GST on sending good morning messages on WhatsApp?’

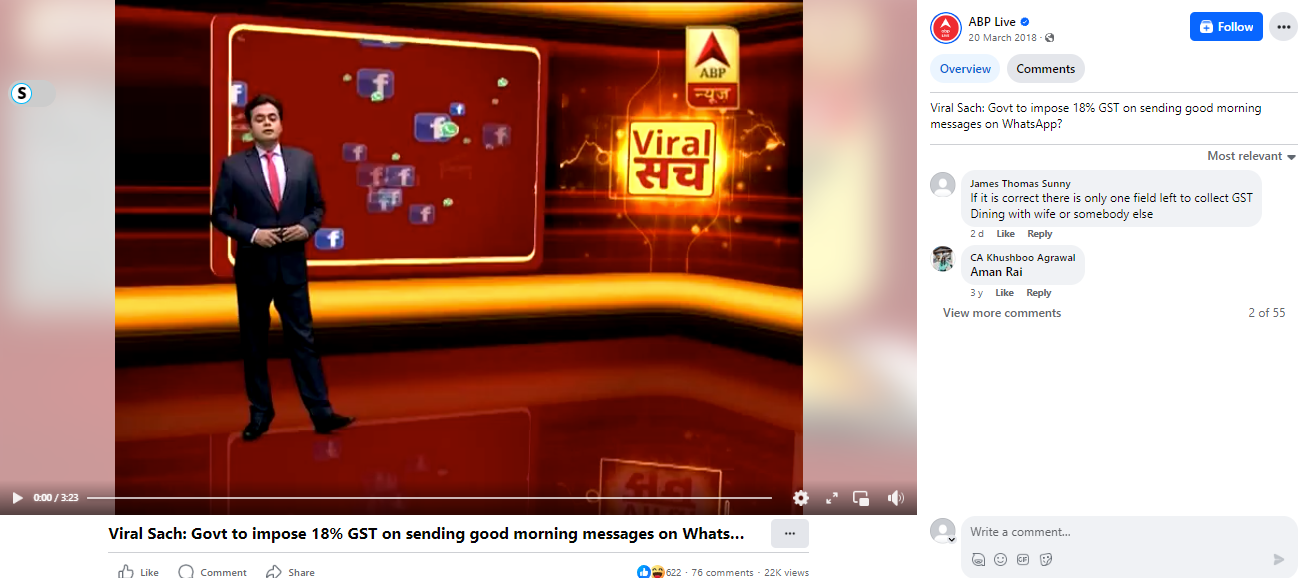
We have watched the full video and found out that the News is 6 years old. The Research Wing of CyberPeace Foundation also found the full version of the widely shared ABP News clip on its website, dated March 20, 2018. The video showed a newspaper clipping from Navbharat Times, published on March 2, 2018, which had a humorous article with the saying "Bura na mano, Holi hain." The recent viral image is a cutout image from ABP News that dates back to the year 2018.
Hence, the recent image that is spreading widely is Fake and Misleading.
Conclusion:
The viral message claiming that the government will impose GST (Goods and Services Tax) on "Good morning" messages is completely fake. The newspaper clipping used in the message is from an old comic article published by Navbharat Times, while the clip and image from ABP News have been taken out of context to spread false information.
Claim: India will introduce a Goods and Services Tax (GST) of 18% on all "good morning" messages sent through mobile phones from April 1, 2024.
Claimed on: Facebook, X
Fact Check: Fake, made as Comic article by Navbharat Times on 2 March 2018
Related Blogs
Executive Summary:
New Linux malware has been discovered by a cybersecurity firm Volexity, and this new strain of malware is being referred to as DISGOMOJI. A Pakistan-based threat actor alias ‘UTA0137’ has been identified as having espionage aims, with its primary focus on Indian government entities. Like other common forms of backdoors and botnets involved in different types of cyberattacks, DISGOMOJI, the malware allows the use of commands to capture screenshots, search for files to steal, spread additional payloads, and transfer files. DISGOMOJI uses Discord (messaging service) for Command & Control (C2) and uses emojis for C2 communication. This malware targets Linux operating systems.
The DISCOMOJI Malware:
- The DISGOMOJI malware opens a specific channel in a Discord server and every new channel corresponds to a new victim. This means that the attacker can communicate with the victim one at a time.
- This particular malware connects with the attacker-controlled Discord server using Emoji, a form of relay protocol. The attacker provides unique emojis as instructions, and the malware uses emojis as a feedback to the subsequent command status.
- For instance, the ‘camera with flash’ emoji is used to screenshots the device of the victim or to steal, the ‘fox’ emoji cracks all Firefox profiles, and the ‘skull’ emoji kills the malware process.
- This C2 communication is done using emojis to ensure messaging between infected contacts, and it is almost impossible for Discord to shut down the malware as it can always change the account details of Discord it is using once the maliciou server is blocked.
- The malware also has capabilities aside from the emoji-based C2 such as network probing, tunneling, and data theft that are needed to help the UTA0137 threat actor in achieving its espionage goals.
Specific emojis used for different commands by UTA0137:
- Camera with Flash (📸): Captures a picture of the target device’s screen as per the victim’s directions.
- Backhand Index Pointing Down (👇): Extracts files from the targeted device and sends them to the command channel in the form of attachments.
- Backhand Index Pointing Right (👉): This process involves sending a file found on the victim’s device to another web-hosted file storage service known as Oshi or oshi[. ]at.
- Backhand Index Pointing Left (👈): Sends a file from the victim’s device to transfer[. ]sh, which is an online service for sharing files on the Internet.
- Fire (🔥): Finds and transmits all files with certain extensions that exist on the victim’s device, such as *. txt, *. doc, *. xls, *. pdf, *. ppt, *. rtf, *. log, *. cfg, *. dat, *. db, *. mdb, *. odb, *. sql, *. json, *. xml, *. php, *. asp, *. pl, *. sh, *. py, *. ino, *. cpp, *. java,
- Fox (🦊): This works by compressing all Firefox related profiles in the affected device.
- Skull (💀): Kills the malware process in windows using ‘os. Exit()’
- Man Running (🏃♂️): Execute a command on a victim’s device. This command receives an argument, which is the command to execute.
- Index Pointing up (👆) : Upload a file to the victim's device. The file to upload is attached along with this emoji
Analysis:
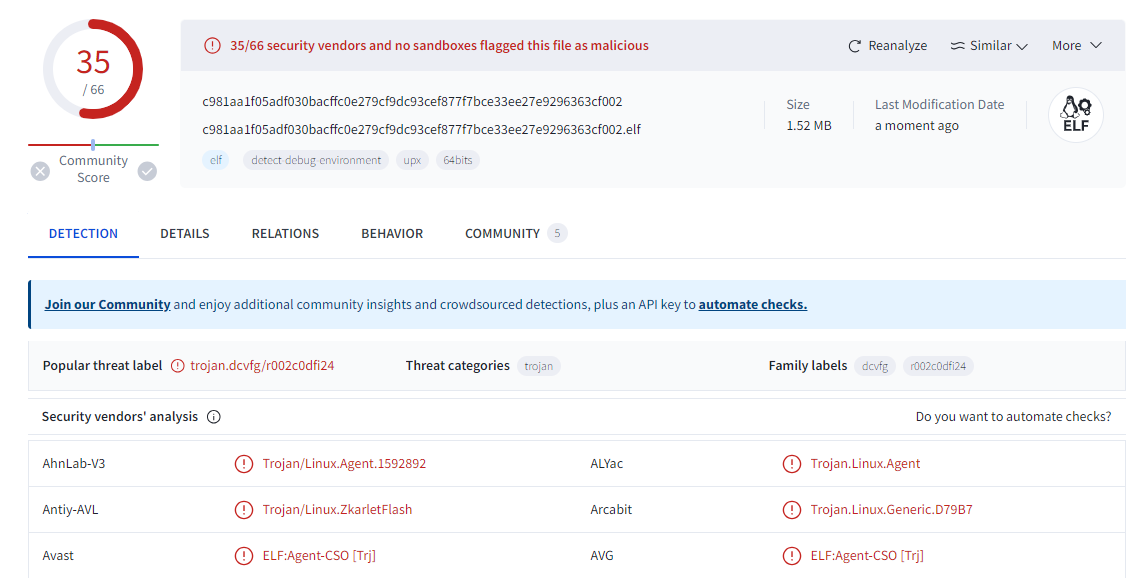
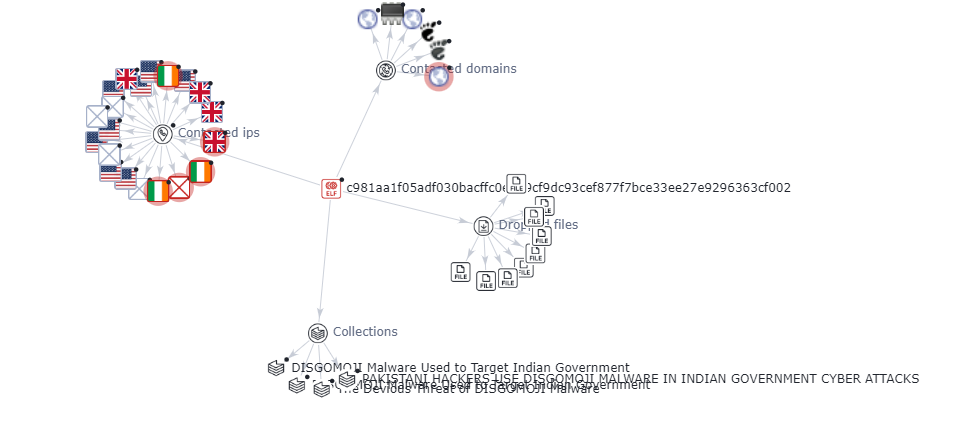
The analysis was carried out for one of the indicator of compromised SHA-256 hash file- C981aa1f05adf030bacffc0e279cf9dc93cef877f7bce33ee27e9296363cf002.
It is found that most of the vendors have marked the file as trojan in virustotal and the graph explains the malicious nature of the contacted domains and IPs.
Discord & C2 Communication for UTA0137:
- Stealthiness: Discord is a well-known messaging platform used for different purposes, which means that sending any messages or files on the server should not attract suspicion. Such stealthiness makes it possible for UTA0137 to remain dormant for greater periods before launching an attack.
- Customization: UTA0137 connected to Discord is able to create specific channels for distinct victims on the server. Such a framework allows the attackers to communicate with each of the victims individually to make a process more accurate and efficient.
- Emoji-based protocol: For C2 communication, emojis really complicates the attempt that Discord might make to interfere with the operations of the malware. In case the malicious server gets banned, malware could easily be recovered, especially by using the Discord credentials from the C2 server.
- Persistence: The malware, as stated above, has the ability to perpetually exist to hack the system and withstand rebooting of systems so that the virus can continue to operate without being detected by the owner of the hacked system.
- Advanced capabilities: Other features of DISGOMOJI are the Network Map using Nmap scanner, network tunneling through Chisel and Ligolo and Data Exfiltration by File Sharing services. These capabilities thus help in aiding the espionage goals of UTA0137.
- Social engineering: The virus and the trojan can show the pop-up windows and prompt messages, for example the fake update for firefox and similar applications, where the user can be tricked into inputting the password.
- Dynamic credential fetching: The malware does not write the hardcoded values of the credentials in order to connect it to the discord server. This also inconveniences analysts as they are unable to easily locate the position of the C2 server.
- Bogus informational and error messages: They never show any real information or errors because they do not want one to decipher the malicious behavior easily.
Recommendations to mitigate the risk of UTA0137:
- Regularly Update Software and Firmware: It is essential to regularly update all the application software and firmware of different devices, particularly, routers, to prevent hackers from exploiting the discovered and disclosed flaws. This includes fixing bugs such as CVE-2024-3080 and CVE-2024-3912 on ASUS routers, which basically entails solving a set of problems.
- Implement Multi-Factor Authentication: There are statistics that show how often user accounts are attacked, it is important to incorporate multi-factor authentication to further secure the accounts.
- Deploy Advanced Malware Protection: Provide robust guard that will help the user recognize and prevent the execution of the DISGOMOJI malware and similar threats.
- Enhance Network Segmentation: Utilize stringent network isolation mechanisms that seek to compartmentalize the key systems and data from the rest of the network in order to minimize the attack exposure.
- Monitor Network Activity: Scanning Network hour to hour for identifying and handling the security breach and the tools such as Nmap, Chisel, Ligolo etc can be used.
- Utilize Threat Intelligence: To leverage advanced threats intelligence which will help you acquire knowledge on previous threats and vulnerabilities and take informed actions.
- Secure Communication Channels: Mitigate the problem of the leakage of developers’ credentials and ways of engaging with the discord through loss of contact to prevent abusing attacks or gaining control over Discord as an attack vector.
- Enforce Access Control: Regularly review and update the user authentication processes by adopting stricter access control measures that will allow only the right personnel to access the right systems and information.
- Conduct Regular Security Audits: It is important to engage in security audits periodically in an effort to check some of the weaknesses present within the network or systems.
- Implement Incident Response Plan: Conduct a risk assessment, based on that design and establish an efficient incident response kit that helps in the early identification, isolation, and management of security breaches.
- Educate Users: Educate users on cybersecurity hygiene, opportunities to strengthen affinity with the University, and conduct retraining on threats like phishing and social engineering.
Conclusion:
The new threat actor named UTA0137 from Pakistan who was utilizing DISGOMOJI malware to attack Indian government institutions using embedded emojis with a command line through the Discord app was discovered by Volexity. It has the capability to exfiltrate and aims to steal the data of government entities. The UTA0137 was continuously improved over time to permanently communicate with victims. It underlines the necessity of having strong protection from viruses and hacker attacks, using secure passwords and unique codes every time, updating the software more often and having high-level anti-malware tools. Organizations can minimize advanced threats, the likes of DISGOMOJI and protect sensitive data by improving network segmentation, continuous monitoring of activities, and users’ awareness.
References:
https://otx.alienvault.com/pulse/66712446e23b1d14e4f293eb
https://thehackernews.com/2024/06/pakistani-hackers-use-disgomoji-malware.html?m=1
https://cybernews.com/news/hackers-using-emojis-to-command-malware/
https://www.volexity.com/blog/2024/06/13/disgomoji-malware-used-to-target-indian-government/

Executive Summary:
Internship scams have infiltrated the academic landscape, scamming students of many prestigious colleges. The students often prefer to carry out internships to gain knowledge and work experience. These scams use the name of popular multinational companies to exploit the students. This report studies the various case studies, their modus operandi, impact on the students and preventive strategies. This report emphasises the importance of awareness and proactive measures to protect students from falling victim to such frauds.
1. Introduction
Internships are the opportunity to overcome the gap between the practical knowledge acquired at the university and practical experience, to get practical skills and contacts in the field of activity, as well as improve employment prospects. Instead, because of high paying internships and interesting positions students have become targets of work scams. As we have seen with the advancement in digital technology, scammers take advantage of the disguise of the internet, making very neat, smart, and convincing scams.
Internship scams are very prevalent and they include fake job listings and phishing schemes as well as payment frauds which make students lose lots of money and also emotionally expose them. In this specific case, this paper examines how these scams work, the warning signs, and ways of protecting students from falling victim to them.
2. Detailed Modus Operandi of Internship Scams
Internship scams often employ a variety of tactics to attract and deceive unsuspecting students. Below is a detailed breakdown of the common methods used by scammers:
- Fake Job Listings and Offers:some text
- Scammers post attractive internship offers on popular job portals, social media platforms, and even send personalised messages via LinkedIn. These listings often mimic the branding and style of reputable companies, including well-designed logos, professional email addresses, and official-looking websites.
- Example: A fake internship offer from a reputed software firm circulates on a job portal, with a professional landing page. Students who apply are quickly “hired” without any interviews, and are asked to pay a security deposit to confirm their acceptance.
- Upfront Payment Requests:some text
- Scammers ask for payment such as registration fees, training materials, background checks, or security deposits. These payments comes under non-refundable payment and it act as the primary revenue stream for the fraudsters.
- Example: A group of students receive internship offers requiring a payment of INR 10,000 for "training materials" and "online assessments." After making the payment, the students never hear back from the company, and all attempts to contact them were futile.
- Phishing and Identity Theft:some text
- Beyond financial fraud, some scams aim to steal personal information. Fake internship applications often require detailed personal data, including identity proofs, bank account details. This data will be used as identity theft or sold on the dark web.
- Example: A student applies for an internship that asks for copies of identification documents and bank details. This information sharing led to unauthorised transactions in their bank account.
- Work-from-Home Frauds:some text
- With the rise of remote work, scammers also offer work-from-home internships that require students to purchase software or pay for specialised training. After payment, students are often given irrelevant tasks or no tasks at all, leaving them with no real work experience.
- Example: An internship advertised as a "remote data analysis role" required students to buy a proprietary software licence. After paying, students realised the software was freely available online, and the internship tasks were non-existent.
- Impersonation of Reputed Companies:some text
- Scammers use the name of well-known companies, they modify the email addresses or create fake websites that look original. They use these platforms to send offer letters, making it difficult for students to identify the scam.
- Example: A scammer creates a fake website mirroring a major consulting firm's internship page. The only difference is a minor change in the URL. Dozens of students are duped into paying registration fees.
3. Case Studies of Real-Life Incidents
- Case Study 1: The Certification Course and Internshipsome text
- A group of students received personalised emails from an official domain of a reputed tech industry providing an internship offer. Students were asked to pay Rs 10,000 to undergo a certification course to carry the internship. After paying the amount, the students did not receive any instructions, and the company was found to be nonexistent. The scammer had spoofed the company’s email domain, making it difficult to trace the source.
- Case Study 2: The Social Media Trapsome text
- A student from a university encountered an internship post on Instagram, advertising roles at a popular fashion brand. The application process involved a "screening fee" of INR 5,000. Despite appearing legitimate, the internship was fake, and the brand had no knowledge of the post. The student's personal data was also compromised, leading to unauthorised social media activity.
- Case Study 3: Internship Providing Social Platformssome text
- A popular internship providing platform, faced an incident where a scammer posted fraudulent internship offers under the guise of a major multinational. The scam involved asking students to purchase expensive software to start their work. The platform had to issue warnings and remove the listings after several complaints.
4. The Impact on Students
The consequences of internship scams extend beyond immediate financial loss, affecting students on multiple levels:
- Financial Impact:some text
- Students lose their money, ranging from minor fees to significant payments.
- Emotional and Psychological Distress:some text
- These kinds of scams can lead to anxiety, depression and loss of confidence in availing the opportunities in future.
- Exposure to Further Scams:some text
- Scammers often share details of their victims with other fraudsters, making students susceptible to repeated scams, including phishing attacks, financial frauds, and unsolicited offers.
5. Preventive Measures
- Verification of Internships:some text
- Always verify the authenticity of the internship by researching the company on official platforms such as LinkedIn, the company’s official website, and through trusted contacts or college placement cells.
- Avoid Upfront Payments:some text
- Employers do not ask for money in exchange for job or internship offers. If they demand for any kind of payment, then the employer is not original. Always question the necessity of such payments and consult trusted advisors before proceeding.
- Use Trusted Job Portals:some text
- Apply for internships through recognized platforms like LinkedIn, Internshala, or your college’s placement cell, which have verification processes to filter out fraudulent postings.
- Reporting Scams:some text
- Report suspicious offers to your college authorities, placement cells, and local cybercrime departments. Additionally, use platforms like Internshala’s “Report This Job” feature to flag fraudulent listings.
- Stay Educated and Updated:some text
- It is important to educate students by providing workshops, webinars, and awareness sessions on cybersecurity to stay informed and report about the latest scams.
6. Conclusion
Internship scams are a severe threat to the student society since they manipulate the student’s desire for an internship. The best ways to prevent such cons are by being cautious and receptive to whatever is being offered. Internship seekers, colleges and the placement cells have to work hand in hand to ensure that there is no fear among people seeking internships.
References
- Smith, J. (2024). Internship Scams on the Rise: How to Spot and Avoid Them. Retrieved from example1.com.
- Brown, A. (2023). Student Internship Scams in India: A Growing Concern. Retrieved from example2.com.
- Johnson, L. (2024). How to Protect Yourself from Fake Internship Offers. Retrieved from example3.com.
- Gupta, R. (2024). Social Media and the Rise of Job Scams. Retrieved from example4.com.

Executive Summary:
A post on X (formerly Twitter) featuring an image that has been widely shared with misleading captions, claiming to show men riding an elephant next to a tiger in Bihar, India. This post has sparked both fascination and skepticism on social media. However, our investigation has revealed that the image is misleading. It is not a recent photograph; rather, it is a photo of an incident from 2011. Always verify claims before sharing.

Claims:
An image purporting to depict men riding an elephant next to a tiger in Bihar has gone viral, implying that this astonishing event truly took place.

Fact Check:
After investigation of the viral image using Reverse Image Search shows that it comes from an older video. The footage shows a tiger that was shot after it became a man-eater by forest guard. The tiger killed six people and caused panic in local villages in the Ramnagar division of Uttarakhand in January, 2011.

Before sharing viral posts, take a brief moment to verify the facts. Misinformation spreads quickly and it’s far better to rely on trusted fact-checking sources.
Conclusion:
The claim that men rode an elephant alongside a tiger in Bihar is false. The photo presented as recent actually originates from the past and does not depict a current event. Social media users should exercise caution and verify sensational claims before sharing them.
- Claim: The video shows people casually interacting with a tiger in Bihar
- Claimed On:Instagram and X (Formerly Known As Twitter)
- Fact Check: False and Misleading


