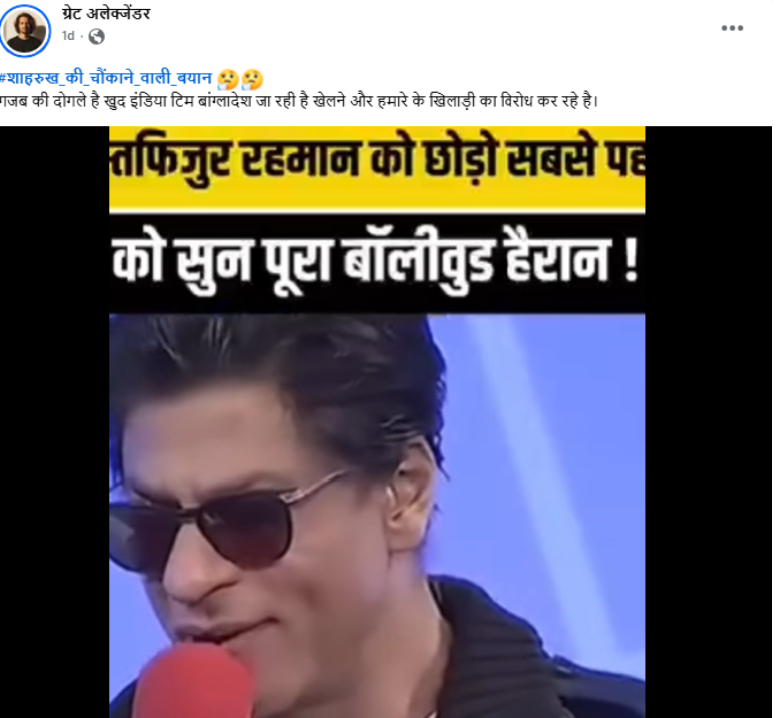
#FactCheck - Viral Video of Shah Rukh Khan Is AI-Generated; Users Sharing Misleading Claims
A video of Bollywood actor and Kolkata Knight Riders (KKR) owner Shah Rukh Khan is going viral on social media. The video claims that Shah Rukh Khan is reacting to opposition against Bangladeshi bowler Mustafizur Rahman playing for KKR and is allegedly calling industrialist Gautam Adani a “traitor,” while appealing to stop Hindu–Muslim politics.
Research by the CyberPeace Foundation found that the voice heard in the video is not Shah Rukh Khan’s but is AI-generated. Shah Rukh Khan has not made any official statement regarding Mustafizur Rahman’s removal from KKR. The claim made in the video concerning industrialist Gautam Adani is also completely misleading and baseless.
Claim
In the viral video, Shah Rukh Khan is allegedly heard saying: “People barking about Mustafizur Rahman playing for KKR should stop it. Adani is earning money by betraying the country by supplying electricity from India to Bangladesh. Leave Hindu–Muslim politics and raise your voice against traitors like Adani for the welfare of the country. Mustafizur Rahman will continue to play for the team.”
The post link, archive link, and screenshots can be seen below:
- Archive link: https://archive.is/XsQXp
- Facebook reel link: https://www.facebook.com/reel/1220246633365097
Research
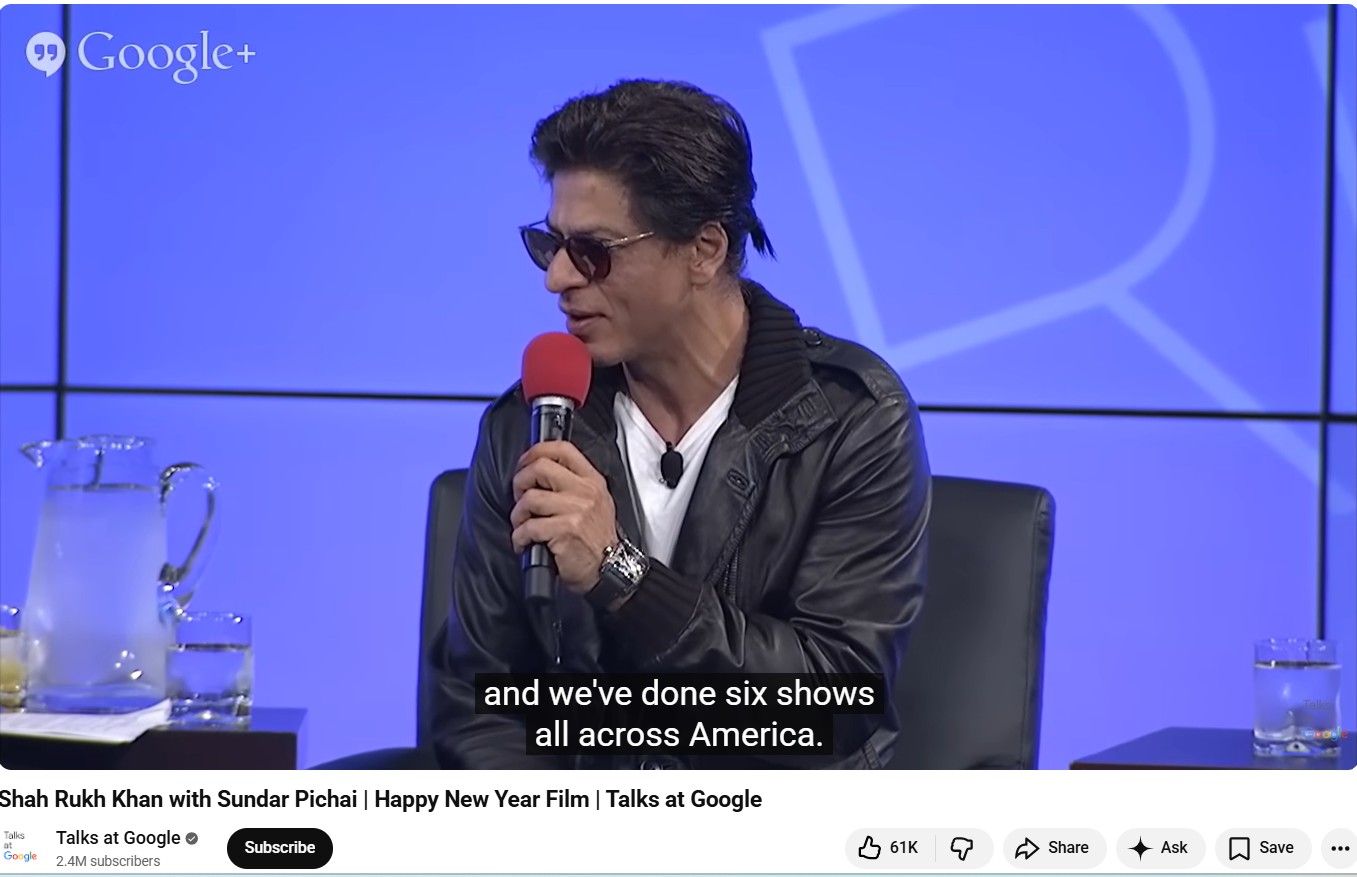
We examined the key frames of Shah Rukh Khan’s viral video using Google Lens. During this process, we found the original video on the official YouTube channel Talks at Google, which was uploaded on 2 October 2014.
In this video, Shah Rukh Khan is seen wearing the same outfit as in the viral clip. He is seen responding to questions from Google CEO Sundar Pichai. The YouTube video description mentions that Shah Rukh Khan participated in a fireside chat held at the Googleplex, where he answered Pichai’s questions and also promoted his upcoming film “Happy New Year.”
The link to the video is given : https://www.youtube.com/watch?v=H_8UBv5bZo0
Upon closely analyzing the viral video of Shah Rukh Khan, we noticed a clear mismatch between his voice and lip movements (lip sync). Such inconsistencies usually appear when the original video or its audio has been tampered with.
We then examined the audio present in the video using the AI detection tool Aurigin. According to the tool’s results, the audio in the viral video was found to be approximately 99 percent AI-generated.
Conclusion
Our research confirmed that the voice heard in the video is not Shah Rukh Khan’s but is AI-generated. Shah Rukh Khan has not made any official comment regarding Mustafizur Rahman’s removal from KKR. Additionally, the claims made in the video about industrialist Gautam Adani are completely misleading and baseless.
Related Blogs

According to Statista, the number of users in India's digital assets market is expected to reach 107.30m users by 2025 (Impacts of Inflation on Financial Markets, August 2023). India's digital asset market has been experiencing exponential growth fueled by the increased adoption of cryptocurrencies and blockchain technology. This furthers the need for its regulation. Digital assets include cryptocurrencies, NFTs, asset-backed tokens, and tokenised real estate.
India has defined Digital Assets under Section 47(A) of the Income Tax Act, 1961. The Finance Act 2022-23 has added the word 'virtual' to make it “Virtual Digital Assets”. A “virtual digital asset” is any information or code, number, or token, created through cryptographic methods or otherwise, by any name, giving a digital representation of value exchanged with or without consideration. A VDA should contain an inherent value and represent a store of value or unit of account, functional in any financial transaction or investment. These can be stored, transferred, or traded in electronic format.
Digital Asset Governance: Update and Future Outlook
Indian regulators have been conservative in their approach towards digital assets, with the Reserve Bank of India first issuing directions against cryptocurrency transactions in 2018. This ban was removed by the Supreme Court through a court order in 2020. The presentation of the Cryptocurrency and Regulation of Official Digital Currency Bill of 2021 is a fairly important milestone in its attempts to lay down the framework for issuing an official digital currency by the Reserve Bank of India. While some digital assets seem to have potential, like the Central Bank Digital Currencies (CBDCs) and blockchain-based financial applications, a blanket prohibition has been enforced on private cryptocurrencies.
However, in more recent trends, the landscape is changing as the RBI's CBDC is to provide a state-backed digital alternative to cash under a more structured regulatory framework. This move seeks to balance state control with innovation on investor safety and compliance, expecting to reduce risk and enhance security for investors by enacting strict anti-money laundering and know-your-customer laws. Highlighting these developments is important to examine how global regulatory trends influence India's digital asset policies.
Impact of Global Development on India’s Approach
Global regulatory developments have an impact on Indian policies on digital assets. The European Union's Markets in Crypto-assets (MiCA) is to introduce a comprehensive regulatory framework for cryptocurrencies that could act as an inspiration for India. MiCA regulation covers crypto-assets that are not currently regulated by existing financial services legislation. Its particular focus on consumer protection and market integrity resonates with India in terms of investigating needs related to digital assets, including fraud and price volatility. Additionally, evolving policies in the US, such as regulating crypto exchanges and classifying certain tokens as securities, could also form the basis for India's regulatory posture.
Collaboration on the international level is also a chief contributing factor. India’s regular participation in global forums like the G20, facilitates an opportunity to align its regulations on digital assets with other countries, tending toward an even more standardised and predictable framework for cross-border transactions. This can significantly help India given that the nation has a huge diaspora providing a critical inflow of remuneration.
CyberPeace Outlook
Though digital assets offer many opportunities to India, challenges also exist. Cryptocurrency volatility affects investors, posing concerns over fraud and illicit dealings. A balance between the need for innovation and investor protection is paramount to avoid killing the growth of India's digital asset ecosystem with overly restrictive regulations.
Financial inclusion, efficient cross-border payments with low transaction costs, and the opening of investment opportunities are a few opportunities offered by digital assets. For example, the tokenisation of real estate throws open real estate investment to smaller investors. To strengthen the opportunities while addressing challenges, some policy reforms and new frameworks might prove beneficial.
CyberPeace Policy Recommendations
- Establish a regulatory sandbox for startups working in the area of blockchain and digital assets. This would allow them to test innovative solutions in a controlled environment with regulatory oversight minimising risks.
- Clear guidelines for the taxation of digital assets should be provided as they will ensure transparency, reduce ambiguity for investors, and promote compliance with tax regulations. Specific guidelines can be drawn from the EU's MiCA regulation.
- Workshops, online resources, and campaigns are some examples of initiatives aimed at improving consumer awareness about digital assets, benefits and associated risks that should be implemented. Partnerships with global fintech firms will provide a great opportunity to learn best practices.
Conclusion
India is positioned at a critical juncture with respect to the debate on digital assets. The challenge which lies ahead is one of balancing innovation with effective regulation. The introduction of the Central Bank Digital Currency (CBDC) and the development of new policies signal a willingness on the part of the regulators to embrace the digital future. In contrast, issues like volatility, fraud, and regulatory compliance continue to pose hurdles. By drawing insights from global frameworks and strengthening ties through international forums, India can pave the way for a secure and dynamic digital asset ecosystem. Embracing strategic measures such as regulatory sandboxes and transparent tax guidelines will not only protect investors but also unlock the immense potential of digital assets, propelling India into a new era of financial innovation and inclusivity.
References
- https://www.weforum.org/agenda/2024/10/different-countries-navigating-uncertainty-digital-asset-regulation-election-year/
- https://www.acfcs.org/eu-passes-landmark-crypto-regulation
- https://www.indiabudget.gov.in/budget2022-23/doc/Finance_Bill.pdf
- https://www.weforum.org/agenda/2024/10/different-countries-navigating-uncertainty-digital-asset-regulation-election-year/
- https://www3.weforum.org/docs/WEF_Digital_Assets_Regulation_2024.pdf

Executive Summary:
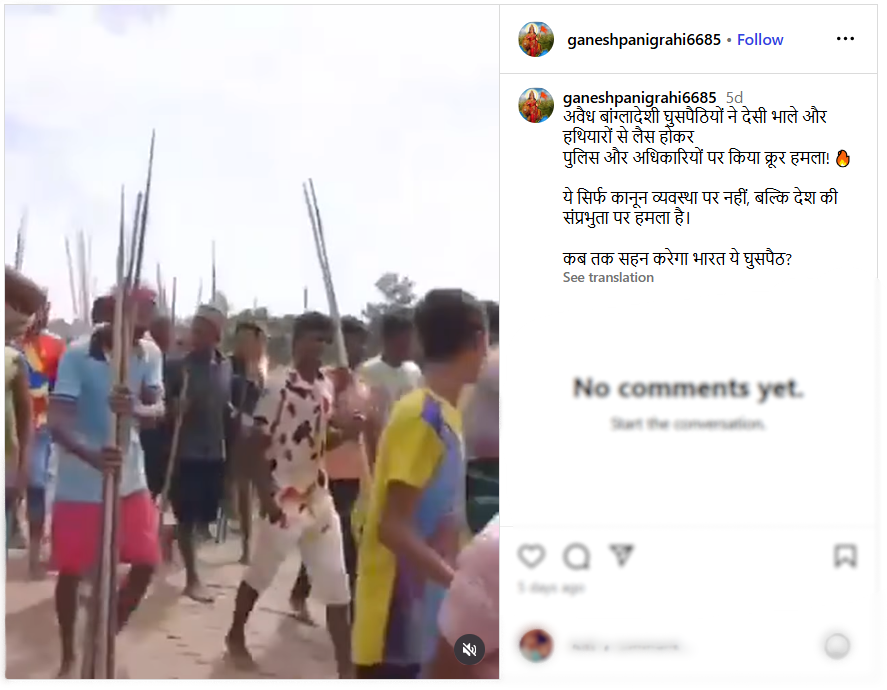
As we researched a viral social media video we encountered, we did a comprehensive fact check utilizing reverse image search. The video circulated with the claim that it shows illegal Bangladeshi in Assam's Goalpara district carrying homemade spears and attacking a police and/or government official. Our findings are certain that this claim is false. This video was filmed in the Kishoreganj district, Bangladesh, on July 1, 2025, during a political argument involving two rival factions of the Bangladesh Nationalist Party (BNP). The footage has been intentionally misrepresented, putting the report into context regarding Assam to disseminate false information.

Claim:
The viral video shows illegal Bangladeshi immigrants armed with spears marching in Goalpara, Assam, with the intention of attacking police or officials.
Fact Check:
To establish if the claim was valid, we performed a reverse image search on some of the key frames from the video. We did our research on a number of news articles and social media posts from Bangladeshi sources. This led us to a reality check as the events confirmed in these reports took place in Ashtagram, Kishoreganj district, Bangladesh, in a violent political confrontation between factions of the Bangladesh Nationalist Party (BNP) on July 1, 2025, that ultimately resulted in about 40 injuries.
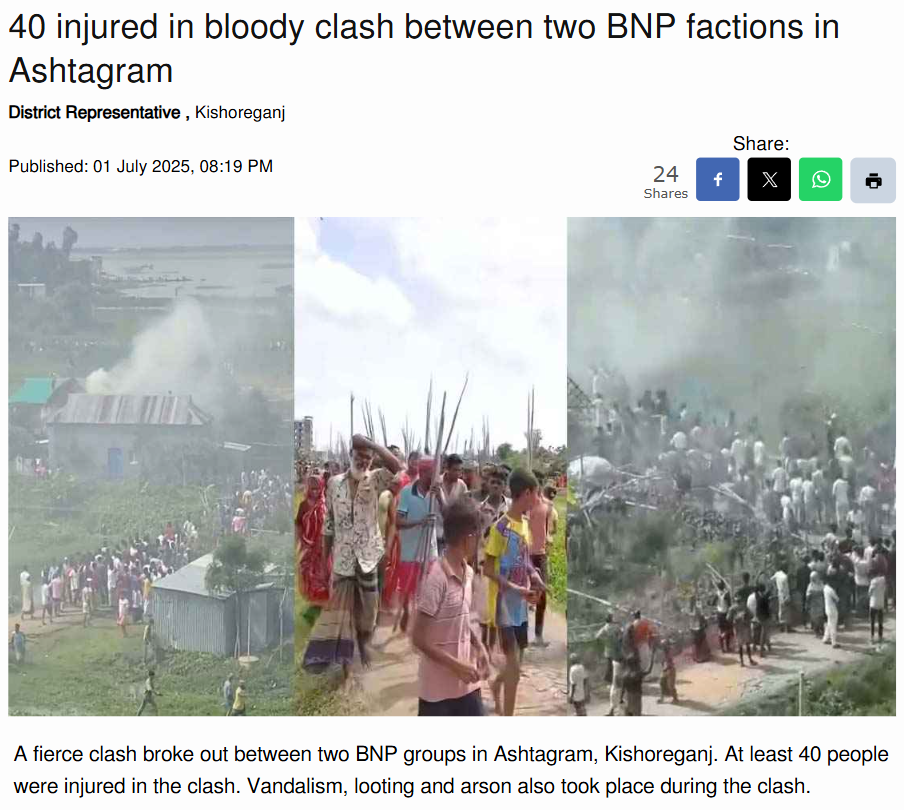
We also found on local media, in particular, Channel i News reported full accounts of the viral report and showed images from the video post. The individuals seen in the video were engaged in a political fight and wielding makeshift spears rather than transitioning into a cross-border attack. The Assam Police issued an official response on X (formerly Twitter) that denied the claim, while noting that nothing of that nature occurred in Goalpara nor in any other district of Assam.
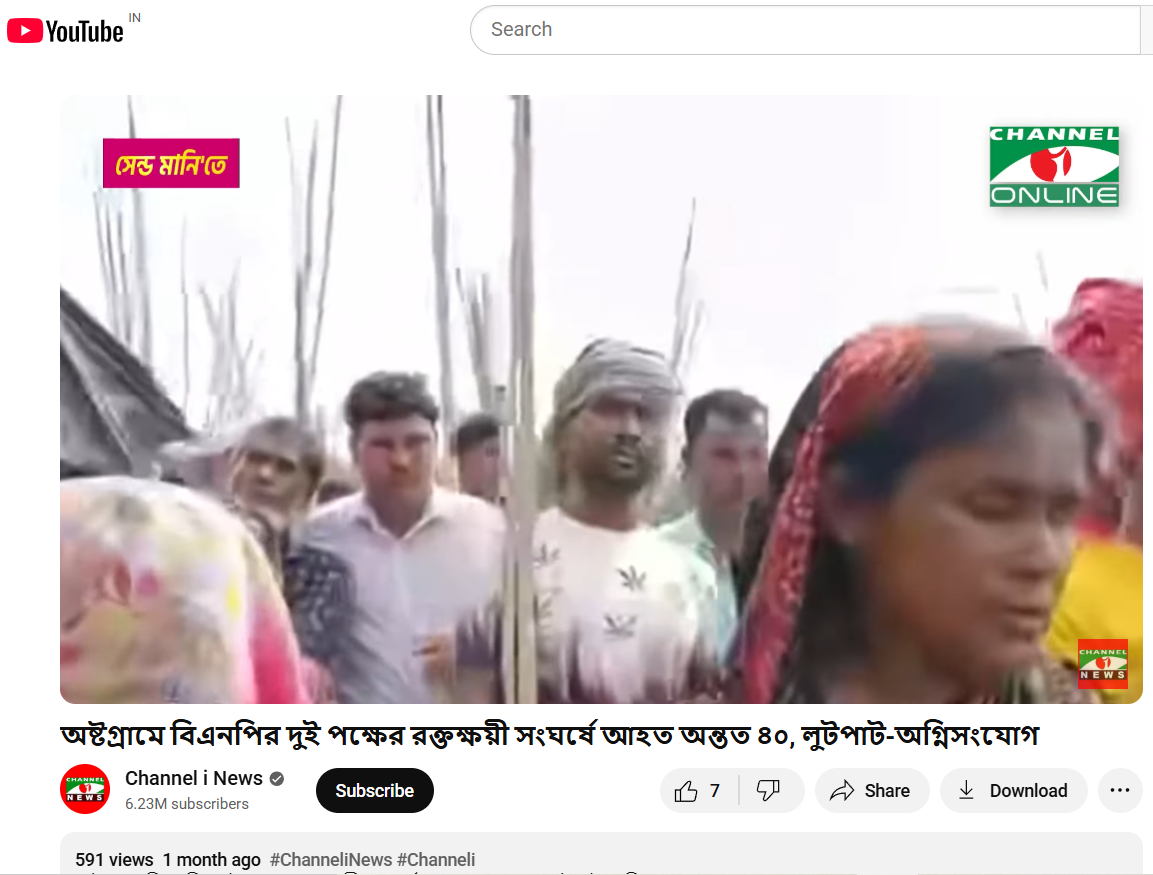
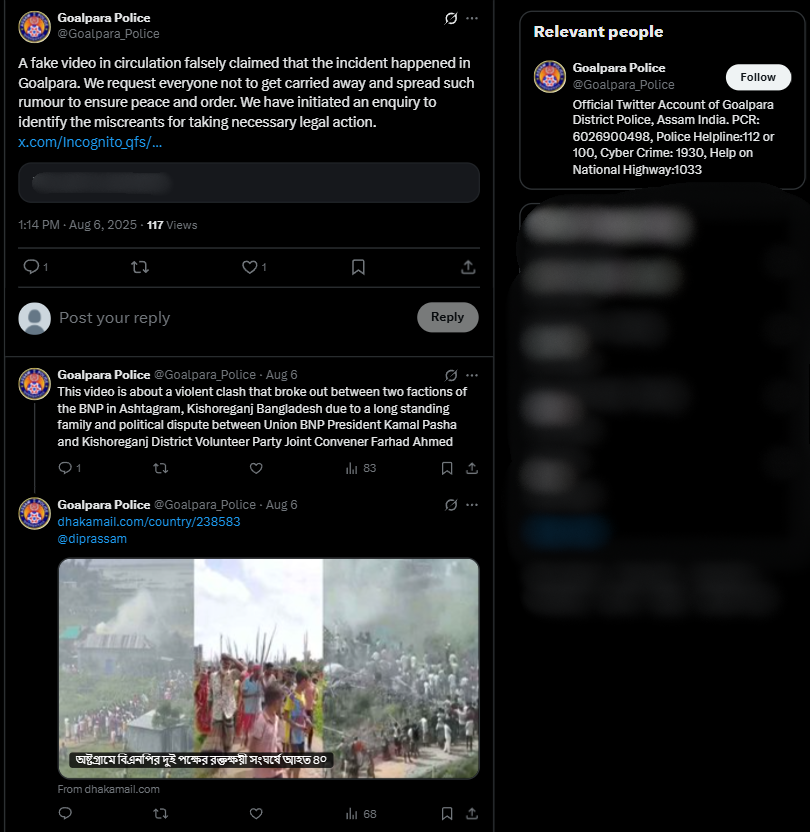
Conclusion:
Based on our research, we conclude that the viral video does not show unlawful Bangladeshi immigrants in Assam. It depicts a political clash in Kishoreganj, Bangladesh, on July 1, 2025. The claim attached to the video is completely untrue and is intended to mislead the public as to where and what the incident depicted is.
Claim: Video shows illegal migrants with spears moving in groups to assault police!
Claimed On: Social Media
Fact Check: False and Misleading
.webp)
Introduction
The Senate bill introduced on 19 March 2024 in the United States would require online platforms to obtain consumer consent before using their data for Artificial Intelligence (AI) model training. If a company fails to obtain this consent, it would be considered a deceptive or unfair practice and result in enforcement action from the Federal Trade Commission (FTC) under the AI consumer opt-in, notification standards, and ethical norms for training (AI Consent) bill. The legislation aims to strengthen consumer protection and give Americans the power to determine how their data is used by online platforms.
The proposed bill also seeks to create standards for disclosures, including requiring platforms to provide instructions to consumers on how they can affirm or rescind their consent. The option to grant or revoke consent should be made available at any time through an accessible and easily navigable mechanism, and the selection to withhold or reverse consent must be at least as prominent as the option to accept while taking the same number of steps or fewer as the option to accept.
The AI Consent bill directs the FTC to implement regulations to improve transparency by requiring companies to disclose when the data of individuals will be used to train AI and receive consumer opt-in to this use. The bill also commissions an FTC report on the technical feasibility of de-identifying data, given the rapid advancements in AI technologies, evaluating potential measures companies could take to effectively de-identify user data.
The definition of ‘Artificial Intelligence System’ under the proposed bill
ARTIFICIALINTELLIGENCE SYSTEM- The term artificial intelligence system“ means a machine-based system that—
- Is capable of influencing the environment by producing an output, including predictions, recommendations or decisions, for a given set of objectives; and
- 2. Uses machine or human-based data and inputs to
(i) Perceive real or virtual environments;
(ii) Abstract these perceptions into models through analysis in an automated manner (such as by using machine learning) or manually; and
(iii) Use model inference to formulate options for outcomes.
Importance of the proposed AI Consent Bill USA
1. Consumer Data Protection: The AI Consent bill primarily upholds the privacy rights of an individual. Consent is necessitated from the consumer before data is used for AI Training; the bill aims to empower individuals with unhinged autonomy over the use of personal information. The scope of the bill aligns with the greater objective of data protection laws globally, stressing the criticality of privacy rights and autonomy.
2. Prohibition Measures: The proposed bill intends to prohibit covered entities from exploiting the data of consumers for training purposes without their consent. This prohibition extends to the sale of data, transfer to third parties and usage. Such measures aim to prevent data misuse and exploitation of personal information. The bill aims to ensure companies are leveraged by consumer information for the development of AI without a transparent process of consent.
3. Transparent Consent Procedures: The bill calls for clear and conspicuous disclosures to be provided by the companies for the intended use of consumer data for AI training. The entities must provide a comprehensive explanation of data processing and its implications for consumers. The transparency fostered by the proposed bill allows consumers to make sound decisions about their data and its management, hence nurturing a sense of accountability and trust in data-driven practices.
4. Regulatory Compliance: The bill's guidelines call for strict requirements for procuring the consent of an individual. The entities must follow a prescribed mechanism for content solicitation, making the process streamlined and accessible for consumers. Moreover, the acquisition of content must be independent, i.e. without terms of service and other contractual obligations. These provisions underscore the importance of active and informed consent in data processing activities, reinforcing the principles of data protection and privacy.
5. Enforcement and Oversight: To enforce compliance with the provisions of the bill, robust mechanisms for oversight and enforcement are established. Violations of the prescribed regulations are treated as unfair or deceptive acts under its provisions. Empowering regulatory bodies like the FTC to ensure adherence to data privacy standards. By holding covered entities accountable for compliance, the bill fosters a culture of accountability and responsibility in data handling practices, thereby enhancing consumer trust and confidence in the digital ecosystem.
Importance of Data Anonymization
Data Anonymization is the process of concealing or removing personal or private information from the data set to safeguard the privacy of the individual associated with it. Anonymised data is a sort of information sanitisation in which data anonymisation techniques encrypt or delete personally identifying information from datasets to protect data privacy of the subject. This reduces the danger of unintentional exposure during information transfer across borders and allows for easier assessment and analytics after anonymisation. When personal information is compromised, the organisation suffers not just a security breach but also a breach of confidence from the client or consumer. Such assaults can result in a wide range of privacy infractions, including breach of contract, discrimination, and identity theft.
The AI consent bill asks the FTC to study data de-identification methods. Data anonymisation is critical to improving privacy protection since it reduces the danger of re-identification and unauthorised access to personal information. Regulatory bodies can increase privacy safeguards and reduce privacy risks connected with data processing operations by investigating and perhaps implementing anonymisation procedures.
The AI consent bill emphasises de-identification methods, as well as the DPDP Act 2023 in India, while not specifically talking about data de-identification, but it emphasises the data minimisation principles, which highlights the potential future focus on data anonymisation processes or techniques in India.
Conclusion
The proposed AI Consent bill in the US represents a significant step towards enhancing consumer privacy rights and data protection in the context of AI development. Through its stringent prohibitions, transparent consent procedures, regulatory compliance measures, and robust enforcement mechanisms, the bill strives to strike a balance between fostering innovation in AI technologies while safeguarding the privacy and autonomy of individuals.
References:
- https://fedscoop.com/consumer-data-consent-training-ai-models-senate-bill/#:~:text=%E2%80%9CThe%20AI%20CONSENT%20Act%20gives,Welch%20said%20in%20a%20statement
- https://www.dataguidance.com/news/usa-bill-ai-consent-act-introduced-house#:~:text=USA%3A%20Bill%20for%20the%20AI%20Consent%20Act%20introduced%20to%20House%20of%20Representatives,-ConsentPrivacy%20Law&text=On%20March%2019%2C%202024%2C%20US,the%20U.S.%20House%20of%20Representatives
- https://datenrecht.ch/en/usa-ai-consent-act-vorgeschlagen/
- https://www.lujan.senate.gov/newsroom/press-releases/lujan-welch-introduce-billto-require-online-platforms-receive-consumers-consent-before-using-their-personal-data-to-train-ai-models/


