Advisory for APS School Students
Pretext
The Army Welfare Education Society has informed the Parents and students that a Scam is targeting the Army schools Students. The Scamster approaches the students by faking the voice of a female and a male. The scamster asks for the personal information and photos of the students by telling them they are taking details for the event, which is being organised by the Army welfare education society for the celebration of independence day. The Army welfare education society intimated that Parents to beware of these calls from scammers.
The students of Army Schools of Jammu & Kashmir, Noida, are getting calls from the scamster. The students were asked to share sensitive information. Students across the country are getting calls and WhatsApp messages from two numbers, which end with 1715 and 2167. The Scamster are posing to be teachers and asking for the students’ names on the pretext of adding them to the WhatsApp Groups. The scamster then sends forms links to the WhatsApp groups and asking students to fill out the form to seek more sensitive information.
Do’s
- Do Make sure to verify the caller.
- Do block the caller while finding it suspicious.
- Do be careful while sharing personal Information.
- Do inform the School Authorities while receiving these types of calls and messages posing to be teachers.
- Do Check the legitimacy of any agency and organisation while telling the details
- Do Record Calls asking for personal information.
- Do inform parents about scam calling.
- Do cross-check the caller and ask for crucial information.
- Do make others aware of the scam.
Don’ts
- Don’t answer anonymous calls or unknown calls from anyone.
- Don’t share personal information with anyone.
- Don’t Share OTP with anyone.
- Don’t open suspicious links.
- Don’t fill any forms, asking for personal information
- Don’t confirm your identity until you know the caller.
- Don’t Reply to messages asking for financial information.
- Don’t go to a fake website by following a prompt call.
- Don’t share bank Details and passwords.
- Don’t Make payment over a prompt fake call.
Related Blogs

Introduction
China is on the verge of unveiling a new policy that will address how Artificial Intelligence (AI) influences employment. On January 27, 2026, the Ministry of Human Resources and Social Security (MOHRSS) announced it would publish a paper on the contribution of AI to the labour and employment markets. The policy will include provisions to help impacted industries, expand assistance to young workers and graduates, and come up with interdisciplinary training programmes to equip individuals with jobs in an AI-enabled economy. The authorities have stressed that AI does not kill jobs but changes them, and education will be needed to assist employees in adjusting to the changes.
This announcement reflects a more proactive policy on AI-based changes in labour, showing that China intends to sustain economic modernisation through AI, as well as social stability. It also depicts wider international issues concerning the rate of automation and the necessity of considering labour and training policy.
AI and the Changing Nature of Work
AI is transforming work content and nature in industries. AI systems enhance the productivity of various functions, including data processing, logistics, and customer service, although they alter the nature of tasks carried out by humans. Extant studies indicate that although AI can automate routine activities, new occupations that require complex thinking, management of artificial intelligence, and skills related to people, including empathy, creativity, and problem-solving, may be generated.
This is the key nuance in the policy framing of China. Authorities point out that AI does not always result in massive unemployment. Instead, it transforms jobs and necessitates workers to change to new task profiles. This perspective is in line with the recent reports of the world research organisations, which predict the effects of AI as transformational and not necessarily destructive. As an example, the World Economic Forum Future Jobs Report 2023 observes that the change in technology will introduce new jobs that were not there 10 years ago, and retraining and upskilling will be instrumental in accessing those opportunities.
Key Components of China’s Policy Response
China’s forthcoming policy is expected to focus on three main areas that address both current workforce needs and future readiness.
Support for Key Industries
The policy will offer targeted assistance to sectors where artificial intelligence is gaining pace. Industries like advanced manufacturing, high-tech services, and online logistics will also get specialised assistance to assist companies in using AI to complement human labour and not just to replace it. The Chinese government tries to balance industrial upgrading with employment by channelling resources to the growth areas.
Assistance for Youth and Graduates
The youth and the recent graduates are entering a labour market that is changing rapidly. The policy aims to increase the support services to this population by career counselling, internships, and training programmes correlated with changing employer demands. According to a study by McKinsey Global Institute, the young workforce all over the globe can face disproportionate disruption in case the prospects of training are scarce, making initial career backing imperative.
Interdisciplinary Talent Development
The Chinese strategy focuses on interdisciplinary training that blends knowledge of domains and AI literacy and digital illiteracy. This is indicative of the realisation that hybrid skills are required in the future. The Organisation for Economic Cooperation and Development suggests that workers who can make it through the technical and non-technical elements of work will stand a better chance of winning in the AI age.
These components show that China’s strategy is not simply to protect existing jobs but to help workers transition to roles that leverage AI’s strengths.
Economy, Stability and Strategic Modernisation
The policy is an attempt to control technological transition as part of wider economic planning. It is an indication that the government regards AI as a structural change rather than an external shock that can be predicted and influenced by policy.
This is in contrast to some other reactions to labour markets in other countries, where the reactionary approach has been seen as a reaction to the job losses that have already become reality. The initiative by China implies that there should be a change in the manner in which one can expect change instead of reacting to change.
Global Comparisons and Shared Challenges
Governments worldwide are testing the options to adapt to the work effects of AI. The European Union is considering the individual learning account and portable training benefits, which would assist workers to gain access to reskilling opportunities in the course of their careers. In the US, there is a concerted effort by the public-private partnerships to match the development of the workforce with technological implementation.
The strategy of China has some of these components, but it stands out due to its incorporation with national planning processes. China wants the adoption of AI to help it achieve the common good and not division by connecting the workforce policy to the overall innovation and economic purpose.
Meanwhile, the issue of balancing the supply of labour with the demand of technology is a challenge of its own to countries with older populations and relatively smaller working forces. The timing and design of policy are particularly significant in China, as there is a large labour force and continuous changes in demography.
Practical Challenges and Risks
The success of China’s emerging policy will depend on effective implementation. Several practical issues will require careful attention:
Ensuring Equitable Access to Training
The labour force in China is diversified, and it goes through technology zones in cities and other rural areas. It will be paramount to make sure that the opportunity of upskilling is extended to all workers across the spectrum to prevent the further worsening of regional inequalities. Research conducted on reskilling across the globe shows that rural and low-income groups tend to lack access to training, despite the availability of programmes.
Aligning Training with Labour Demand
The programme of upskilling should be related to the market requirements. Disconnected training is prone to resulting in the production of skills that are obsolete or not applicable in actual work settings. Experience in emerging economies indicates that the involvement of employers in the training design enhances placement success on the part of the learner.
Private Sector Participation
The policy needs to be translated into employment outcomes with the help of private companies. Incentives to make firms invest in worker training, internships, and apprenticeships will enable workers to shift to AI-augmented jobs with ease.
A Model for AI Workforce Policy
The Chinese policy can serve as an example for other countries that want to balance technological advancement and labour market security. It acknowledges the fact that the effect of AI on employment is not only a technical or an economic problem but also a social challenge. Through foregrounding training, support, and coordinated action, China aims to create a future where people are ready to change and not lose their jobs to this change.
This strategy can be agreed with the suggestions of international organisations like the World Bank and the OECD, which insist on the idea of lifelong learning and flexibility of labour markets, as well as proactive investment in human capital as the main aspects of the labour policy in the future.
Conclusion
Artificial intelligence will continue to reshape work around the world. China’s forthcoming policy, which emphasises support, training and strategic integration of AI into labour markets, reflects a proactive and holistic view of technological transition. Other countries could benefit from studying this approach, especially in terms of linking workforce development with innovation goals.
By anticipating disruption and investing in people as well as technology, policymakers can help ensure that AI becomes a driver of shared economic opportunity rather than a source of exclusion. The balance between innovation and employment will shape not only economic outcomes but also social cohesion in the years ahead.
References

Introduction
Freedom of speech and expression is fundamental to democracy and is constitutionally entrenched in Article 19(1)(a) of the Indian Constitution. The explosion of online spaces, brought about by the digital age, in the form of social media, blogs, and messaging apps, has reinterpreted how information is authored, disseminated, and consumed. This digital revolution has galvanised individuals to engage further inclusively in public debate, but has also fanatically magnified the risks of misinformation, hate speech, and threats to public order. Against this background, the judiciary is increasingly called upon to determine the limits of free speech, primarily where state regulation seeks to infringe upon constitutional protection.
Constitutional and Statutory Framework related to Freedom of Speech
The judiciary plays an integral role in balancing the fundamental right of freedom of speech with the regulation of online content, especially during the fast-paced evolution of the digital world. In India, with Article 19(1)(a) of the Constitution guaranteeing the freedom of speech, the courts bear the critical responsibility of protecting this liberty while recognising the State's legitimate interests in restricting harmful or unlawful content on a digital scale. This adjudicatory dilemma is even trickier because the said right has been held by the Supreme Court not to be an absolute one and is subject to "reasonable restrictions" as in Article 19(2), which recognises restrictions in the interest of sovereignty, security, public order, decency, and morality. Freedom of speech, being the cornerstone of democracy in India, does have an umbrella of reasonable restrictions under which the state can regulate any form of speech that infringes upon other equally compelling societal interests. However, with the coming of the internet and other digital communication arrangements, there was a need to develop new statutory instruments, i.e., Information Technology Act, 2000 (IT Act) and Rules made thereunder, including Information Technology (Intermediary Guidelines) and Digital Media Ethics Code Rules, 2021. These enactments attempt to regulate digital content, confronting issues such as hate speech, misinformation, and content that threatens public order. The judiciary's mandate is to interpret the enactments within the constitutional precincts, thus ensuring that the arbitrariness of State action is not aggravated or that the regulation is not overbroad. Judicial Landmark Decisions Affirming Balance The judiciary has played a front-ranking role in elaborating a jurisprudence protecting free speech in delineating legitimate regulation thereof. The Supreme Court judgment in Shreya Singhal v. Union of India, 2015, is seminal. Section 66A of the IT Act was struck down as it was vague and overly broad, causing a chilling effect on online speech. The Court has emphasised that any limitation on speech must be precise and fall strictly within the parameters laid down in Article 19(2). While the Court recognises that harmful online content needs to be addressed, the remedy must not encroach upon free political debate, satire, and criticism vital for democracy.
Following this, the Anuradha Bhasin case clarified the convergence of free speech and online access. The court held that the right to free speech had a vital medium in the form of the internet and that it would have to be an inevitable, proportionate shutdown, and transparent for challenge before the judiciary for any shutdown of the internet. This reaffirmed that restrictions on online speech must be rigorously tested.
Subsequent cases involve limitations on the 2021 IT Rules, whereby such government bodies can demand that “fake” or “misleading” material be taken off the internet. Courts move with circumspection, recognising the government's interest in fighting bogus information but remaining vigilant against over-regulation that can be code for pre-emptive censorship and threatening healthy discourses.
The virtual world raises particular and deeper questions: the viral nature of online speech multiplies its impact, distributing both democratic ideas and abusive material instantaneously. The courts recognise this twinning. While pressurising the legislature and executive to formulate clearer, more precise rules, courts simultaneously act as constitutional Guardians, avoiding breaches of the right with executive excess or vague laws. There is a strain between judicial activism, which promotes constitutional rights aggressively, and the fear of judicial paternalism, courts overreaching into policy arenas. But there is a need for vigilance by the judiciary due to the rapidly changing nature of digital technologies and threats to the freedoms of democracy. The judiciary continues to give contours to free speech and online regulation. There are enforcement issues, such as ongoing abuse of struck-down provisions, such as Section 66A, that the court counters with reaffirmation of constitutional directives. The evolving jurisprudence balances on thin stilts, upholding the democratic spirit of India by securing speech on online spaces and sanctioning reasonable, transparent moderation of harmful speech.
Conclusion
The Indian judiciary's leadership in balancing online content regulation with the freedom of speech is central and refined. The courts continually emphasise that speech on the digital medium is highly constitutionally protected and that restrictions must be legally valid, specific, essential, and proportionate. By classical decisions and constant review of new regulating actions, courts safeguard democratic participation in the digital public domain from unmeritorious censorship. Concurrently, the courts recognize the responsibility of the state in regulating digital ills such as mis recipe and hate speech, demanding parameters that uphold constitutional freedoms and the due process. The balancing act of the judiciary continues to be fundamental in defining India's digital democracy so that free speech can thrive even as the state upholds public order and human dignity in the digital communication age.
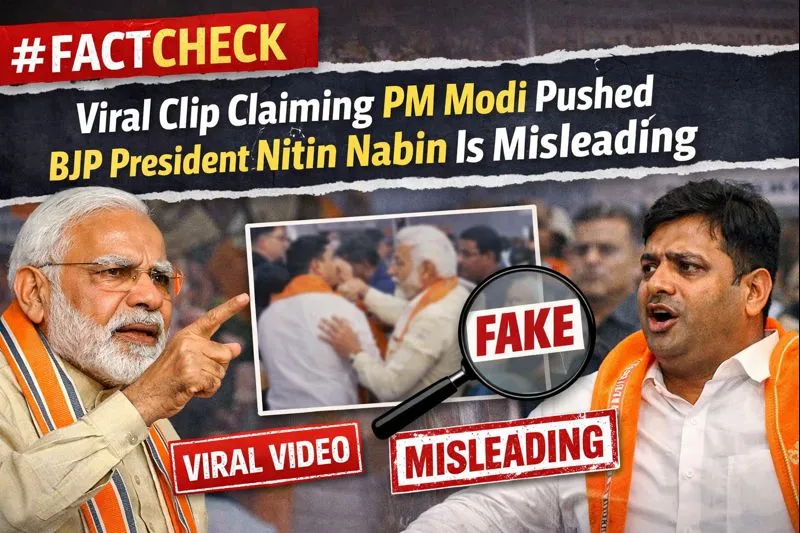
Executive Summary:
A video clip featuring Prime Minister Narendra Modi and the newly elected Bharatiya Janata Party (BJP) national president, Nitin Nabin, is going viral on social media. In the clip, PM Modi is seen apparently pushing Nitin Nabin, prompting claims that Nabin had accidentally stepped between the Prime Minister and the camera, after which Modi allegedly pushed him out of the frame. CyberPeace’s research found that the viral clip is misleading and cropped. The original, unedited video shows Prime Minister Modi gesturing for Nitin Nabin to move ahead and offer floral tributes to the statues of Bharatiya Jana Sangh founder Syama Prasad Mukherjee and Pandit Deendayal Upadhyaya at the BJP headquarters in Delhi. It is pertinent to note that on 20 January 2026, BJP leader Nitin Nabin was elected as the party’s national president. Several senior BJP leaders, including Prime Minister Narendra Modi, were present at the event. During his address, PM Modi remarked, “Nitin Nabin ji is my boss, and I am a party worker.” The statement received widespread attention, following which multiple videos linking to the remark began circulating on social media. A Facebook user shared the viral clip with a Hindi caption alleging that despite calling himself a “party worker,” PM Modi pushed his “boss” out of the camera frame. The post further mocked the position of BJP president, claiming it to be merely ceremonial. (Archived link)
To verify the claim, we conducted a reverse image and video search, which led us to a longer version of the video uploaded on news agency INS’s official X handle on 20 January 2026. The caption stated that PM Modi, BJP president Nitin Nabin, Defence Minister Rajnath Singh, Home Minister Amit Shah, Union Minister Nitin Gadkari and senior leader J.P. Nadda paid tributes to Syama Prasad Mukherjee and Pandit Deendayal Upadhyaya at the BJP headquarters.
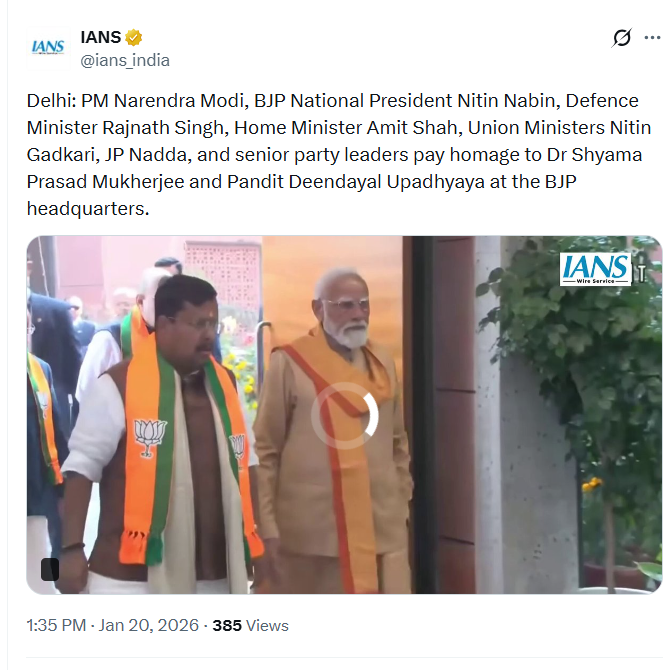
In the full video, PM Modi and Nitin Nabin are seen walking together. PM Modi then requests Nitin Nabin to proceed first for the floral tribute, placing his hand on Nabin’s back as a gesture to move forward. The viral clip selectively cuts this moment out of context and loops it to create a misleading impression. The complete footage clearly shows that PM Modi asked Nitin Nabin to offer tributes first, after which other leaders followed. There is no indication whatsoever that Nitin Nabin was pushed out of the camera frame, as claimed in the viral posts. We also found the live broadcast of the ‘Bharatiya Janata Party Sangathan Parv’ on BJP’s official YouTube channel. The same visuals appear at the end of the live stream, further confirming that PM Modi was merely gesturing for Nitin Nabin to proceed first.
Additionally, photographs available on Nitin Nabin’s official X handle show him offering floral tributes ahead of PM Modi, who is seen standing behind and waiting.

Conclusion:
CyberPeace research confirms that the viral clip has been cropped and shared with a false narrative. In the original context, Prime Minister Narendra Modi was respectfully inviting BJP national president Nitin Nabin to move ahead and pay tributes, not pushing him out of the camera frame.


